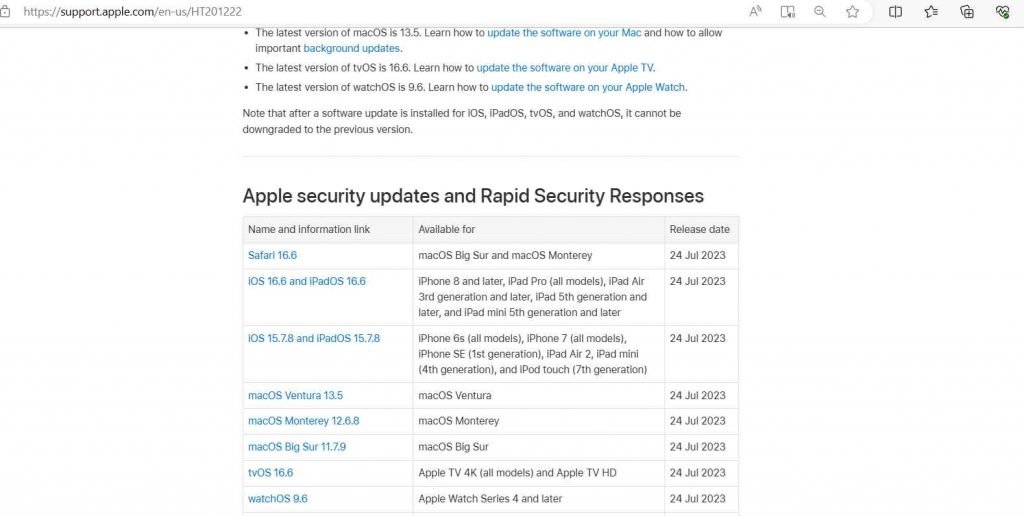
Recent news reports have brought attention to two serious zero-day vulnerabilities that pose a risk to the digital security of Apple products sold in every region of the world. Both of these vulnerabilities, which have been given the CVE identifiers CVE-2023-37450 and CVE-2023-38606, were found to be present in Apple’s WebKit browser engine and kernel component for several platforms. Both vulnerabilities have been actively exploited, which makes it imperative that quick attention be paid to these security flaws. WebKit has a security vulnerability that has been identified as CVE-2023-37450. If exploited, this vulnerability might enable malicious actors to execute arbitrary code on susceptible devices, giving them control of such devices. The attack begins when a victim visits a malicious website without their knowledge while using a device that has already been infected. The iPhone 8 and subsequent models, as well as all versions of the iPad Pro, iPad Air (3rd generation and later), iPad 5th generation and later, and iPad mini 5th generation and later, are included in the list of impacted devices. MacOS Ventura is also involved. A researcher who wishes to remain nameless discovered and reported this problem.
As a direct reaction to this vulnerability, Apple has strengthened its security mechanism against it by including more checks with iOS 16.6, iPadOS 16.6, and macOS Ventura 13.5. In spite of this, the corporation continues to exercise extreme caution, admitting in its security warnings that there is evidence suggesting that this vulnerability may have been actively exploited. The business disclosed this information in security warnings that described the vulnerability. “Apple is aware of a report that this issue may have been actively exploited,” the company said.
A Kernel Zero-Day Bug with the Identifier CVE-2023-38606
Experts from Kaspersky discovered the second vulnerability, which was given the identifier CVE-2023-38606. If this kernel issue were exploited, it would allow attackers to “modify sensitive kernel state” on iPhones and Macs, which would give them the ability to possibly take control of these devices. The technology giant disclosed this information in security advisories explaining the vulnerability. “Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.7.1,” the firm said.
The danger affects a broad variety of Apple products, such as the macOS Big Sur, Monterey, and Ventura operating systems, as well as all iPhone models beginning with the iPhone 6s and moving forward. All versions of the iPad Pro, iPad Air starting with the 3rd generation, iPad starting with the 5th generation, iPad mini starting with the 5th generation, and the iPod touch starting with the 7th generation are all susceptible.
Apple has strengthened its state management in response to this vulnerability, which the company discovered very quickly. On the other hand, the tech giant has issued a warning that versions of iOS that were launched prior to iOS 15.7.1 may have been vulnerable to this bug.
In order for users to defend themselves against these attacks, it is strongly recommended that they upgrade their devices to the most recent versions of iOS, iPadOS, and macOS as quickly as they can.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











