Global radios depend on the TETRA (Terrestrial Trunked Radio) standard, however a number of vulnerabilities have been found that have an influence on its use in Europe, the UK, and other countries. These issues include the following:-
Institutions of the state, Law enforcement, Organizations that provide emergency assistance, Institutions of the military

The encryption and the implementation of it were found to have all of these flaws, which allowed for the communication to be decrypted. Midnight Blue, a security company with headquarters in the Netherlands, has discovered five flaws in the Terrestrial Trunked Radio (TETRA) system.
All TETRA radio networks are believed to be vulnerable to the problems, which have been given the name TETRA:BURST. They provide the possibility for an adversary to decode communications in real time or after the fact, to insert messages, to deanonymize users, or to change the session key to zero in order to engage in uplink interception.
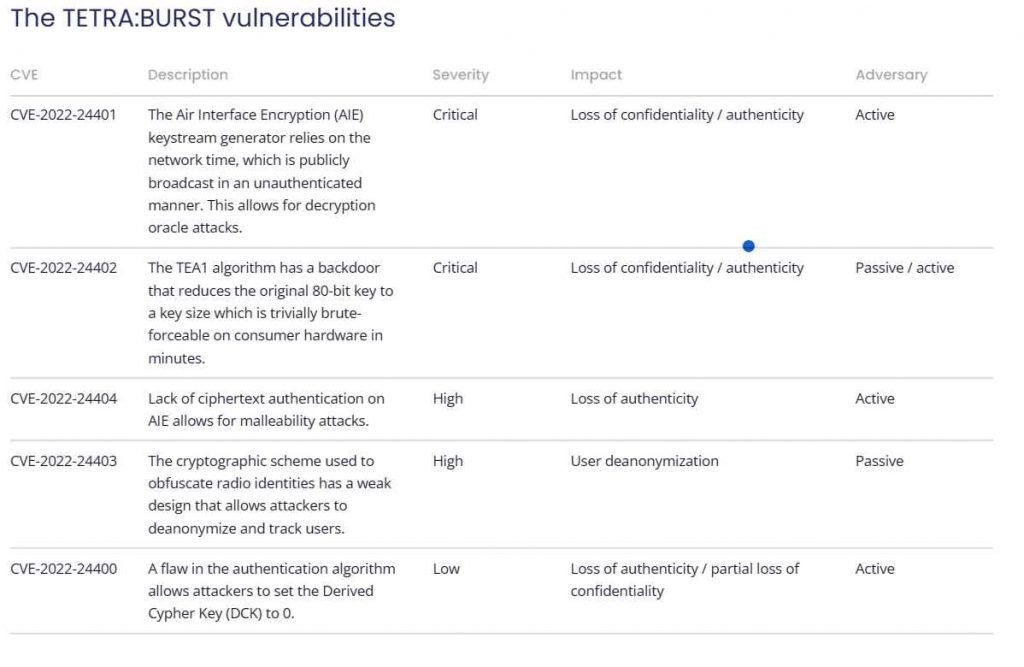
Two of the issues are considered to be of vital importance. The first vulnerability, identified as CVE-2022-24401, is referred to be an oracle decryption attack, and it is capable of exposing text, voice, or data transmission. Because the Air Interface Encryption (AIE) keystream generator depends on network time, which is broadcast openly and without encryption, this is made possible.
The second flaw, known as CVE-2022-24402, is an engineering flaw. According to the researchers, the TEA1 encryption method “has a backdoor that reduces the original 80-bit key to a key size which is trivially brute-forceable on consumer hardware in minutes.”
CVE-2022-24404 is a high-severity vulnerability that arises from a lack of ciphertext authentication on the AIE that enables a malleability attack. CVE-2022-24403 is a high-severity vulnerability that allows radio identities to be identified and tracked due to weak cryptographic design. CVE-2022-24400 is a low-severity vulnerability that allows confidentially to be partially compromised through a flawed authentication algorithim. These three vulnerabilities are less severe.
The Midnight Blue team maintains that the “backdoor,” as they refer to it, is the result of intentional choices made during the algorithm’s construction. It is likely that this was done in order to facilitate the export of the encryption technology; in accordance with a number of laws and regulations, it is sometimes necessary to reduce the level of security .
After an extended and covert disclosure procedure that was funded by the NLnet Foundation, Midnight Blue will present their results at the Black Hat conference in August.
In 1995, ETSI launched TETRA, which was subsequently used by Motorola and Airbus. Because it makes use of “secret, proprietary cryptography,” establishing its security may be difficult.
The researchers purchased a TETRA-powered radio from eBay, found flaws in it, and extracted the cryptographic ciphers. This led to the development of TETRA:BURST and the “secret reduction step” in TEA1, which made it possible to decode communications using inexpensive hardware.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











