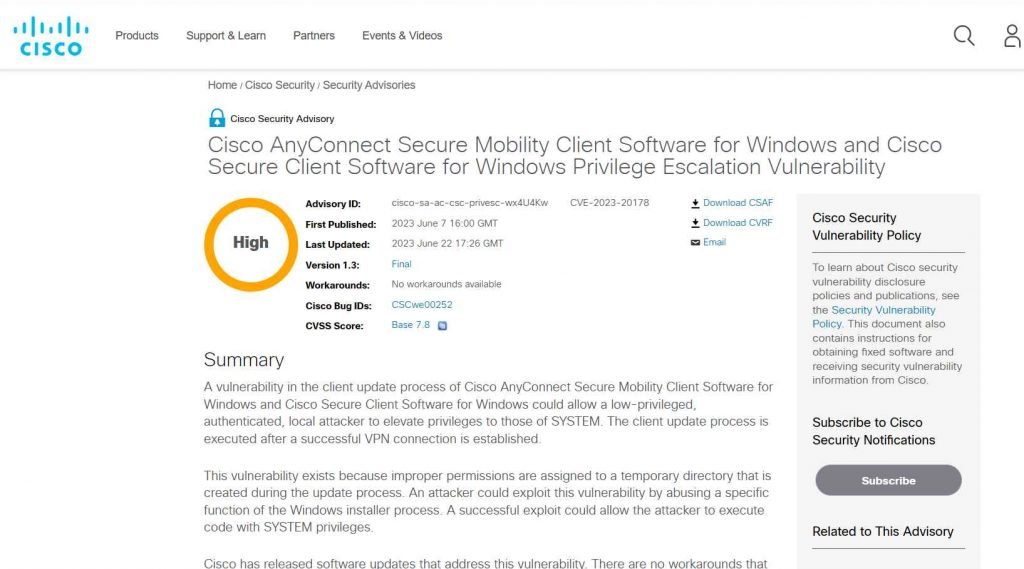
AnyConnect Secure Mobility Client Software for Windows and Cisco Secure Client Software for Windows both include a high-severity vulnerability, and proof-of-concept attack code for exploiting the issue has been made public. Users who have not yet applied the patch are strongly encouraged to do so as soon as possible in order to avoid being exploited. Malicious actors have, in the past, attempted to exploit vulnerabilities in the Cisco Secure Client Software that were not fixed.
IT administrators use Cisco Secure Client Software as an endpoint management tool. This software is a remote access solution that enables workers to connect to the network from any place by means of a Virtual Private Network. Cisco Secure Client Software is utilized by IT administrators. The vulnerability, which has been assigned the tracking number CVE-2023-20178, has a base score of 7.8 on the CVSS scale.
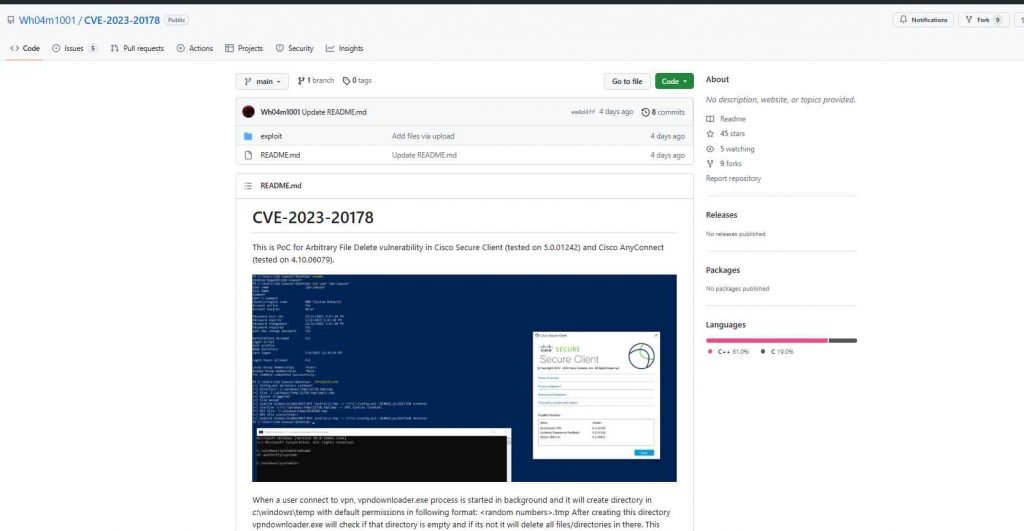
Filip Dragovi, a security researcher, discovered the Arbitrary File Delete vulnerability and reported it to Cisco. Dragovi also released the proof-of-concept (PoC) attack code that may be used to exploit the issue.
According to Dragovi’s explanation, this proof of concept was tested using Cisco Secure Client (tested on version 5.0.01242) and Cisco AnyConnect (tested on version 4.10.06079).
The researcher explains that “when a user connects to vpn, vpndownloader.exe process is started in the background,” and that “it will create [a] directory in c:windowstemp with default permissions in [the] following format: random numbers>.tmp.”
“After establishing this directory, vpndownloader.exe will check to see whether that directory is empty. whether it isn’t, vpndownloader.exe will remove all of the files and folders that are contained inside that directory. This behavior has the potential to be exploited in order to delete arbitrary files when logged in as the NT Authority SYSTEM account.
Using the method outlined in this article, the attacker may then escalate their privileges by spawning a SYSTEM shell via the deletion of arbitrary files by taking advantage of the behavior of the Windows installer and the fact that a client update procedure is conducted after each successful VPN connection. This allows the attacker to gain full control over the system.
This vulnerability may be exploited by an authorized, local attacker to elevate their privileges to SYSTEM level. The issue impacts the client update process. The vulnerability is caused by incorrect permissions on a temporary directory that is generated while the update process is running. The vulnerability may be exploited by misusing a particular component of the Windows installation process. An attack that takes advantage of the vulnerability is not complicated and does not need any effort on the part of the user.
There is no other way around the vulnerability; installing the patch is the only method to cure it and stop it from being exploited. On June 13, 2023, a patch was made available to correct the vulnerability, and at the time of its release, there were no known instances of the vulnerability being exploited by anybody. AnyConnect Secure Mobility Client for Windows 4.10MR7 and Cisco Secure Client for Windows 5.0MR2 both have fixes for the vulnerability that had been discovered.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











