OneNote is one of the most popular components of the Microsoft 365 package, which the firm is still working to improve even as we speak by releasing new updates. However, as a consequence of the product undergoing continuous beta testing, hackers have discovered and exploited weaknesses in order to launch malware attacks based on phishing. Now, security pros are sounding the alarm about criminal actors that utilize OneNote files to covertly implant malware onto user machines. The attachments are sent via phishing emails.
Threat actors take advantage of the frequent feature updates that Microsoft makes to OneNote in order to install malware on users’ computers by tricking them into double-clicking on spam emails. This causes the user’s computer to automatically run a script that downloads malware from remote locations. A user’s device may be infected with malware, which can then be used not just to steal passwords but also to attack cryptocurrency wallets or even to install other software on the device without the user’s knowledge.
In the beginning, Microsoft eliminated the capability of its Office documents to make use of macros, which prevented malicious actors from using Excel and Word files to distribute malware. In addition, users are unable to open ZIP and ISO files without first going through a series of security warnings since Microsoft has restricted this functionality. Hackers have discovered methods to get around the ban on macros, which allows them to spread malware. Phishing emails may include a variety of bogus attachments, including fraudulent invoices, delivery confirmations, or alerts, amongst other things.
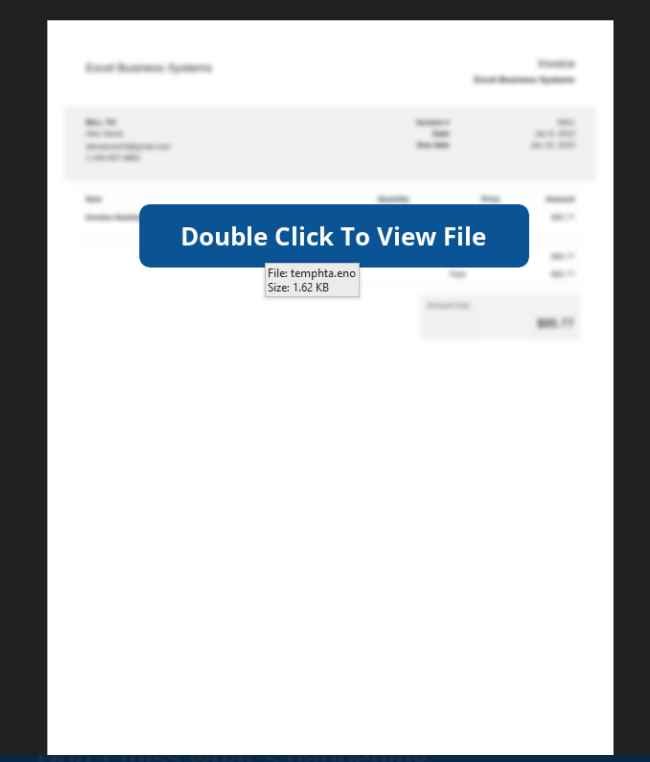
The majority of the time, the photographs in the email will be obscured, and the subject line will read, “Double Click to View File.” However, doing so actually launches a malicious Visual Basic script file, which begins contacts with a remote server to install malware, which may include a range of trojans. The file is designed to exploit vulnerabilities in Microsoft’s Visual Basic programming language.
Microsoft has already put a stop to the mining of cryptocurrencies on its network, since this activity is often associated with unlawful user access. Because of this, there has been a dramatic reduction in the deterioration and interruption of cloud services.
However, in order for users of OneNote to fully safeguard themselves, it is essential for them not to dismiss warnings that are shown by the program and to make use of multi-factor authentication, antivirus software, and firewalls whenever it is practicable to do so. In addition to this, it is essential that they refrain from downloading attachments from email URLs with which they are unfamiliar.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










