Sysdig, a company that specializes in cybersecurity intelligence, uncovered a sophisticated hacking operation known as Scarleteel in February. Since then, Scarleteel has refined both its infection and exfiltration techniques and moved into phase two. Recent operations by Scarleteel have targeted settings such as AWS Fargate and Kubernetes, which indicates a clear shift from just crypto mining to additional exploitation such as the theft of intellectual rights. During the most recent attack, Scarleteel was seen taking advantage of a small flaw in the AWS policy in order to increase its privileges to administrator access and seize control of the Fargate account. Through this vulnerability, Kubernetes seemed to be the subject of more attacks. This gave the attacker the ability to exploit several Jupyter Notebook containers that were deployed in a Kubernetes cluster, which in turn gave them the ability to continue with numerous sorts of attacks, the primary one of which was to steal AWS credentials in order to further exploit the victim’s AWS environment.
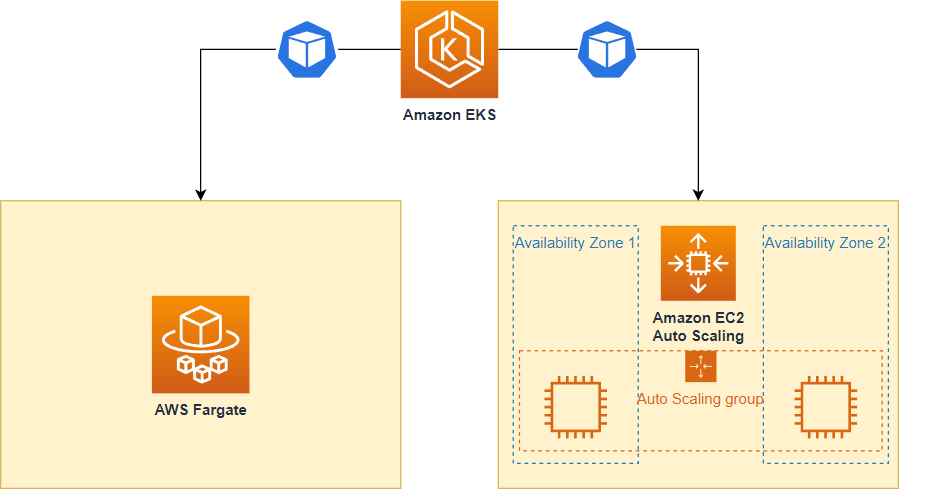
The goal of Scarleteel is to gain persistence in a vulnerable Kubernetes workload in order to elevate cloud privileges and ultimately cause financial damage through crypto-jacking as well as theft of intellectual property. A single vulnerable web application, or in the case of Scarleteel, a Jupyter Notebook, can lead to the complete compromise of an Amazon Web Services account.
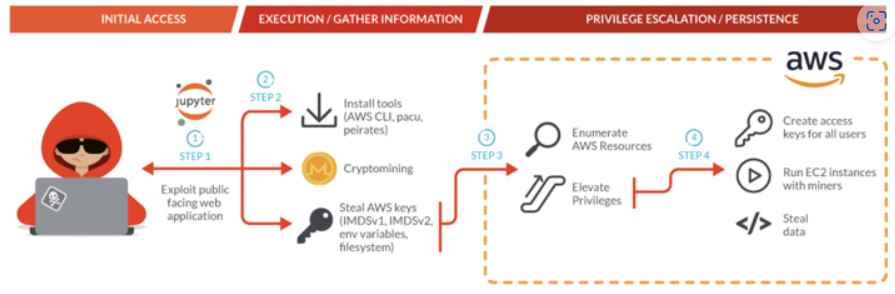
The scripts that were utilized in the attacks to steal information seemed to be aware that they were running in a container that was hosted by Fargate, since they carried out the appropriate instructions to gather credentials.
Their scripts communicate with a variety of services in order to collect information about the environment. After that, they proceed with their attack by using tools that are targeted for certain services (for example, peirates in Kubernetes pods or pacu after gaining AWS credentials). Popular open source attack tools like as Pacu and Peirates are frequently used by penetration testers and red teams in order to evaluate the level of security provided by current cloud and Kubernetes architecture. As a post-exploitation enumeration tool, Pacu was used in the Scarleteel attack. This allowed the attacker to quickly analyze the victim’s AWS account for more than 20 existing privilege escalation avenues. Peirates, on the other hand, provides attackers with an all-in-one command line interface that enables them to carry out Kubernetes attacks such as acquiring persistence via a reverse shell, performing lateral movement, or stealing cloud IAM credentials.
To avoid being discovered, Scarleteel used a cutting-edge method of exfiltration as well. It decided to use shell built-ins instead of the more popular command-line tools such as “curl” or “wget,” which is a stealthier approach to evade cloudtrail logs. Because Scarleteel employs shell built-ins to execute network external calls to IP addresses controlled by the attacker, the attack will look “normal” to most simple security monitoring solutions that make use of pre-built signatures. The malicious actor also utilized the compromised AWS Command Line Interface (CLI) to download and run Pandora, a piece of malware that is a part of the Mirai Botnet and that mainly targets internet-connected IoT devices in order to carry out large-scale DDoS operations. Before you can make your environment more resistant to an entity such as ScarletEel, you will first need to take certain precautions to stop potential attackers from getting inside. However, if they still manage to accomplish so despite your best efforts, you will need to put in place reliable runtime security. This is because the attackers are becoming more smart.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










