On the 30th of January, 2023, reports began to surface about a newly discovered vulnerability that affects QNAP devices. Although there is limited information regarding the vulnerability’s specifics, it has been fixed in QTS version 5.0.1.2234 and QuTS Hero version h5.0.1.2248 and affects QNAP QTS devices running versions older than 5.0.1.2234 and QuTS Hero versions older than “h5.0.1.2248.” The vulnerability affects QTS Hero versions older than “h5.0.1.2248.” This is being monitored as CVE-2022-27596 at the moment.
It has been determined by QNAP to be a significant vulnerability since it has a low attack complexity, does not need authentication, and can be exploited remotely. If the exploitation is successful, an attacker will be able to “inject malicious code.”
Due to the fact that the Deadbolt ransomware is designed to particularly target QNAP NAS equipment, it is quite probable that, in the event that an exploit is made public, the same cybercriminals would use it to distribute the Deadbolt ransomware once again.
Unfortunately, experts were only able to collect the version number from 30,520 out of the 67,415 servers that showed signs of running a QNAP-based system. Censys has seen indications that 67,415 hosts are running a QNAP-based system. However, if the advise is accurate, more than 98% of the QNAP devices that have been detected would be susceptible to this attack. They discovered that out of the 30,520 sites that had a version, only 557 were using a QuTS Hero version that was more than or equal to “h5.0.1.2248” or a QTS version that was greater than or equal to “5.0.1.2234” This indicates that the vulnerability might potentially impact 29,968 hosts.
It is possible that thousands of QNAP customers may have problems if the vulnerability is made public and then weaponized. It is imperative that everyone promptly upgrades their QNAP devices in order to protect themselves from any future ransomware operations.
The following is a rundown of the top ten countries whose hosts are running versions of QNAP that are considered to be susceptible to the CVE-2022-27596 vulnerability.
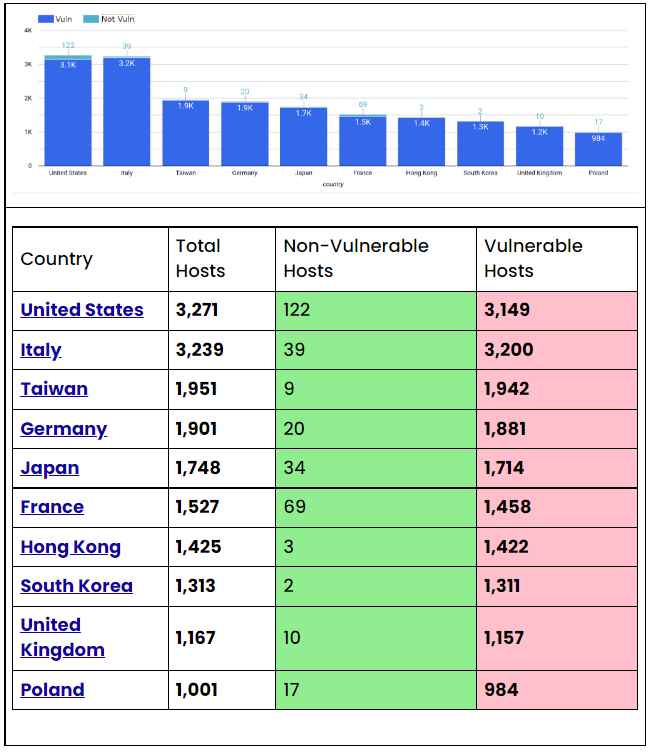
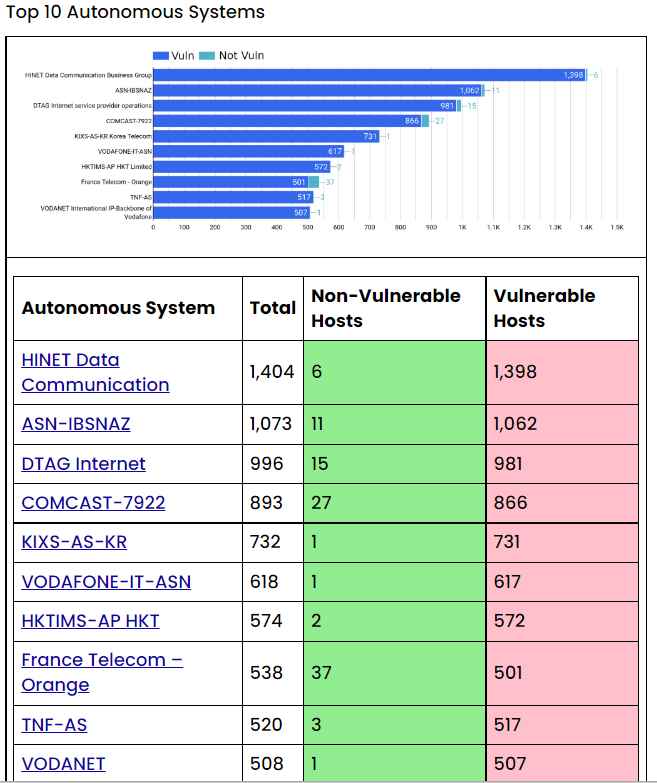
The following is a rundown of the top 10 susceptible versions of the QNAP software that we discovered when doing an auxiliary scan over the internet.
It is highly recommended by QNAP that users update to the most recent version, which users may locate on the product support status page.
We strongly suggest that you take measures to ensure that the device is not connected to the internet.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











