Group that engages in hacking and denial of service attacks Anonymous Sudan claims that it has information stolen from 30 million user accounts on Microsoft’s platform. The assertions have been refuted by Microsoft.
At the beginning of this month, the hacking gang made the claim that it successfully attacked Microsoft and obtained a database that held information on more than 30 million Microsoft accounts, including passwords. They also claimed that they obtained the database.
The information was advertised for sale on a Telegram channel by the gang, which is requesting a price of $50,000 for the whole database. The post contains a sample of the data, which consists of one hundred credential pairings; nevertheless, the data cannot be connected to the purported attack.
The following statement was released by the organization: “We announce that we have successfully hacked Microsoft and have access to a large database containing more than 30 million Microsoft accounts, email, and passwords.”
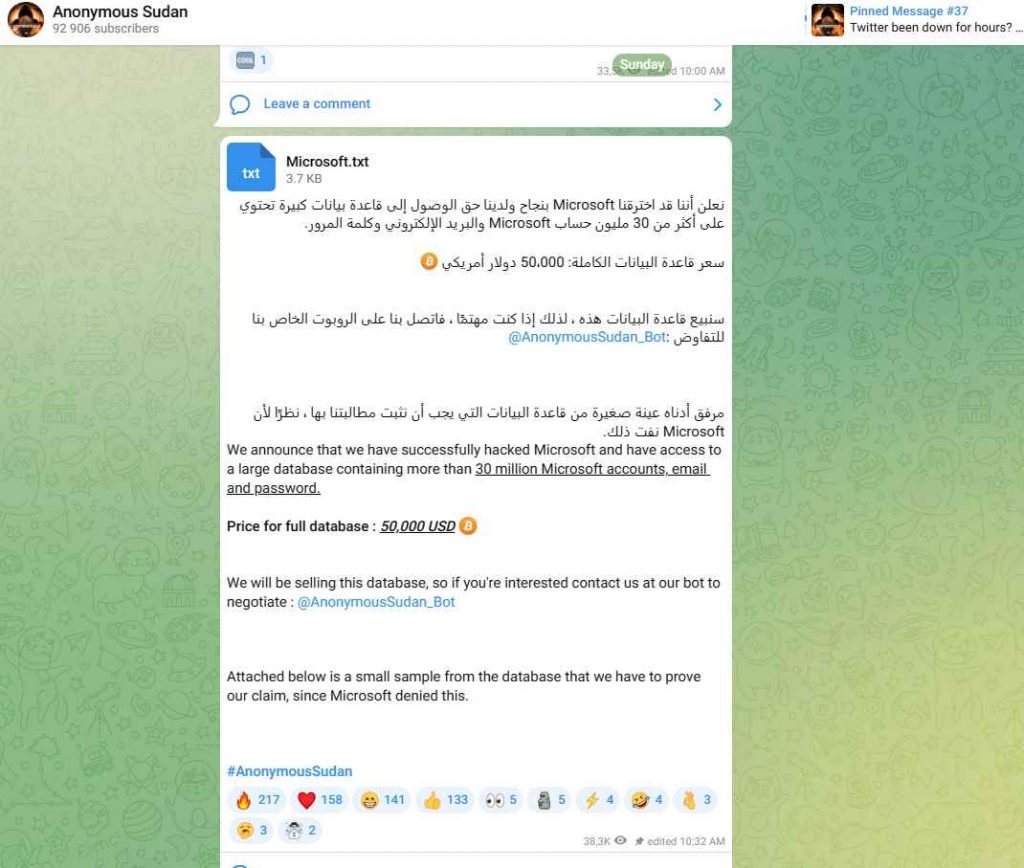
Anonymous Sudan is requesting that prospective purchasers negotiate with their bot by contacting them. According to the findings, the organization has been operational since January of 2023. It carried out distributed denial of service assaults on targets in vital infrastructure in nations like as Sweden, Australia, Germany, and Israel.
Microsoft has refuted the accusations that a data breach occurred. Microsoft said that the results of its investigation of the data that was readily accessible led them to the conclusion that the claim was not credible and that the data that was provided was an amalgamation of facts.
Microsoft asserts that Anonymous Sudan is responsible for creating the data by merging previously compromised or stolen data sets with new information. The site was informed by a spokeswoman for Microsoft that the company has not seen any evidence to suggest that user data was accessed or otherwise compromised.
Microsoft may investigate the accusations using one of two primary approaches. Either it may examine the data that was made publicly available to assess the veracity of it, or it can conduct an investigation into its own systems to establish whether or not a security breach had place. It’s possible that Microsoft’s first response to the breach was released online in order to discourage prospective customers.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











