A variety of Cisco products have been found to include several serious security flaws that might be exploited by hackers to cause serious problems including denial of service, remote code execution, privilege escalation, and other major vulnerabilities. The Common Vulnerability Scoring System (CVSS) score for these vulnerabilities, which places them in the “critical” category, is significant for its expression of their severity.
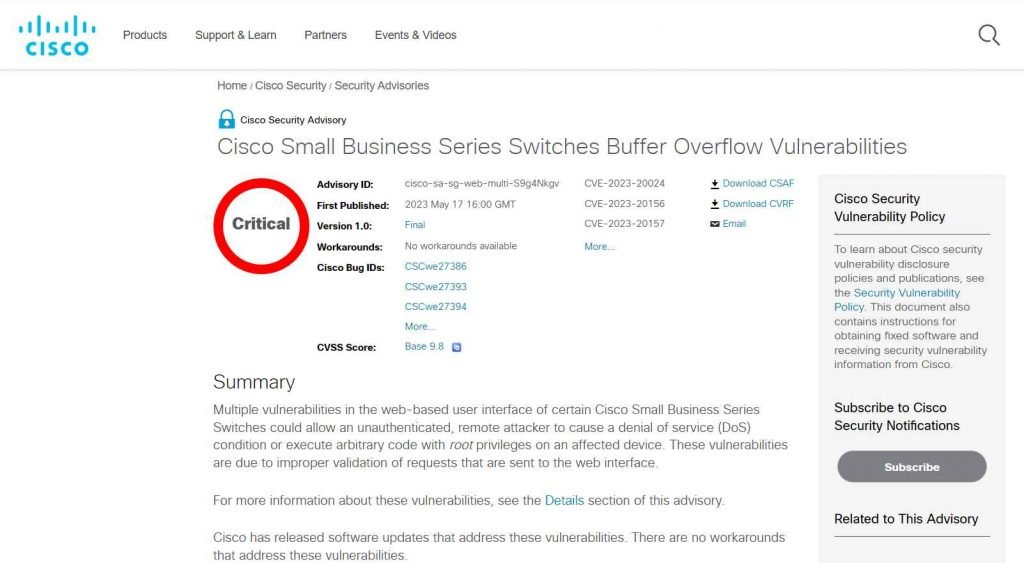
According to the CVSS rating methodology, four of the nine vulnerabilities are classified as serious since they have a score of 9.8 out of 10. The following product lines are impacted by the nine vulnerabilities. –
The 350 Series Managed Switches and the 250 Series Smart Switches both have a fix in firmware version 2.5.9.16.
Stackable Managed Switches from the 350X Series (Fixed in Firmware Version 2.5.9.16)
Stackable Managed Switches from the 550X Series (Fixed in Firmware Version 2.5.9.16)
Smart Switches from the Business 250 Series (Fixed in firmware version 3.3.0.16)
Switches from the Business 350 Series (Fixed in firmware version 3.3.0.16)
Smart Switches for Small Businesses in the 200 Series (Won’t Be Patched)
Switches from the 300 Series for Small Businesses (Won’t be patched)
Unpatched Small Business 500 Series Stackable Managed Switches
The four security flaws—CVE-2023-20159, CVE-2023-20160, CVE-2023-20161, and CVE-2023-20189—all originate from a flaw in the Cisco Small Business Series Switches’ web-based user interface. Inadequate validation of requests sent to the web interface is what leads to the vulnerabilities. Due to the absence of validation, a malicious request may be able to run arbitrary code with root privileges on the harmed device.
This implies that a remote attacker may possibly make a customized request via the web interface and execute arbitrary code with root capabilities on the target device without the need for authentication. Such an exploit has serious repercussions since it gives the attacker extensive access over the compromised system.
Cisco has made software upgrades available to help reduce these vulnerabilities. Since there are presently no effective workarounds, it is imperative for users and administrators of affected Cisco equipment to apply these updates as soon as possible.
The unauthenticated configuration reading vulnerability (CVE-2023-20162), the unauthenticated Denial-of-Service vulnerability (CVE-2023-20158), and the unauthenticated heap buffer overflow vulnerability (CVE-2023-20024, CVE-2023-20156, and CVE-2023-20157) in Cisco’s Small Business Series Switches were among the five other high-severity flaws for which patches were released this week.
It’s crucial to note that, despite the fact that these vulnerabilities have proof-of-concept exploit codes available, Cisco’s Product Security Incident Response Team (PSIRT) noted that, as far as they are aware, these vulnerabilities have not yet been used in cyberattacks. However, the fact that these attack codes exist demonstrates how quickly these vulnerabilities need to be fixed.
Network administrators and users of the impacted Cisco equipment should be aware that the products that have already started the end-of-life process will not get firmware upgrades resolving these vulnerabilities.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











