The Exynos Modems manufactured by Samsung Semiconductor were found to have eighteen 0-day vulnerabilities, as revealed by Project Zero. Internet-to-baseband remote code execution was possible due to the four vulnerabilities that were deemed to be the most serious among these eighteen flaws (CVE-2023-24033 and three further vulnerabilities that have not yet been allocated CVE-IDs). Tests that were carried out by Project Zero have shown that the aforementioned four vulnerabilities make it possible for an attacker to remotely compromise a phone at the baseband level without any interaction from the user; all that is required is for the attacker to know the phone number of the victim. We anticipate that highly competent adversaries would be able to swiftly design an operational exploit to compromise impacted devices in a stealthy and remote manner if they were just given access to modest extra research and development resources.
The fourteen other similar vulnerabilities (CVE-2023-26072, CVE-2023-26073, CVE-2023-26074, CVE-2023-26075, CVE-2023-26076, and nine additional vulnerabilities that have yet to be granted CVE-IDs) were not as serious since they need either a hostile mobile network operator or an attacker with local access to the device.
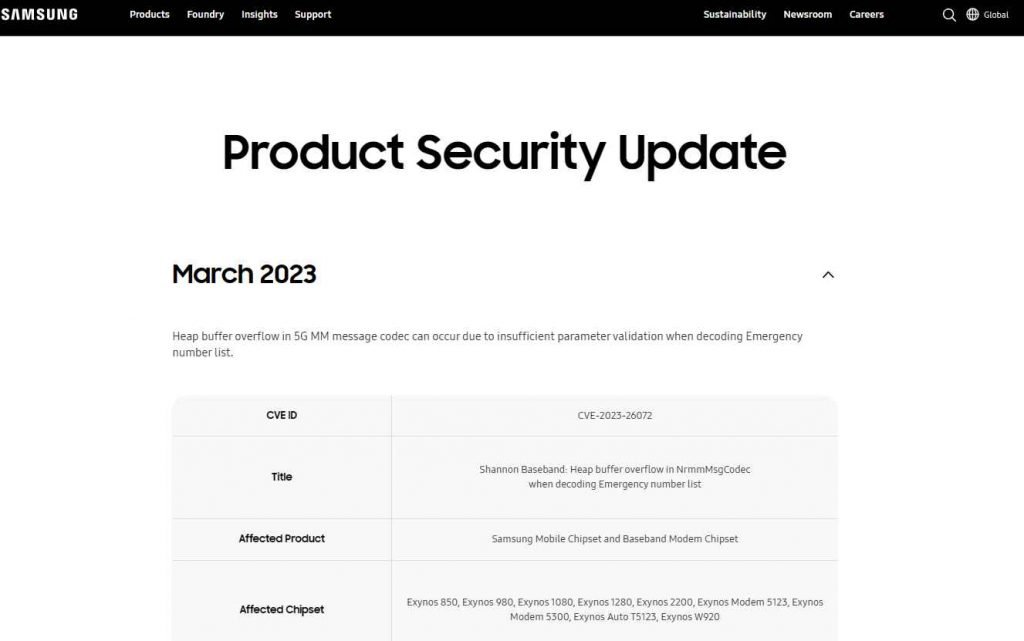
The list of Exynos chipsets that are susceptible to these vulnerabilities may be found in the advisory published by Samsung Semiconductor. On the basis of information obtained from public sources that provide a mapping of chipsets to devices, the following devices are likely to be affected:
Devices from Samsung’s S22, M33, M13, M12, A71, A53, A33, A21, A13, A12, and A04 series;
Devices from Vivo’s S16, S15, S6, X70, X60, and X30 series
Devices from Google’s Pixel 6 and Pixel 7 series
Any wearables that use the Exynos W920 chipset and vehicles that use the Exynos Auto T5123 chipset.
Timelines for patches to address these vulnerabilities will differ depending on the manufacturer. Those who have devices that are vulnerable may protect themselves from baseband remote code execution vulnerabilities in the meanwhile by turning off Wi-Fi calling and Voice-over-LTE (VoLTE) in the settings of their devices.
Due to the unusual combination of the level of access that these vulnerabilities provide and the speed at which they believe a reliable operational exploit could be crafted, the Google Security Team has decided to make an exception to their standard disclosure policy and delay the disclosure of the four most severe vulnerabilities. This decision was made because the Google Security Team believes that a reliable operational exploit could be crafted relatively quickly.
But, they will maintain their tradition of openness by publicly publishing disclosure policy exclusions, and after all of the concerns have been identified, they will add these problems to the list. Five of the remaining fourteen vulnerabilities (CVE-2023-24072, CVE-2023-24073, CVE-2023-24074, CVE-2023-24075, and CVE-2023-24076) have surpassed Project Zero’s regular 90-day limit and have been publicly revealed in their issue tracker. The other nine vulnerabilities will be publicly disclosed at that time if they are still unfixed.
End users are strongly urged by the Google Security Team to upgrade their devices as soon as is practically practicable in order to guarantee that they are using the most recent releases, which patch security flaws that have been made public as well as those that have not been made public. It is very vital to maintain vigilance and adopt the appropriate safety measures in order to safeguard one’s personal information and electrical devices from possible security risks.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










