During its April 2023 Security Patch Day, the German corporate software manufacturer SAP announced a total of 19 new security notes, five of which were categorized as “hot news” and dealt with significant vulnerabilities (2 new flaws: CVE-2023-27497 & CVE-2023-28765, and 3 updates).
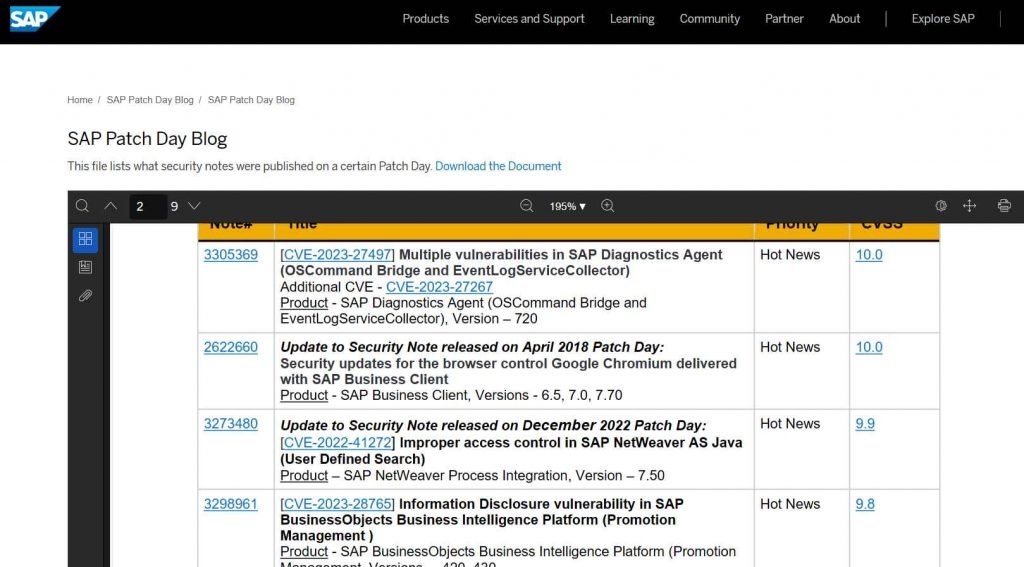
The vulnerability in the SAP Diagnostics Agent known as CVE-2023-27497, which has a CVSS score of 10, is the most serious of all (OSCommand Bridge and EventLogServiceCollector). An adversary is able to execute malicious scripts on all connected Diagnostics Agents running on Windows if the EventLogServiceCollector of SAP Diagnostics Agent – version 720 does not perform authentication or input sanitization of code. This vulnerability was discovered in SAP Diagnostics Agent version 720. If the exploit is effective, the attacker has the potential to entirely compromise not just the system’s secrecy but also its integrity and availability.
An attacker may use CVE-2023-27267 to run scripts on connected Diagnostics Agents by taking advantage of a lack of authentication and poor input validation in the OSCommand Bridge of SAP Diagnostics Agent version 720. This flaw can be found in the OSCommand Bridge. An exploit that is successful has the potential to result in the complete breach of the system.
An attacker with basic rights in SAP BusinessObjects Business Intelligence Platform (Promotion Management) – versions 420, 430, may exploit the problem to get access to the lcmbiar file and then decrypt the file using CVE-2023-28765. Once an attacker has obtained access to the credentials of Business Intelligence (BI) users, he may undertake activities that, depending on the rights of the BI user, can entirely compromise the program.
This month, SAP also disclosed that it would be releasing a high-priority security note that would patch a hole in SAP NetWeaver.
The eleven remaining security notes that SAP issued this week all deal with vulnerabilities that are rated as having a severity of either medium or low.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











