Hackers gained access to highly restricted corporate databases and information after stealing a master password from a top engineer’s private computer, according to a revelation made by LastPass. These hackers exploited the password to access highly restricted corporate databases. The password management provider first disclosed that it had been hacked in August of the previous year, when it reported that hackers had gained access to the development environment and stolen parts of the LastPass source code along with some confidential technical information. LastPass had said at the time that there was no evidence to suggest that the attackers had obtained access to sensitive encrypted vaults or user data. But all of this changed in December of last year, when LastPass said that hackers had obtained vault data comprising encrypted as well as unencrypted data, including information on clients.
The corporation has now revealed that the second attack was powered by information that was acquired during the first attack, as well as information obtained in prior breaches and the exploitation of a cybersecurity weakness.
This attack was directed at one of only four senior DevOps engineers who had the required high-level security authentication necessary to use the decryption keys that were required to access the cloud storage service. The perpetrators of this attack targeted the home computer of the individual they were aiming at.
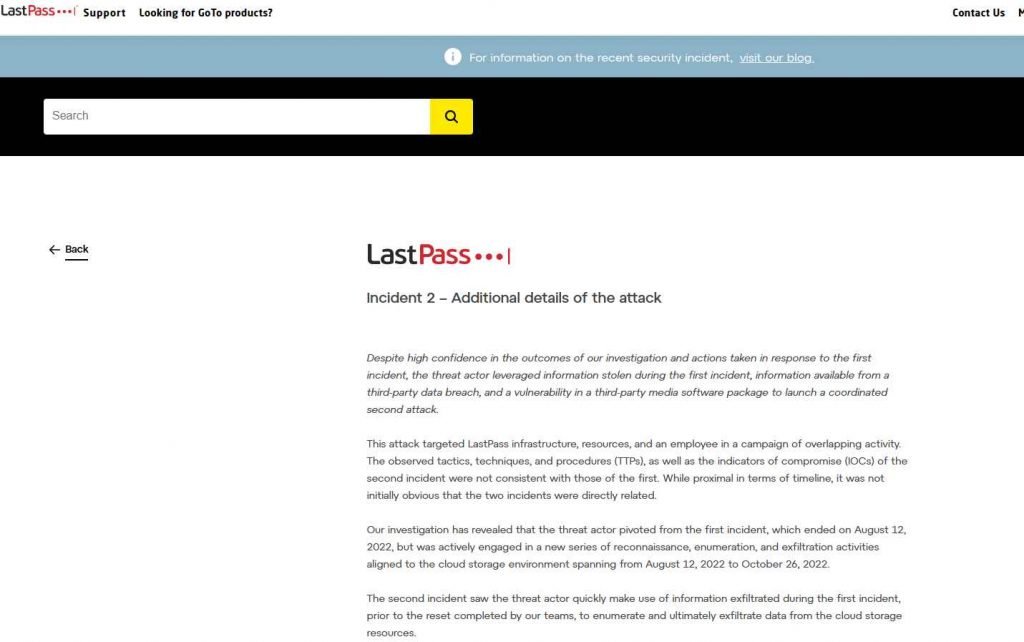
LastPass stated that the home computer of the DevOps engineer was targeted by attackers who exploited what is described as “a vulnerable third-party media software package.” This allowed the attackers to gain the privileges necessary for remote code execution. The exact details of how the attack occurred have not been disclosed. This strategy provided the potential for attackers to install keylogger malware on the home computer of the employee, which allowed them the ability to watch what the person typed on their own device. They made use of this knowledge to their advantage by stealing the master password in order to get into the company vault.
LastPass claims that this access gave the attackers access to many shared instances, “which included encrypted secure notes with access and decryption keys required to access the Amazon S3 LastPass production backups, other cloud-based storage resources, and certain associated essential database backups,” according to the company.
LastPass has said that in the aftermath of the event, it “supported the DevOps Engineer with tightening the security of their home network and personal resources.”
LastPass has strengthened its multi-factor authentication (MFA) by implementing Microsoft’s conditional access PIN-matching MFA, and the company is currently rotating critical and high-privilege passwords that were known to the attackers. This is being done in order to reduce the likelihood of an additional security breach.
Also, the corporation is investigating the possible effects that the compromise may have had on consumers. According to a statement made by Lastpass, “there are multiple other workstreams happening to better safeguard our clients,” and “it may need them to execute certain activities.”
It is strongly suggested that all clients of LastPass, including those who utilize the company management features, update their master password. It is strongly recommended that you do not use this password to protect any other online accounts. It is also advised that multi-factor authentication (MFA) be enabled to the account in order to limit the likelihood that it will be accessed.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











