On Tuesday, Microsoft issued an updated patch to address a vulnerability that had previously been fixed in March but which was subsequently found by researchers in the security community to be ineffective.
Ben Barnea, a researcher at Akamai, found a method around the flaw that had been addressed in March. This manner, an attacker could exploit the vulnerability to force an Outlook client to connect to a server that was controlled by the attacker. Although the issue had been patched in March, the researcher found a way around the patch.
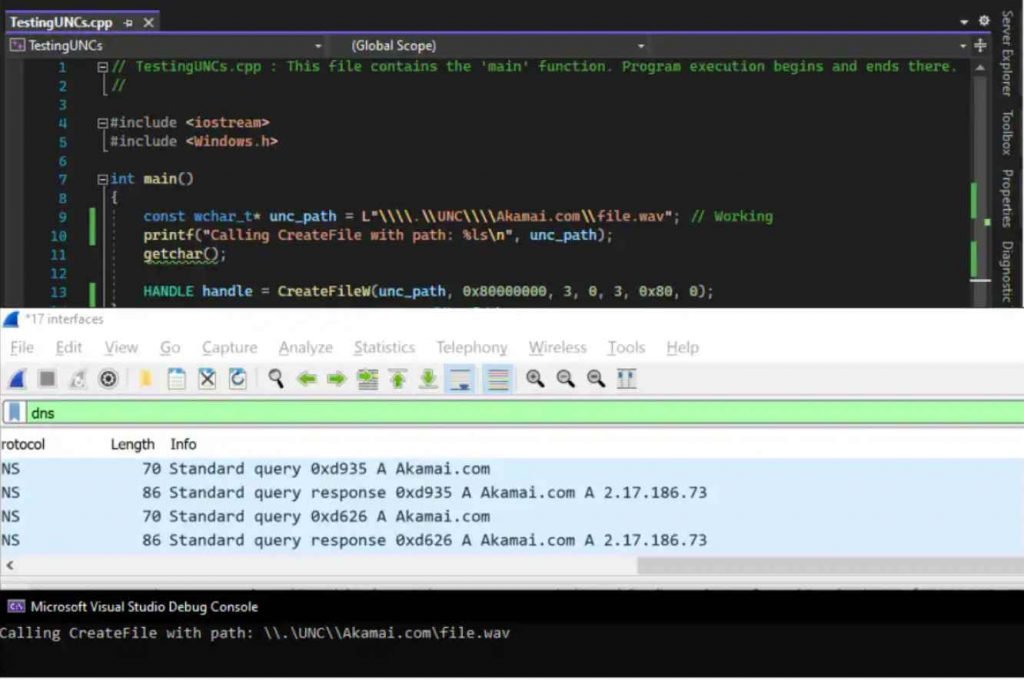
Barnea said that the problem is a zero-click vulnerability, which means that it can be activated with no interaction required from the user, and that all versions of Windows are vulnerable to it. Barnea elaborated by stating that the original patch was made meaningless by the introduction of a single new character. However, he and the security team at Akamai disagreed with the way Microsoft categorized the problem, which was assigned a CVSS score of just 6.5. They found it when they were analyzing the patch for CVE-2023-23397, which fixed the issue by changing the code flow in Outlook so that it now checks to see if the universal naming convention (UNC) path that retrieves the custom sound file refers to an internet URL, and if it does, it uses the default reminder sound instead of the custom one.
Un fortuitously, they also discovered that the check—and, as a consequence, the patch—can be readily broken by adding a single character, which would alter the way that a certain function categorizes the zone of the UNC route. This was a disappointing discovery.
Also, according to recent study conducted by Cybernews, more than 85,000 Microsoft Exchange servers do not have the necessary patches installed to protect them from multiple vulnerabilities that allow remote code execution and were resolved by Microsoft in February 2023.
Threat actors are able to remotely execute code on the target computer thanks to the vulnerabilities in question, which are recorded as CVE-2023-21529, CVE-2023-21706, and CVE-2023-21707. These vulnerabilities are tracked as CVE-2023-21529, CVE-2023-21706, and CVE-2023-21707.
Even though there have been no reports of attacks exploiting these problems at the time, Microsoft recommended enterprises to upgrade their servers as quickly as possible. This is because the holes theoretically might have been leveraged by hackers to get initial access to a corporate network. However, there have been no reports of attacks using these issues.
However, the findings of an investigation indicated that over three months after security upgrades were made available, many businesses that use Microsoft Exchange software are still susceptible to security flaws.
The team discovered that one in every three Microsoft Exchange servers was still missing their patch, the majority of which are situated in Germany (almost 18,000 of them).
Researchers examined a total of 248,350 internet-connected Microsoft Exchange servers. They found that 85,261 of those servers, or 34.33%, were vulnerable to RCE attacks.
The United States of America is the second most afflicted nation in the world, with approximately 16,000 servers that have not yet been patched. This is followed by the United Kingdom (3,734), France (2,959), the Netherlands (2,906), and Russia (2,775).
In addition, the researchers evaluated the distribution of Exchange versions and discovered that, in the majority of Western nations, newer versions that were still susceptible were more frequent, with the exception of the first minor version in a major release (for example, version 15.2.986.5 rather than 15.2.986.41).
Researchers discovered that earlier versions of Microsoft Exchange 2016 were preferred in the cases of China and Russia, despite the fact that newer versions were being utilized in the 2019 and 2013 releases. This was the case despite the fact that newer versions were available.
Even though it’s been many months since the RCE problems were discovered, the number of Exchange servers that are still missing their patches is scarcely going down at all. The researchers noticed that the number of susceptible servers in February was around 87,000, as shown by the statistics provided by the Shadowserver Foundation.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











