Apache HTTP Server is one of the web servers that is used the most often throughout the globe. It is responsible for providing power to millions of websites and apps. Recent vulnerabilities found in the server, on the other hand, have the ability to disclose sensitive information and make it easier for attackers to carry out further attacks. The Apache HTTP Server has recently been found to contain two significant vulnerabilities, both of which are detailed below. It is imperative that you rapidly upgrade Apache HTTP Server to the most recent version in order to protect your system against the vulnerabilities described.
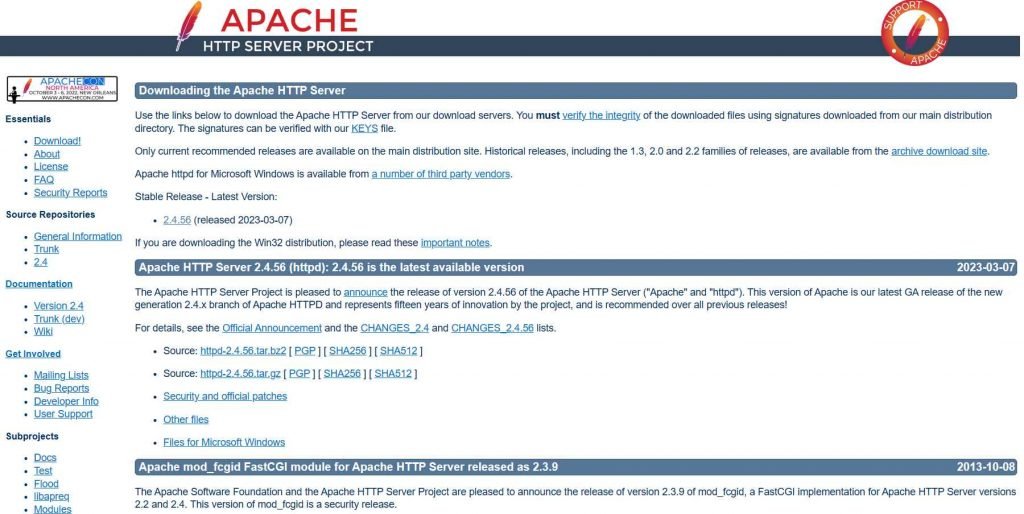
Apache HTTP Server request splitting vulnerability, CVE-2023-25690. This vulnerability is brought about by an issue that occurs in mod proxy whenever it is activated with a RewriteRule or ProxyPassMatch of some kind. This vulnerability might be used by a remote attacker to overcome access constraints in the proxy server, route undesired URLs to existing origin servers, and poison cache. Attacks using HTTP Request Smuggling are possible on Apache HTTP Server versions 2.4.0 through 2.4.55, if the server is configured with certain mod proxy settings. It occurs when mod proxy is enabled along with some form of RewriteRule or ProxyPassMatch. In these configurations, a non-specific pattern matches some portion of the user-supplied request-target (URL) data, and the matched data is then re-inserted into the proxied request-target utilizing variable substitution. This causes CVE-2023-25690 to be triggered. This might result in requests being split or smuggled, access rules being bypassed, and unwanted URLs being proxied to existing origin servers, all of which could lead to cache poisoning.
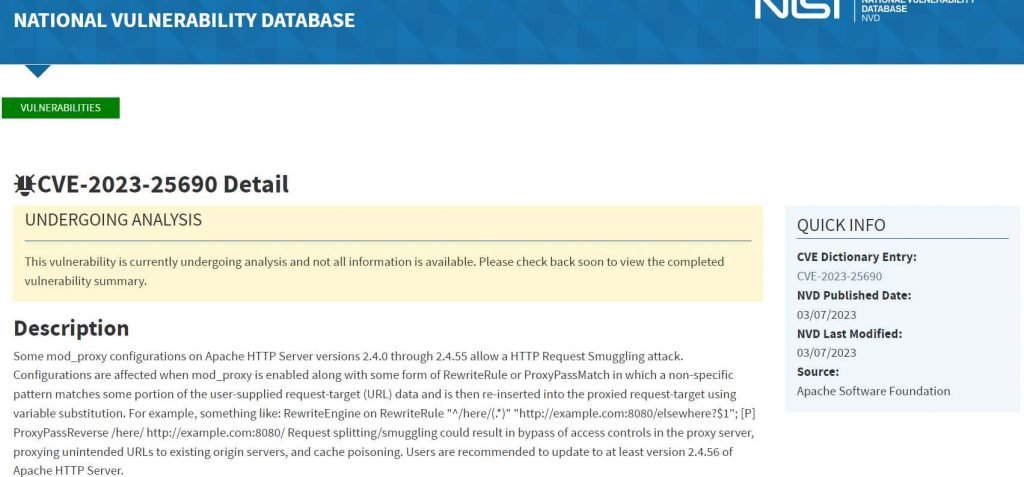
Apache HTTP Server mod proxy response splitting vulnerability, referenced as CVE-2023-27522. This is an issue in mod proxy uwsgi is the root cause of this vulnerability. This problem makes it possible for a remote attacker to insert arbitrary HTTP headers, which in turn causes the server to send a split response. This might possibly make it possible for the attacker to carry out other attacks, such as cross-site scripting or poisoning Web cache, and collect sensitive information.
Versions of the Apache HTTP Server ranging from 2.4.30 to 2.4.55 are impacted by the problem. This attack is carried out by introducing unusual characters into the header of the origin response, which has the potential to either truncate or divide the response that is sent to the client. An attacker might take use of this vulnerability to inject their own headers into the request, causing the server to produce a split response.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











