WinTapix is a driver developed by Microsoft for Windows.Donut is a position-independent shellcode that is used by this driver. It loads.NET Assemblies, PE files, and other Windows payloads from memory and then executes them with arguments. According to the findings of the analysis conducted by Fortinet specialists on the sample, the component in question is a Windows Kernel Driver. The characteristics it has are shown below.
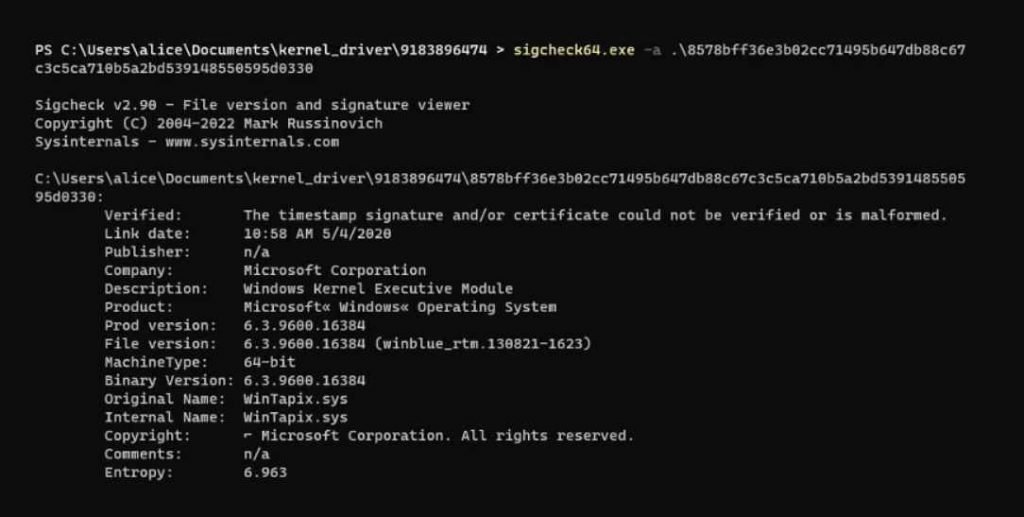
Due to the fact that its digital signature is incorrect, the threat actor may first need loading a vulnerable (but legal) driver before being able to attack that driver and load the Wintapix.sys file. After the driver has been loaded, however, the following execution chain will take place:
- Wintapix.sys is loaded into the kernel of the operating system.
- Wintapix.sys is capable of injecting shellcode into a process that has the appropriate level of local system privilege.
- A.NET payload that has been encrypted is loaded and executed by the injected shellcode.
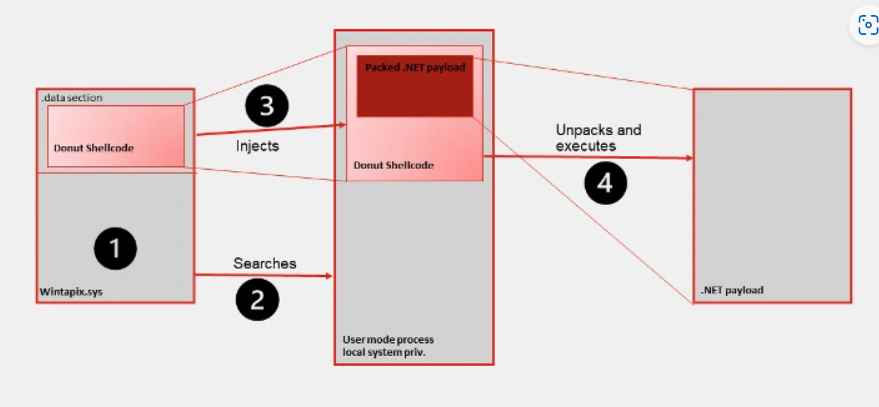
In its most basic form, Wintapix.sys is a loader. As a result, its major objective is to create and carry out the next stage of the attack. This is accomplished with the help of a shellcode.
In order for the driver to be able to inject the shellcode, it must first locate an appropriate target process. The following are some of the prerequisites for the intended process:
- A Local System account is being used to carry out the task.
- The process is of the 32-bit kind.
- The name of the process is not included on the list of executables that should be blocked, which includes ‘wininit.exe, csrss.exe, smss.exe, services.exe, winlogon.exe, and lsass.exe.’
Establishing persistence is yet another essential role that Wintapix.sys plays in the system. The first step in doing this is to create register keys. It’s interesting to note that the driver will load even in Safe Boot. Safe Boot is a diagnostic starting mode in Windows that boots the system with the very minimum number of drivers and services. Safe Mode is another name for Safe Boot. It is intended to assist users in diagnosing and fixing problems with the system’s software or drivers, which may otherwise prevent the system from starting properly. The driver may also be loaded in Safe Boot, which provides an additional layer of persistence to the whole mix.
The malicious software generates a list of websites that are hosted by the IIS server and then opens an HTTP listener on the URLs of those websites. It does this in order to search for requests that include instructions that it can then carry out. If given the appropriate instructions, it is also able to upload or download files.
It seems that Wintapix has been operational since at least the middle of the year 2020. It was most likely designed by an Iranian threat actor and deployed in operations mostly against businesses in Saudi Arabia, but also against targets in Jordan, Qatar, and the United Arab Emirates.
According to Fortinet, the driver was most likely used in some large campaigns in the months of August and September 2022 as well as in the months of February and March 2023, despite the fact that it has stayed under the radar to this day. The compilation dates on the seen samples are between May 2020 and June 2021, however the samples were encountered in the wild much later.
Considering that Iranian threat actors are known to compromise Exchange servers in order to spread further malware, there is a distinct possibility that this driver has been used in conjunction with attacks that target Exchange. To that point, the period of compilation of the drivers is also associated with times when Iranian threat actors were attacking vulnerabilities in Exchange servers, according to Fortinet.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











