One of the most popular open-source systems for analytics and visualization, Grafana, was found to have a security flaw.This open-source platform serves a wide variety of users, from those working on small-scale projects to those doing enormous enterprise-level installations, and it provides tools for data analysis and visualization that are both simple to use and aesthetically pleasing.
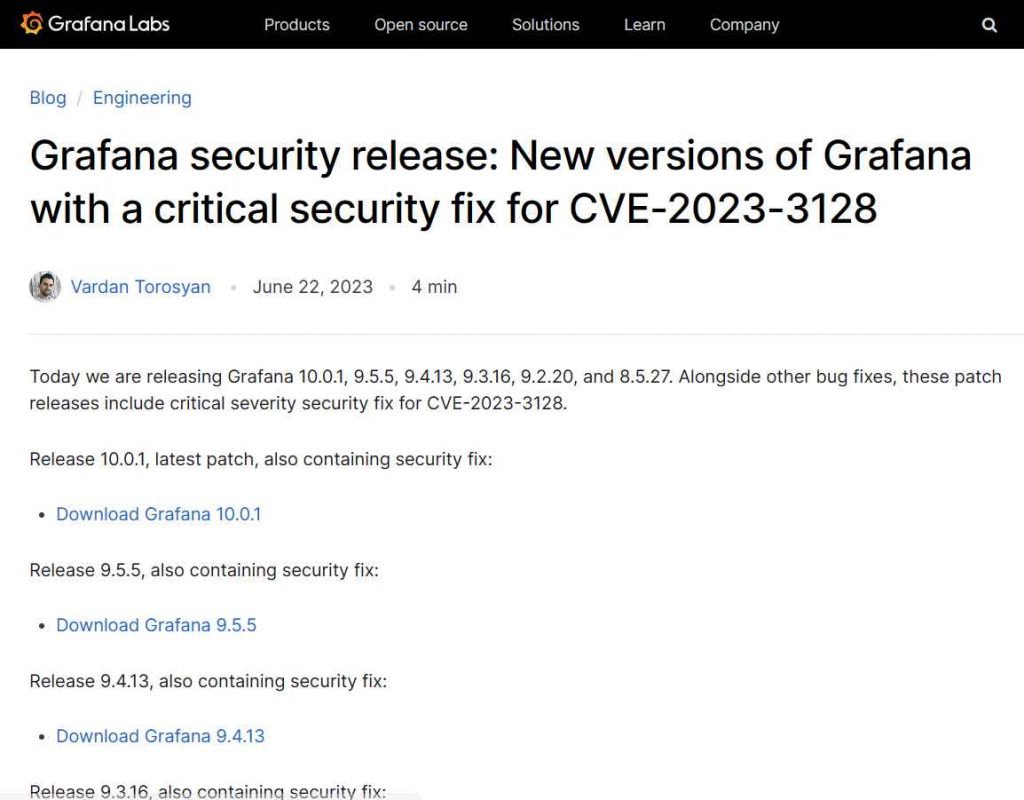
The security issue, which has been assigned the identifier CVE-2023-3128 and received a score of 9.4 out of 10 on the CVSS scale for severity, has the potential to enable an adversary to circumvent authentication protocols and gain control of a user’s account.In its most basic form, the CVE-2023-3128 vulnerability in Grafana allows for the bypassing of authentication or the taking over of another user’s account. The validation method that Grafana uses is the primary cause of this vulnerability. Grafana is able to specifically check Azure Active Directory (Azure AD) accounts based on their email claim when it is used in combination with Azure Active Directory (Azure AD) OAuth. This is where the difficulty rests. Because the email address used in the profile box is not guaranteed to be unique across all Azure AD tenants, it is possible for one Azure AD tenant to impersonate another by using an email address that is similar to their own.
The extent of this vulnerability’s possible repercussions is both wide-ranging and concerning. By exploiting this security hole, attackers might take complete control of a user’s account, giving them access to sensitive customer data as well as other important information.
The vulnerability is most prevalent in Grafana installations that use Azure AD OAuth and are set up with a multi-tenant Azure AD OAuth application but do not have an allowed_groups option. It is imperative that you take quick action if you are using a version of Grafana that is 6.7.0 or later.
The Grafana development team quickly reacted to this urgent issue by patching the vulnerability in versions 10.0.1, 9.5.5, 9.4.13, 9.3.16, 9.2.20, and 8.5.27 respectively. You are safe as long as the version of Grafana you are using is either one of these or a later one.
But what if an update isn’t something that can be done right away? The good news is that there are mitigating strategies that can be implemented. In the first place, making sure that a user who signs in also belongs to a group in Azure AD may be accomplished by adding an allowed_groups parameter to your Azure AD setup. Because of this step, the possibility of an attacker using an arbitrary email has been significantly cut down.
Alternately, the attack vector may be effectively eliminated by registering a single tenant application in Azure Active Directory. This removes the possibility of cross-tenant impersonation, which is the attack vector.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











