After being targeted by a spate of ransomware attacks, NCR’s Aloha point of sale platform is now unavailable due to the incident. The BlackCat/ALPHV gang has taken credit for the attack.
NCR is an American software and technology consultancy firm that specializes in providing restaurants, enterprises, and retailers with solutions for digital banking, point-of-sale (POS) systems, and payment processing.
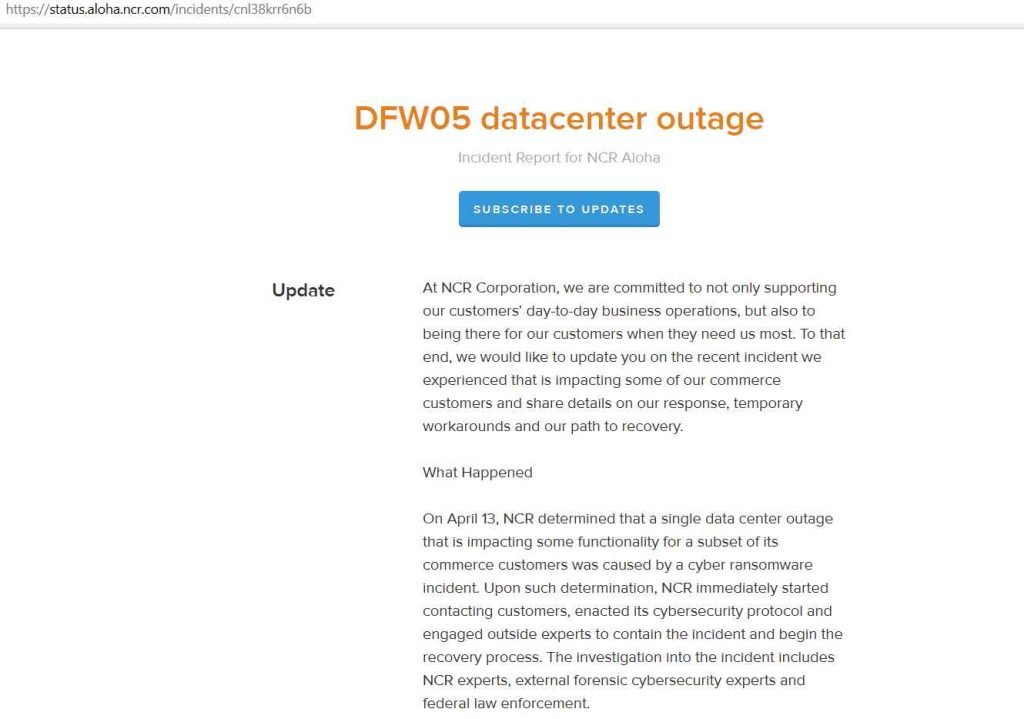
Since Wednesday, one of its products, the Aloha POS platform, which is utilized in hospitality services, has been experiencing an outage, and as a result, clients are unable to use the system. On April 12, NCR disclosed to the public for the first time that it was looking into a “issue” with the Aloha restaurant point-of-sale (PoS) device. An outage that occurred at a single data center on April 15 caused the business to report that a small number of auxiliary Aloha apps used by a fraction of its hospitality clients were among those that were affected.
“On April 13, we were able to establish that the disruption was caused by an incident using ransomware. As soon as we became aware of this turn of events, we immediately started notifying consumers, enlisting the assistance of third-party cybersecurity experts, and initiating an investigation. In addition, law enforcement has been alerted, the NCR said.
The firm has been attempting to restore the affected services, but in the meanwhile, they have said that affected restaurants should still be able to serve their guests; the only capability that has been disrupted is particular.
The ransomware gang known as BlackCat, Alphv, and Noberus claimed responsibility for the attack on their Tor-based leak website; however, the hackers withdrew the article almost immediately after it was published. At the very least, the BlackCat ransomware has been circulating since November 2021, and the leak website for this malware now includes more than 300 victims. It has been documented that the organization goes after manufacturing businesses. The term “BlackCat” was given to the ransomware group because the data leak site that they used included a picture of a black cat. On the other hand, the threat actors refer to themselves as ALPHV when they are discussing their operation on hacker forums and when they are negotiating.
Since its inception, the ransomware operation has expanded to become one of the most major ransomware operations currently operational. It is responsible for hundreds of attacks throughout the globe, and its demands for a ransom range from $35,000 all the way up to over $10 million.
In the post that has since been taken down, the hackers claimed that they were approached by NCR personnel who were interested in discovering the nature of the data that was taken from their systems. The hackers said that they did not acquire any real NCR data, but they did collect “a lot of credentials” that can be used to gain access to NCR client networks. The hackers also stated that they did not steal any NCR data.
BlackCat’s leak website seems to have removed a post that named NCR, which is a strong indication that discussions have begun and that the hackers are expecting to be compensated.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











