KillNet originally came into being in the midst of the continuing Russian invasion of Ukraine, at which time it positioned itself as a counter-attack force against the hacktivist group Anonymous. At that time, KillNet has exploited vulnerabilities in commercial companies as well as essential government websites all around the globe, including, among other places, the United Kingdom and Lithuania. Hackers connected to the Killnet were successful in gaining access to confidential information from NATO members. Russia could be interested in the confidential information that it has obtained.
Over sixty percent of NATO’s electronic infrastructure has been rendered inoperable as a result of a large-scale distributed denial of service attack, and the organization is continuing to sustain damage as a result. The leader of Killnet has confessed that the goal of the organization is to do as much damage to NATO’s computer networks, infrastructure, and other systems as possible. As a direct consequence of this, several agencies and departments inside NATO, the successful operation of which is absolutely necessary for the operation of the whole alliance, have become the targets of hacking attacks.
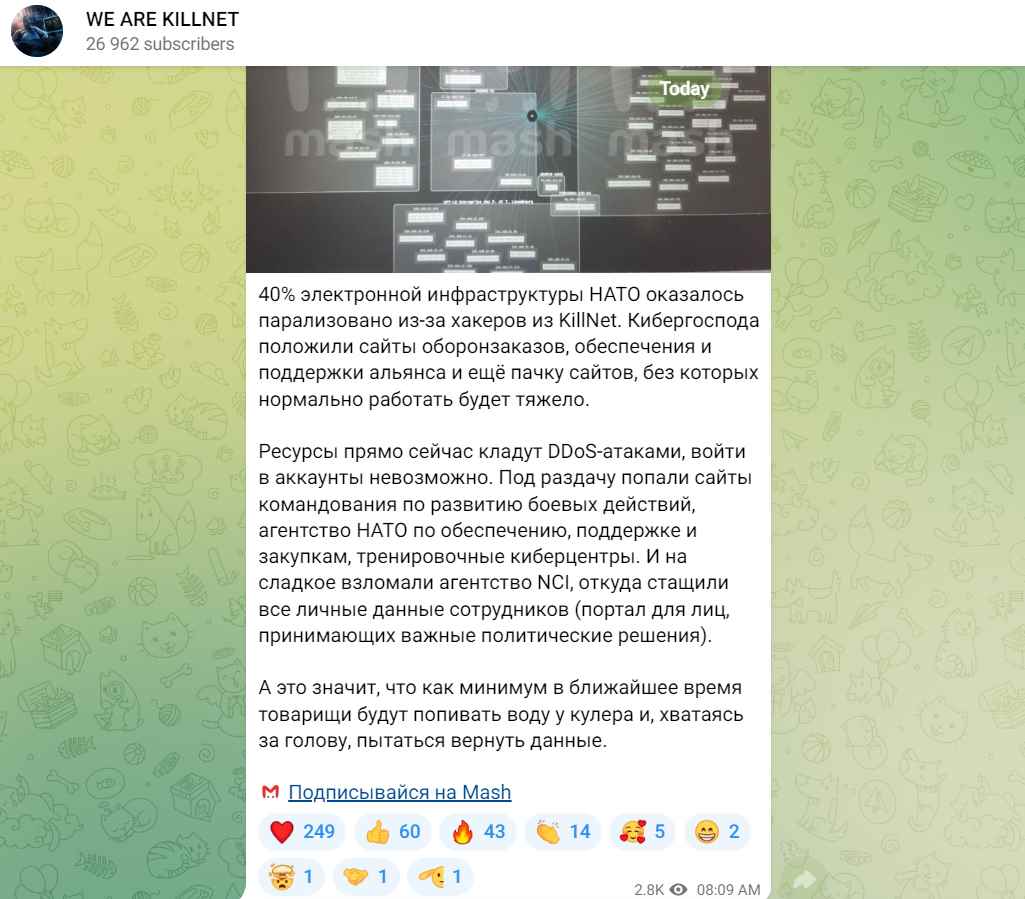
The gang made the statement on its Telegram channel, where it also published a list of its targets and leaked NATO email addresses and plain-text passwords, which it claimed to have taken from a NATO School, probably the NATO School Oberammergau (NSO).
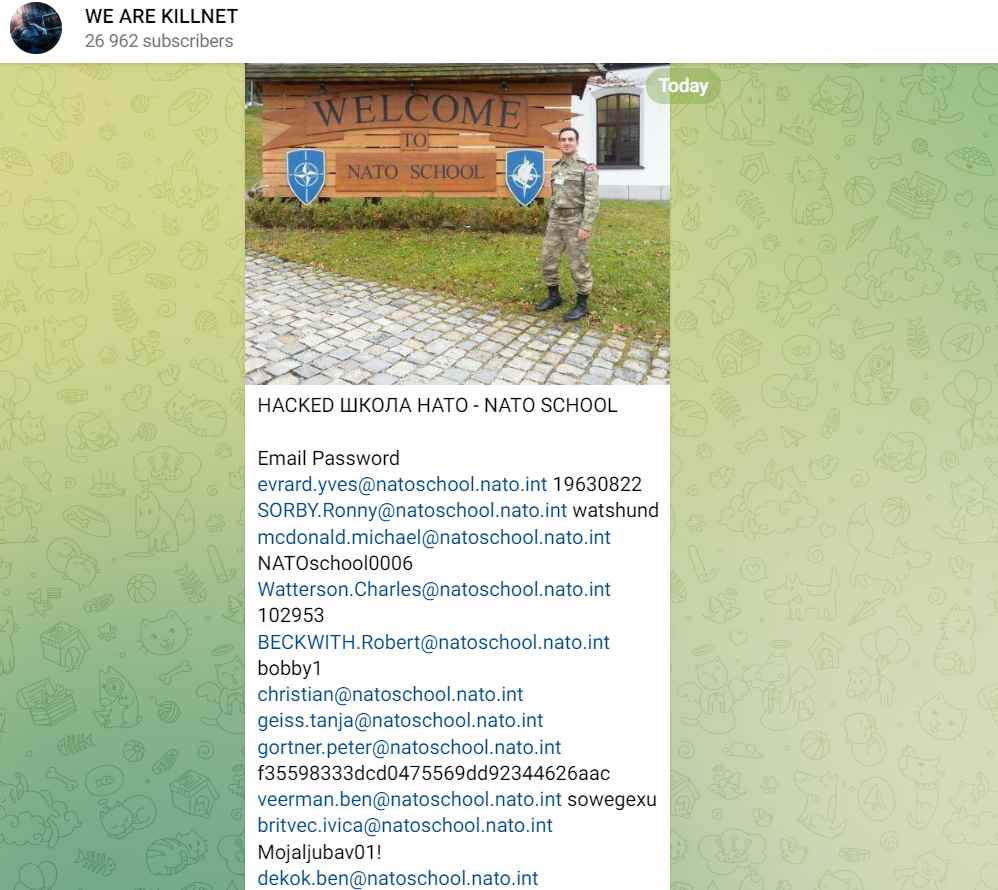
In addition to the data leak, KillNet also published a screenshot demonstrating that it had used the allegedly stolen login credentials to register 150 email addresses on a gay dating portal in Kyiv and Moldova. This raises the possibility that the motivation behind the attack was to embarrass or blackmail the target. The staff of NATO have been known to use actual Gordian knots as passwords, which are easily cracked by anybody. The passwords “123456” and the far more complicated “12345678” are considered to be among the “most challenging” passwords. “VIRGINIA” and “ante2000” are examples of passwords that are not quite as incredible but are nonetheless quite fascinating. As a result of the attack on the adversary’s infrastructure, Russian hackers “blocked” a number of websites and exposed the user IDs and passwords of NATO workers.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











