Researchers from SentinelLabs found a social engineering effort aimed at specialists in North Korean issues that was carried out by an advanced persistent threat (APT) organization with ties to North Korea. The APT group mostly concentrates its attacks on organizations and think tanks located in South Korea; however, they have also claimed victims in the United States, Europe, and Russia. Malware known as ReconShark, which was recently revealed as a reconnaissance tool, was seen being distributed by the attackers. The attack intends to deploy reconnaissance malware as well as steal Google credentials and subscription credentials from a reputed news and analysis service that focuses on North Korea. In 2013, a researcher from Kaspersky was the one who discovered the cyberespionage gang known as Kimsuky (also known as ARCHIPELAGO, Black Banshee, Thallium, Velvet Chollima, and APT43). At the end of October 2020, the United States Computer Emergency Readiness Team (US-CERT) issued a report on Kimusky’s recent operations. The study included information on the TTPs and infrastructure used by Kimusky.
The most recent campaign that was run by the state-backed organization Kimsuky focused on nuclear agendas between China and North Korea. These agendas are pertinent to the conflict that is now taking place between Russia and Ukraine.
Threat actors engage in extended email contact with the victims and employ weaponized papers in addition to faked URLs, websites that resemble reputable online platforms, and spoof websites. The effort is centered on the fraudulent acquisition of email accounts and subscription credentials for NK News. Based on the kind of malware that was used, the attack infrastructure, and the TTPs, SentinelLabs has determined that the campaign was carried out by Kimsuky.
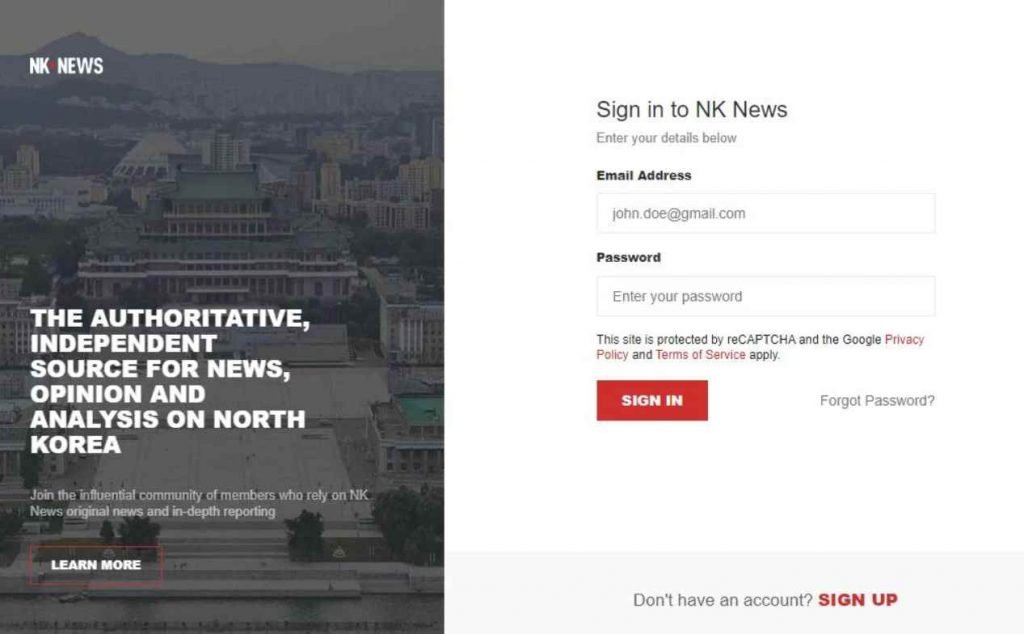
“Kimsuky’s concentration on making first contact and forming a rapport with their targets prior to commencing harmful actions is a defining characteristic of the activity . “As part of their initial contact strategy, the group impersonated Chad O’Carroll, the founder of NK News and the associated holding company Korea Risk Group, using an attacker-created domain, nknews[.]pro, which closely resembles the legitimate NK News domain nknews.org.” “[T]he group impersonated Chad O’Carroll, the founder of NK News and the associated holding company Korea Risk Group,” reads the report. The first email asks for feedback on a preliminary version of an essay that examines the danger presented by North Korea’s nuclear program.
The investigators saw Kimsuky send a spear phishing message structured in HTML. The message asked the recipients to study a draft analysis of the nuclear danger presented by North Korea. The email impersonates members of the NK News leadership and does not include any dangerous content; its purpose is to provoke a following dialogue between the receiver and sender. After the APT group has successfully engaged the target in discussion, they will finally send a follow-up email to the target with a URL that leads to a Google document.
The nation-state actors follow up with a reminder email in the event that the receiver does not respond to their first message in an effort to engage the target in dialogue.The attackers deceived users by changing the destination of the URL by modifying the href HTML attribute to go to a website that was under the attackers’ control.
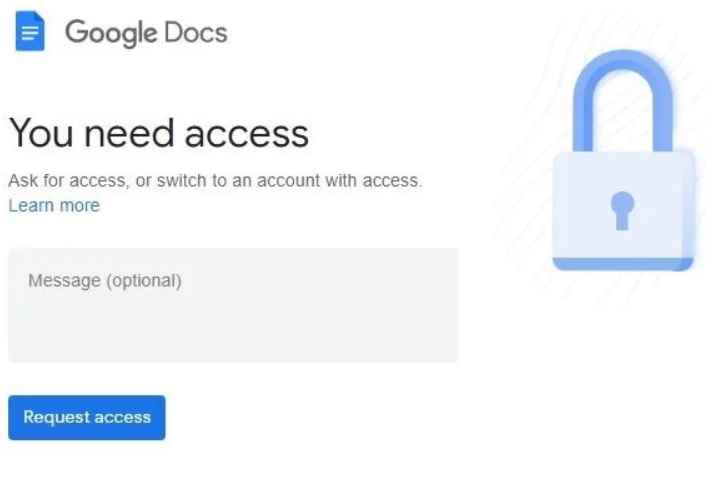
The URL that is shown leads to a paper that is posted on Google Docs and it discusses the issue of the nuclear danger posed by North Korea. This article has been edited in a way that makes it seem to be an authentic draft article by including revisions that are apparent to the reader. The destination of the URL has been faked so that it would take the victim to a website owned by Kimsuky’s that pretends to be an official Google Docs site and allows users to seek access to documents. After the APT group has successfully engaged the target in discussion, they will finally send a follow-up email to the target with a URL that leads to a Google document. During their talks with the victims, the researchers saw that threat actors were passing around password-protected weaponized Office documents. The reconnaissance instrument known as ReconShark was deployed with the help of the archive.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










