Researchers from Tsinghua University and George Mason University have discovered a significant weakness in the NPU chipset. By exploiting this flaw, attackers are able to eavesdrop on data being broadcast across 89% of real-world Wi-Fi networks.
Hardware acceleration, such as the use of NPU chipsets in Wi-Fi networks, increases the data transmission rate and decreases latency. However, it also creates security problems owing to the direct transmission of wireless frames by Access Point (AP) routers.

Researchers from Tsinghua University and George Mason University have recently found a security weakness in the wireless frame forwarding mechanism used by the NPU. Attackers may take use of the vulnerability to conduct a Man-in-the-Middle attack (MITM) on Wi-Fi networks by circumventing the need for rogue access points (APs). Intercepting a victim’s plaintext communication while avoiding link layer security methods such as WPA3 is possible with this technique. The research paper that team wrote has been approved for presentation at the 2023 IEEE Symposium on Security and Privacy.
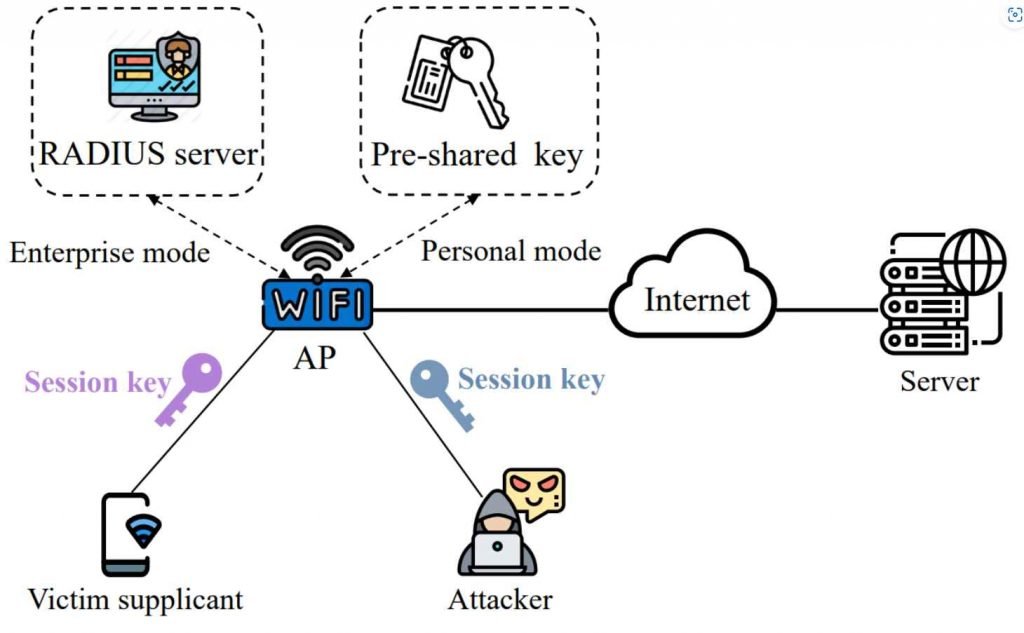
The scenario shown in Figure depicts a situation in which an attacker and a victim supplicant are both connected to the same Wi-Fi network in order to access Internet services. Imagine that you have successfully completed the phone authentication process and are now able to access the Wi-Fi network at Starbucks. Each session to the AP router is protected by a Pairwise Transient Key (PTK) session key, and the Wi-Fi network that you are trying to connect to has WPA2 or WPA3 installed to provide security.
They made the discovery that the security methods, such as WPA2 and WPA3, may be readily evaded, giving attackers the ability to read the plaintext of the victim supplicant’s communication. An impersonation of the access point (AP) is created by the attacker via the use of spoofing the source IP address. The attacker then sends a victim supplicant an ICMP redirect message, which is an ICMP error message with a type value of 5.
Because of the need to maximize performance, the NPU in the AP router (for example, Qualcomm IPQ5018 and HiSilicon Gigahome Quad-core) would immediately transfer the bogus message of ICMP redirection that it has received to the victim supplicant. After receiving the message, the victim supplicant will be deceived into changing its routing cache and substituting the next hop to the server with the IP address of the attacker. This will allow the attacker to get access to the server. Because of this, future IP packets that were supposed to be sent to the server are instead routed to the attacker at the IP layer. This gives the attacker the ability to send the packets to their intended destination. The MITM attack is successfully carried out by the attacker, who does not make use of any rogue AP in the process. This allows the attacker to intercept and change the traffic of the victim supplicant invisibly.
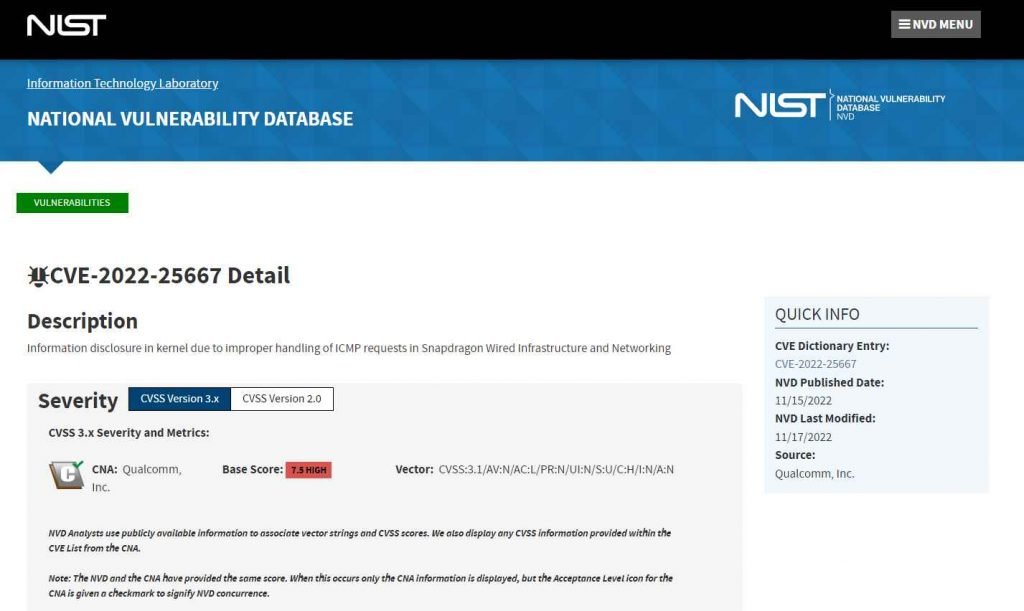
Both Qualcomm and Hisilicon have verified that their NPUs are susceptible to the vulnerability that prohibits AP devices from successfully blocking faked ICMP redirect packets. This vulnerability has been given the identifier CVE-2022-25667 by Qualcomm.
The researchers recommend two preventative steps that may be taken in response to this attack:
Adding features to access points that will slow down maliciously constructed ICMP redirection. If the message has clear unlawful features (for instance, the source IP address of the message is provided with the AP’s IP address, and the message can only be created by the AP itself), then the AP should block and discard the message as soon as it is detected. This strategy depends on the participation of both the NPU chip makers and the AP suppliers in a collaborative effort.
Improving the ability of supplicants to check the ICMP packets that they have received. The supplicant has the ability to successfully detect bogus ICMP messages and mount a defense against this attack provided it ensures that the source IP address and source MAC address of the received ICMP message are consistent with one another.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











