Experts from Microsoft Defender discovered a multi-stage adversary-in-the-middle (AiTM) phishing and business email compromise (BEC) attack that targeted firms that provide banking and financial services. The attack began with the penetration of a reliable third-party vendor and progressed into a string of AiTM attacks as well as subsequent BEC activities that spread across many businesses. This attack demonstrates the sophistication of AiTM and BEC threats, which use the trusted connections that exist between vendors, suppliers, and other partner businesses for the purpose of committing financial fraud. Even while the attacks was successful in achieving its ultimate aim of a normal AiTM phishing attack followed by corporate email compromise, important components of the attack, such as the use of indirect proxy rather than the traditional reverse proxy tactics, demonstrate the ongoing development of these threats. Because this campaign made use of indirect proxy, the attackers had freedom and flexibility when it came to customizing the phishing sites to their targets, which helped them move closer to their aim of stealing session cookies as per experts. After logging in with the stolen cookie obtained via a session replay attack, the threat actors updated MFA methods without being presented with an MFA challenge by using multifactor authentication (MFA) rules that had not been established following security best practices. After afterwards, there was a second stage of the phishing effort, which consisted of sending over 16,000 emails to the target’s contacts.
This attack brings to light the intricacy of AiTM attacks and the extensive defenses that are required to fend them off. This complex AiTM attack necessitates additional remedial procedures in addition to the conventional ones for identity compromise, such as resetting a password. The affected companies need to delete their session cookies and undo any changes made to MFA that were carried out by the malicious attacker. This event also illustrates the need of engaging in proactive threat hunting to uncover new tactics, techniques, and procedures (TTPs) for previously recognized campaigns in order to identify and eliminate threats of this kind.
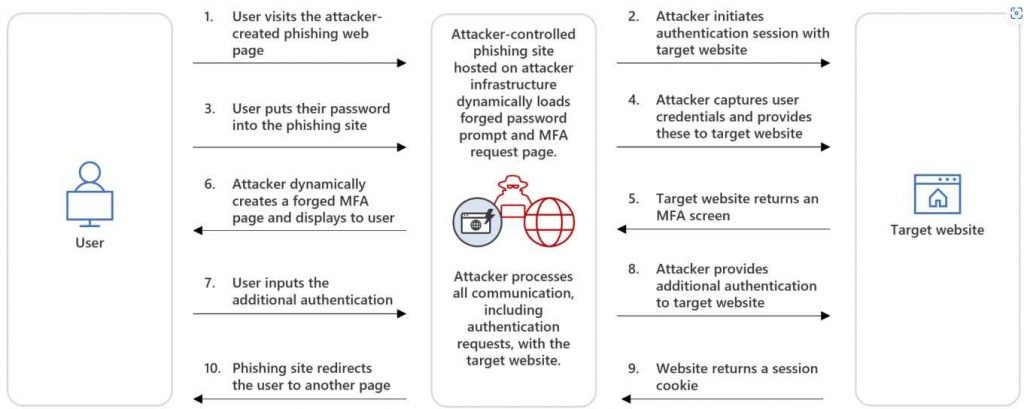
It is a sort of attack known as adversary-in-the-middle, and its intent is to intercept authentication that is taking place between users and a genuine authentication service for the purpose of either compromising identities or carrying out other types of operations. In order to steal a user’s credentials and intercept MFA in order to get their hands on the session cookie, the attackers will place themselves in between the user and the service. After then, the attackers may impersonate the user by replaying the session with the stolen session cookie before the time the token is set to expire, and they can do this without the user having to intervene or employ MFA. Because of this session, the attackers were able to access the resources and apps of the person who was compromised, as well as carry out additional malicious operations such as corporate email compromise attacks. Since the attackers are the ones who put up the phishing website as part of an AiTM attack via the indirect proxy approach, they have more control over the material that is shown on the website and may adjust it to correspond with the situation. In addition, since the perpetrators of the phishing attack are in control of the infrastructure, they have the ability to set up many servers simultaneously in order to avoid detection. There is no HTTP packet proxying as there is in traditional AiTM attacks; instead, there is direct communication between the target and the real website.
After a valid password has been entered and successfully validated, the server will provide a phony MFA page if MFA is requested. After the user has supplied their MFA token, the adversary will utilize that same token in the session that they have begun with the authentication provider. After the successful completion of the authentication process, the session token is given to the attacker, and the victim is taken to a different page. Following are attack stages
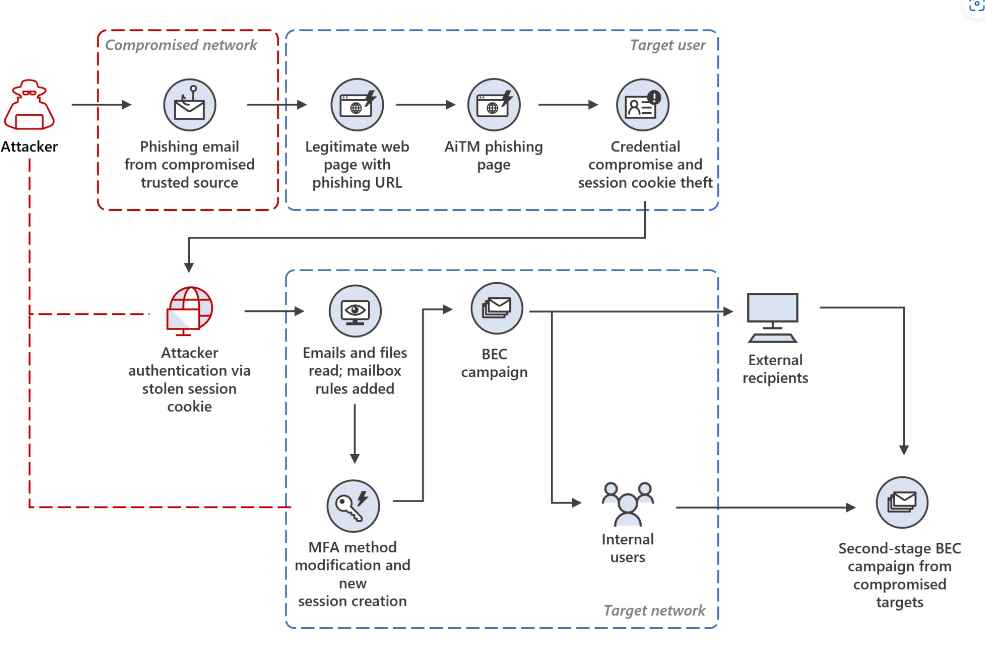
Stage 1: Initial access via a trusted vendor breach
Phishing emails purporting to come from reputable suppliers to the targeted companies were the first step in the campaign. A seven-digit number was used as the subject line of the phishing email that was sent. Because this code was different for each of the organizations that were targeted, it is probable that the attacker used it as a tracking method.
Stage 2: Clicking a harmful URL
In order to evade discovery, threat actors often exploit genuine services and trademarks in their activities. In this particular case, we were able to determine that the malicious actor behind the phishing effort used the respectable online tool Canva.
Stage 3: AiTM attack
When the user tried to access the URL, they were instead sent to a phishing website that was hosted on Tencent’s cloud infrastructure and imitated a Microsoft sign-in page.
Stage 4: Replay of the session cookie
An impersonation attack known as a stolen session cookie replay attack occurs when an adversary utilizes a genuine cookie that was stolen in order to fool authentication measures such as passwords and multi-factor authentication.
Stage 5: Modifying the MFA process
After that, the attacker went ahead and set up a new multi-factor authentication method for the target’s account, which consisted of a phone-based one-time password (OTP). This was done so that the attacker could sign in using the user’s stolen credentials without being discovered.
Stage 6: Developing an inbox rule
After some time, the attacker logged in with the new session token and proceeded to build a new Inbox rule with parameters. This rule transferred all incoming emails on the user’s mailbox to the Archive folder and tagged all of the emails as read.
Stage7: Phishing operation
After creating an Inbox rule, the attacker started a large-scale phishing effort that included more than 16,000 emails with a Canva URL that had been slightly changed. The emails were sent to distribution lists in addition to the contacts of the compromised user, who may have been located either within or outside of the business. The recipients were identified using the most recent email threads found in the inbox of the individual whose account had been hijacked.
Stage 8: BEC strategies and tactics
After that, the attacker checked the mailbox of the target user for emails that had not been delivered or that had been marked as out of office, and then they removed those emails from the Archive folder. The perpetrator of the attack went to the trouble of reading the emails sent by recipients who had doubts about the legitimacy of the phishing email and then replied, most likely to give the impression that the email is real when it is not.
Stage 9: Compromised Accounts
Phishing email receivers from inside the company who navigated to fraudulent websites by clicking on links included in those emails were subjected to a second AiTM attack.
Stage 10: BEC in its second stage
After the second AiTM attack, it was discovered that the attacker was launching a new phishing campaign from the inbox of one of the users whose account had been hacked.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











