Veeam is a big vendor of backup services, as shown by the fact that it counts over 450,000 clients all over the world, among them are 81% of the Fortune 500 and 70% of the Global 2000. This makes it an appealing target. Veeam has issued a warning to its customers, advising them to update their software as soon as the company has patched a vulnerability that enables an unauthenticated user to request encrypted credentials. The warning comes from the supplier of disaster recovery and data protection software. The CVSS rating for the vulnerability in Veeam is 7.5, which may seem like an unexpectedly low score.
Users who have their Veeam environments correctly configured, such as being in an isolated network/subnet and having a firewall that is properly configured, should only have the port in question opened to other Veeam servers. This may be the case because the vulnerability sounds concerning, but users who have their Veeam environments properly configured should not have the port in question opened.
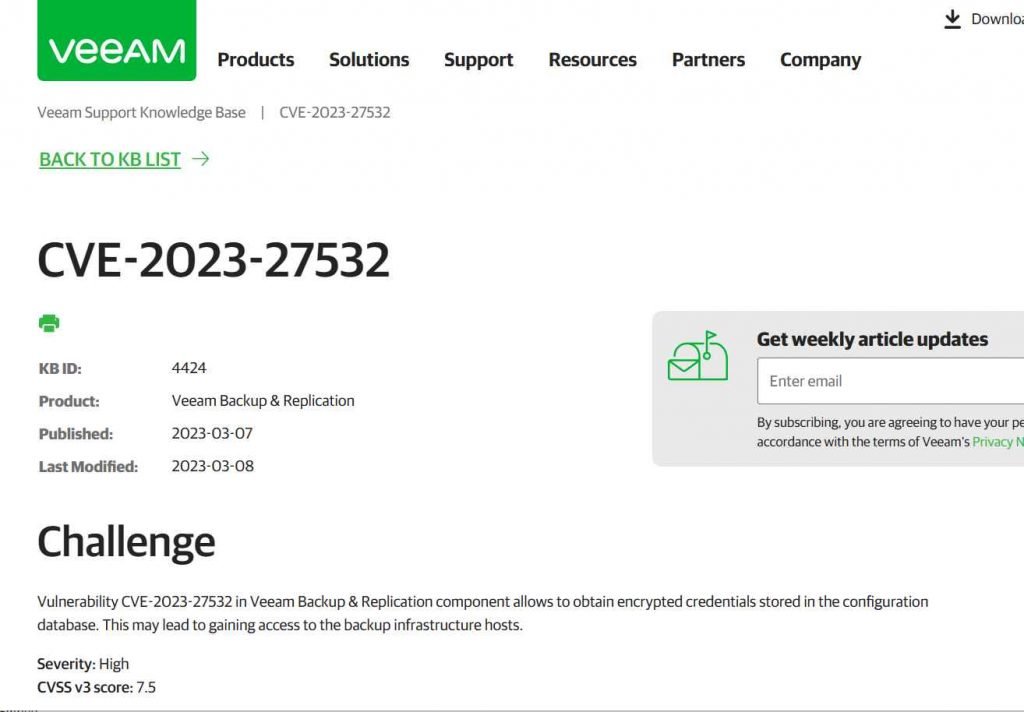
Please update to a supported version of Veeam Backup & Replication before continuing if you are using an older version of the software. If you use an all-in-one Veeam appliance that does not include any remote backup infrastructure components, you have another option available to you as a temporary remediation until the patch is installed. This option involves blocking external connections to port TCP 9401 in the backup server firewall. It is necessary for the Veeam Backup & Replication server to have the patch installed.There is little doubt that individuals that pose a threat will investigate the possibility of reverse engineering the patch in order to determine how to take advantage of the vulnerability in the very near future. The Veeam.Backup.Service.exe program, which by default listens on the TCP 9401 port, is the one that may be exploited. VEEAM has made available a patch in order to address the security flaw.
A common target is backup software. The Veeam vulnerability notice came days after CISA issued a warning about attackers using ConnectWise server backup software in the public. Attackers were essentially surfing backwards from backup systems to live settings from where they could steal sensitive data or spread malware as they pleased.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











