The security experts at Bishop Fox have identified a major issue in several FortiGate firewalls and have given it the tracking identifier CVE-2023-27997. This flaw puts the firewalls at danger, despite a recent security patch update that was released by Fortinet.
This bug, which is known as an RCE flaw (which stands for “Remote Code Execution”), can be found in FortiOS, which is the connected operating system for Fortinet’s Security Fabric. This serious vulnerability received a score of 9.8 out of 10. There are around 490,000 SSL VPN interfaces on the internet that are vulnerable, and roughly 69% of them have not been patched. Despite the fact that this RCE bug, which stands for remote code execution, was caused by a heap-based buffer overflow problem in FortiOS. There are around 490,000 SSL VPN interfaces on the internet that are vulnerable, and roughly 69% of them have not been patched. Despite the fact that this RCE bug, which stands for remote code execution, was caused by a heap-based buffer overflow problem in FortiOS.
The exploit of this flaw may be used to do the following things:
Breaks the heap
Establishes a connection to the attacker’s server
Downloads BusyBox binary
Opens an interactive shell
On a 64-bit system, the exploit may be executed in a single second, which is far faster than the pace shown in the example video. Researchers were able to locate machines that have accessible SSL VPN ports with the assistance of the Shodan search engine.
By searching for appliances that had specified HTTP response headers, they were able to find machines that redirected to ‘/remote/login,’ which indicated that an exposed SSL VPN interface was present.
There were a variety of degrees of Xortigate (CVE-2023-27997) vulnerability among the 489,337 devices that were discovered by the query. After further examination, it was found that 153,414 appliances had been upgraded to a more secure version of FortiOS.
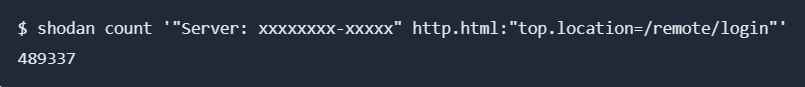
The previous estimate of 250,000 vulnerable FortiGate firewalls generated from less trustworthy inquiries has been surpassed by the new figure of about 335,900 vulnerable web-accessible FortiGate firewalls.
The proof-of-concept exploit code for critical-severity issues is accessible to the public, which makes the devices in question susceptible to attack. At this time, the only solution that can be used is “Disable SSL-VPN.”
In order to protect important assets, it is highly advised that major vulnerabilities be patched as soon as possible, especially those that are amenable to proven exploitation. This vulnerability, CVE-2023-27997, may result in data breaches, ransomware attacks, and other severe repercussions.
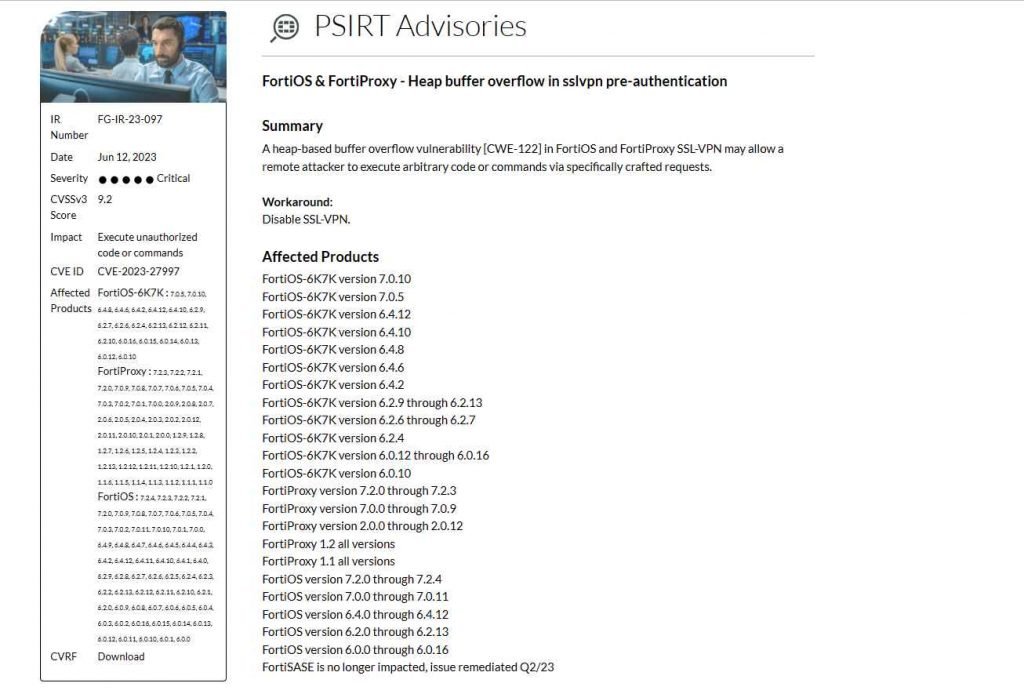
In the list that follows, you will find all of the products that are impacted by this:

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










