Fortinet, a company that specialises in cybersecurity, has patched two serious flaws that were present in the FortiNAC and FortiWeb products it manufactures. The customers have been encouraged by Fortinet to quickly upgrade to the most recent versions that are available. The remote code execution vulnerability, which is being tracked as CVE-2022-39952 and has a CVSS score of 9.8, is located in the keyUpload scriptlet of the FortiNAC. This vulnerability could allow unauthenticated threat actors to execute unauthorized code or commands through the use of specifically crafted HTTP requests.
A vulnerability in the external control of file name or path [CWE-73] in the FortiNAC webserver may enable an unauthenticated attacker to conduct arbitrary write operations on the system. The following items are included on the comprehensive list of products that are susceptible to attacks that aim to exploit the CVE-2022-39952 flaw:
- FortiNAC version 9.4.0
- FortiNAC version 9.2.0 through 9.2.5
- FortiNAC version 9.1.0 through 9.1.7
- FortiNAC 8.8 all versions
- FortiNAC 8.7 all versions
- FortiNAC 8.6 all versions
- FortiNAC 8.5 all versions
- FortiNAC 8.3 all versions
Stack-based buffer overflows in FortiWeb’s proxy daemon, which are tracked as CVE-2021-42756 and have a CVSS score of 9.3, are another critical bug that affects the software. These buffer overflows make it possible for an unauthenticated remote attacker to execute arbitrary code by sending specially crafted HTTP requests.
Several stack-based buffer overflow vulnerabilities [CWE-121] in the FortiWeb proxy daemon may make it possible for an unauthenticated remote attacker to accomplish arbitrary code execution by submitting specially crafted HTTP requests. The following FortiWeb product versions are affected: all versions 5.x, versions 6.0.7 and below, versions 6.1.2 and below, versions 6.2.6 and below, versions 6.3.16 and below, and all versions 6.4.
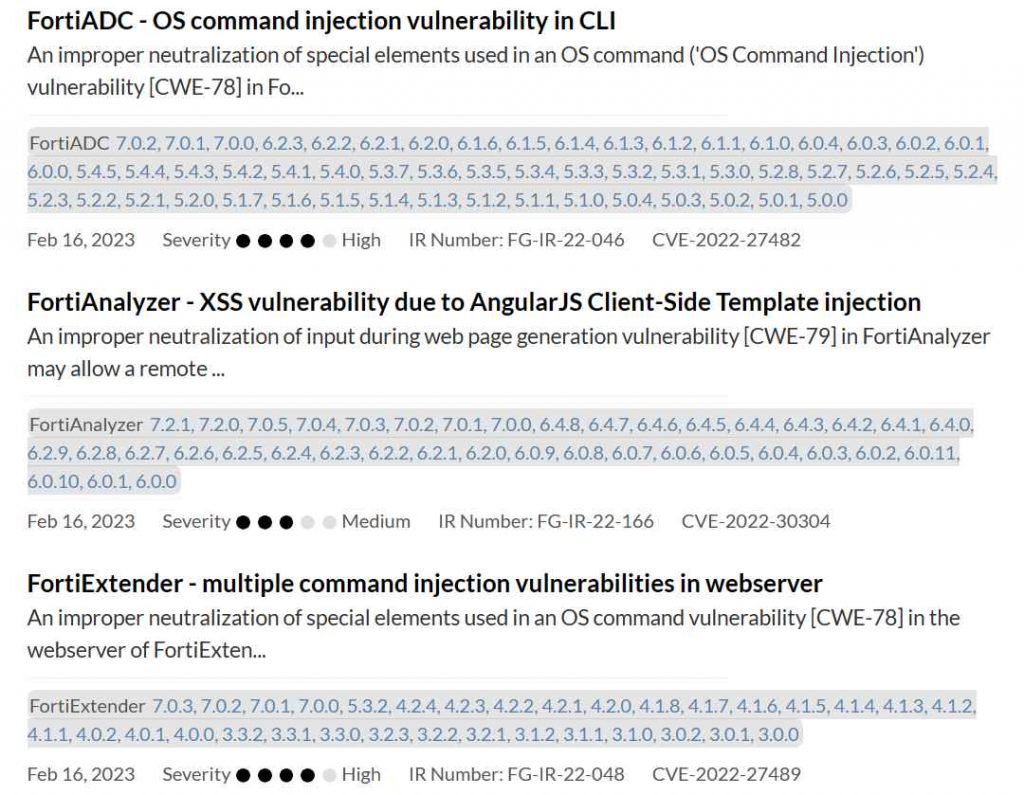
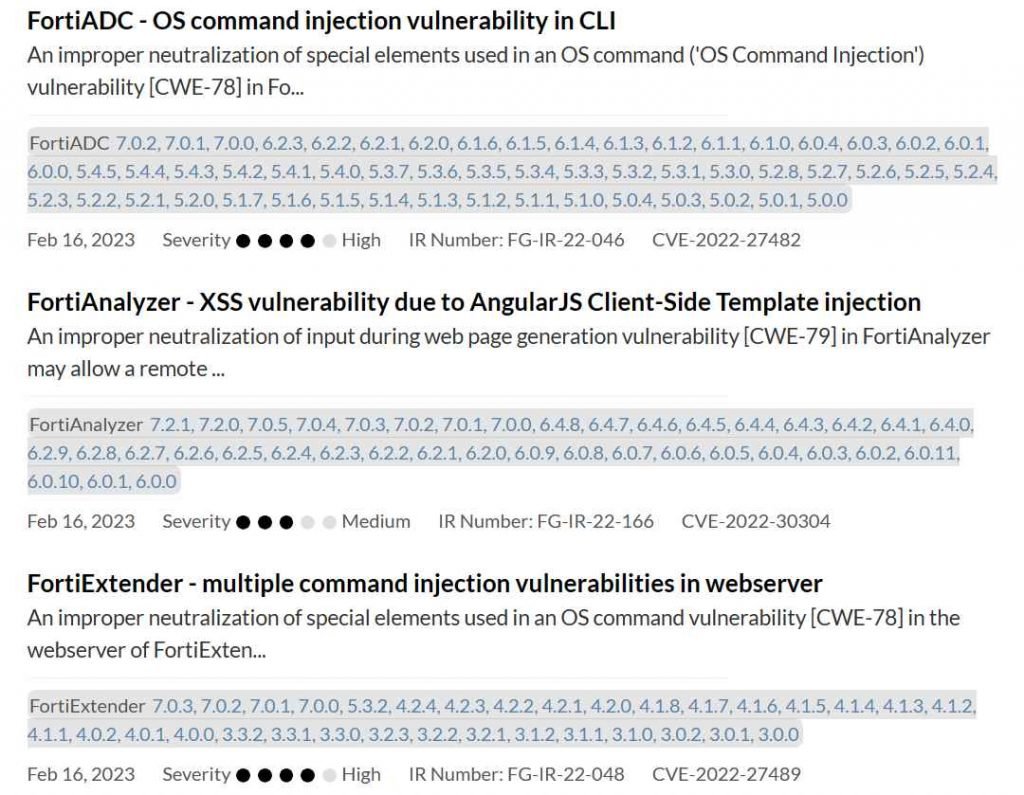
Fortinet issued security patches and urged customers to upgrade to the most recent versions of FortiADC, FortiExtender, FortiOS, FortiProxy & FortiSwitchManager, FortiWAN, FortiAnalyzer, FortiAuthenticator, FortiPortal, and FortiSandbox. FortiSandbox was also included in the list of products that needed to be updated.
Since there is now no advise or workarounds that can be used to circumvent or mitigate the reported security flaws, the only method that is suggested to address the risks is to update the products that are affected.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











