The Linux kernel is the most important part of the Linux operating system. It is in charge of managing system resources, delivering necessary services, and guaranteeing the general stability of the system. As a result, any vulnerability inside the kernel has the potential to have major implications, which might put the system’s overall security and integrity at risk. The Linux kernel has been found to include a major security flaw, which has been given the identifier CVE-2023-32233. This flaw makes it possible for locally authenticated users to gain additional rights while using the system. A locally authenticated attacker is able to get elevated privileges as root by submitting a specifically constructed request thanks to the vulnerability, which is caused by a use-after-free hole in Netfilter nf_tables while processing batch requests. The bug was caused by a use-after-free flaw. Linux has a subsystem known as netfilter nf_tables that is responsible for managing the setup of firewall rules. The problem is that Netfilter nf_tables is accepting some improper modifications to its configuration, which is causing the issue.
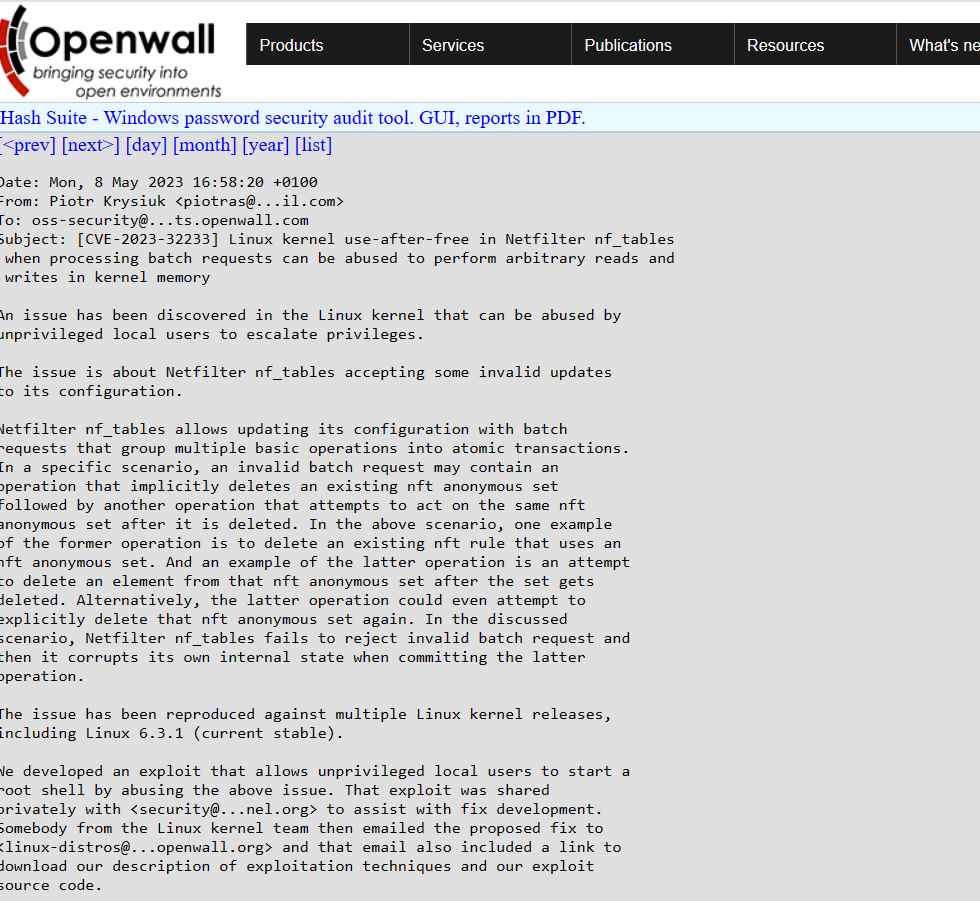
Security researchers Piotr Krysiuk and Piotr Krysiuk found the vulnerability and built an attack for it. The exploit makes it possible for local users without administrative privileges to launch a root shell by exploiting the problem. This attack was discussed in confidence with the Linux kernel security developers so that they may get assistance in developing a solution.
An adversary might take advantage of this vulnerability in a particular situation by constructing an erroneous batch request that includes actions that lead to a corruption of the internal state of Netfilter nf_tables. Because of this, the attacker is granted the ability to obtain root access to the system and further elevate their privileges.
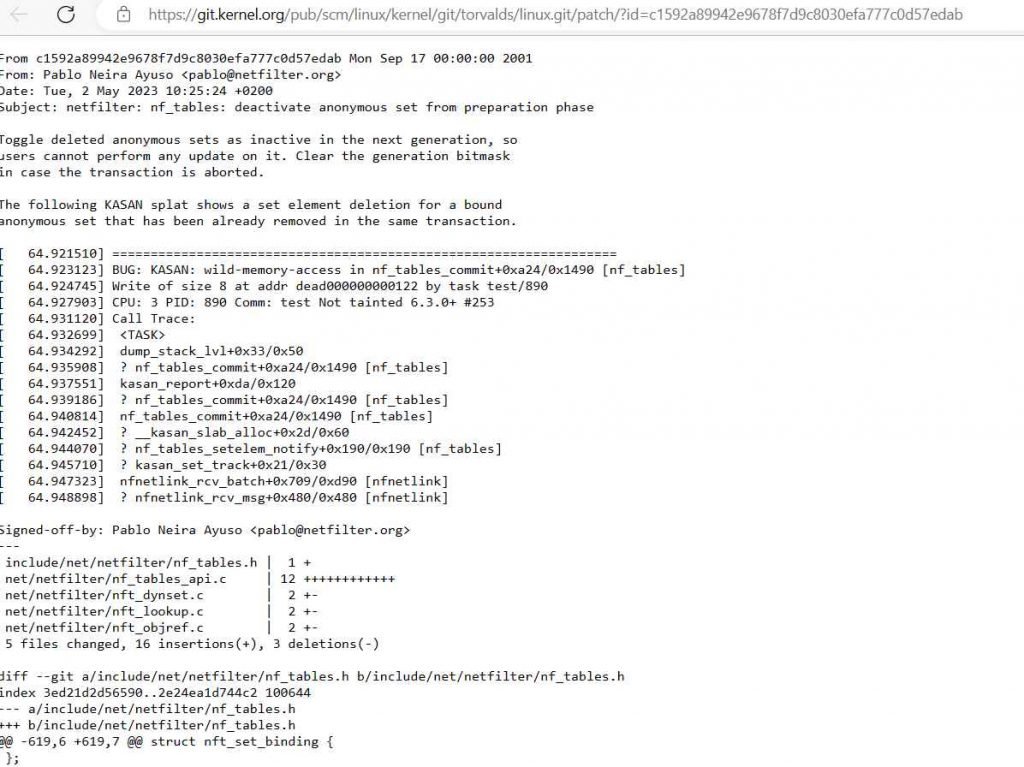
The mainline kernel git repository now provides a patch that may be used to resolve the vulnerability that was discovered. Administrators and users of the system are strongly encouraged to deploy the patch as quickly as they can in order to prevent their systems from the possibility of being exploited.
Multiple versions of the Linux kernel, including the most recent stable release, Linux 6.3.1, have been used to successfully replicate the issue. If this vulnerability is not fixed, it may be used by hostile actors to obtain unauthorized access to the system with elevated privileges. As a result, sensitive data may be compromised, and serious disruption may occur.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











