Any user who has a Microsoft account is able to communicate with ‘external tenants’ via the usage of Microsoft Teams. Any company or organization that makes use of Microsoft Teams qualifies as an external tenancy for the purposes of this discussion.
Members of the Red Team at the security services business Jumpsec, did some digging and found a means to send malware via Microsoft Teams while using an account that was not affiliated with the target enterprise.
Users of one Microsoft tenancy are able to communicate with users of another Microsoft tenancy thanks to the fact that each of these organizations has its own Microsoft tenancy. When this is done, a banner reading “External” shows next to the name, as seen in the following example.
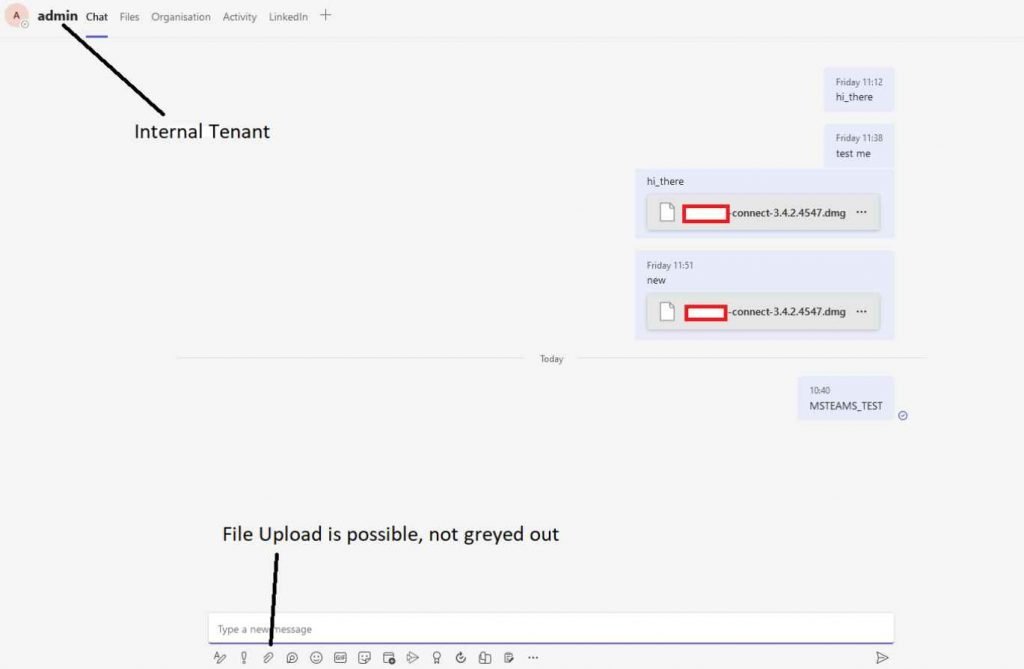
In contrast to when you are texting members of your own tenancy, you are unable to transmit files to staff members of other organizations while you are using messaging. See the difference in the following:
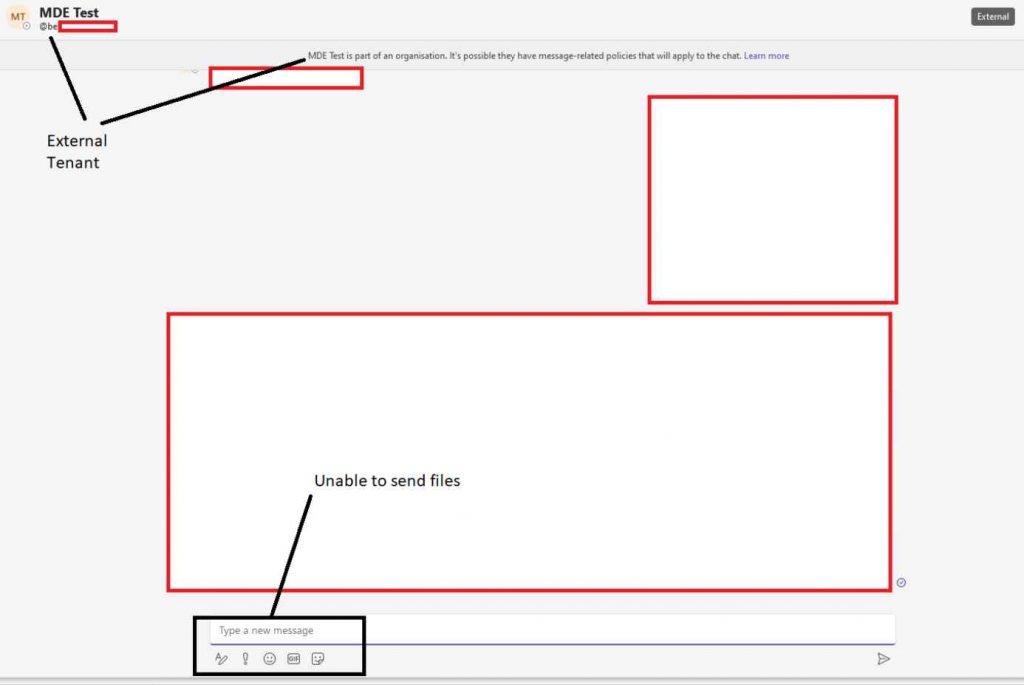
When the payload is sent in this manner, it is really housed on a Sharepoint domain, and the target gets it directly from that location. The recipient’s inbox, on the other hand, will see it as a file rather than a link to the file.
The fact that this circumvents practically all of the contemporary anti-phishing security mechanisms listed in the introduction to this warning makes it a potentially profitable channel for threat actors to deliver payloads. This advise warns that this should be avoided at all costs.
To begin, purchasing and registering a domain that is highly similarto your target organizations using M365 is a fairly basic process. It eliminates the need that you make use of mature domains, which require web servers, landing pages, CAPTCHAs, domain categorization, and URL filtering.
Second, it prevents the now-justifiably risky behavior of clicking on a link in an email, which is something that staff members have been instructed to avoid for years now. This drastically lowers the possibility that a regular staff member would recognize this as a phishing attack. The payload will now be supplied by a reliable Sharepoint domain, and it will arrive in the form of a file in the inbox that is associated with the target’s Teams account. As a result, the payload is not considered to be a malicious phishing website but rather one that inherits the trust reputation of Sharepoint.
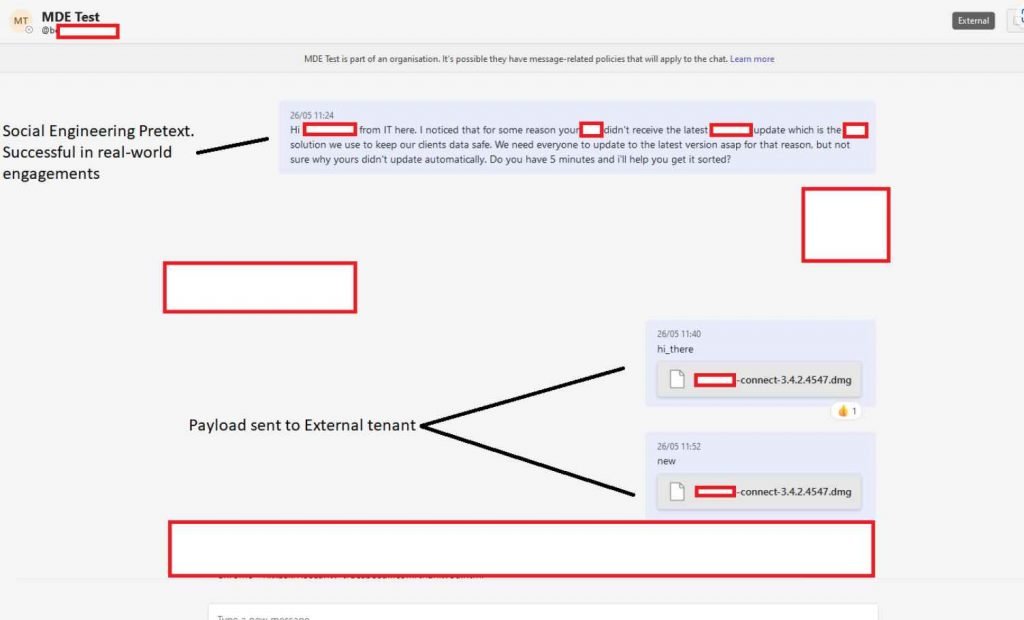
Finally, when this vulnerability is paired with social engineering via Teams, it is quite simple to begin a chat, hop on a call, share screens, and do a variety of other things. When compared, it makes social engineering via email seem rather stale and stop-and-start rather than dynamic. When you put this strategy into action on an actual engagement, you can ask the target, under the guise of an IT specialist, whether they would be willing to join a call so that we could install some urgent software patches. Once on the call, this vulnerability could be used to send a payload, and when paired with a comprehensive social engineering attack, the victim unwittingly would grant the attacker implicit confidence.
Microsoft was notified of this vulnerability, and while the company confirmed that it is real, they said that it “did not meet the bar for immediate servicing.”

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











