Because to the use of an obsolete third-party dependecies many ManageEngine products might make it possible for a remote attacker to execute arbitrary code on the system. This was caused by the usage of an outdated third-party component. If SAML single sign-on is presently enabled on certain products or was enabled on them in the past, an attacker might submit a SAML request to the system with an incorrect signature to execute arbitrary code if it is currently enabled. In a security alert, Zoho expressed concern by stating, “This vulnerability enables an unauthenticated attacker to execute arbitrary code.”
Late in the previous year, Zoho sent fixes and strongly recommended that users immediately patch this major vulnerability in their systems.
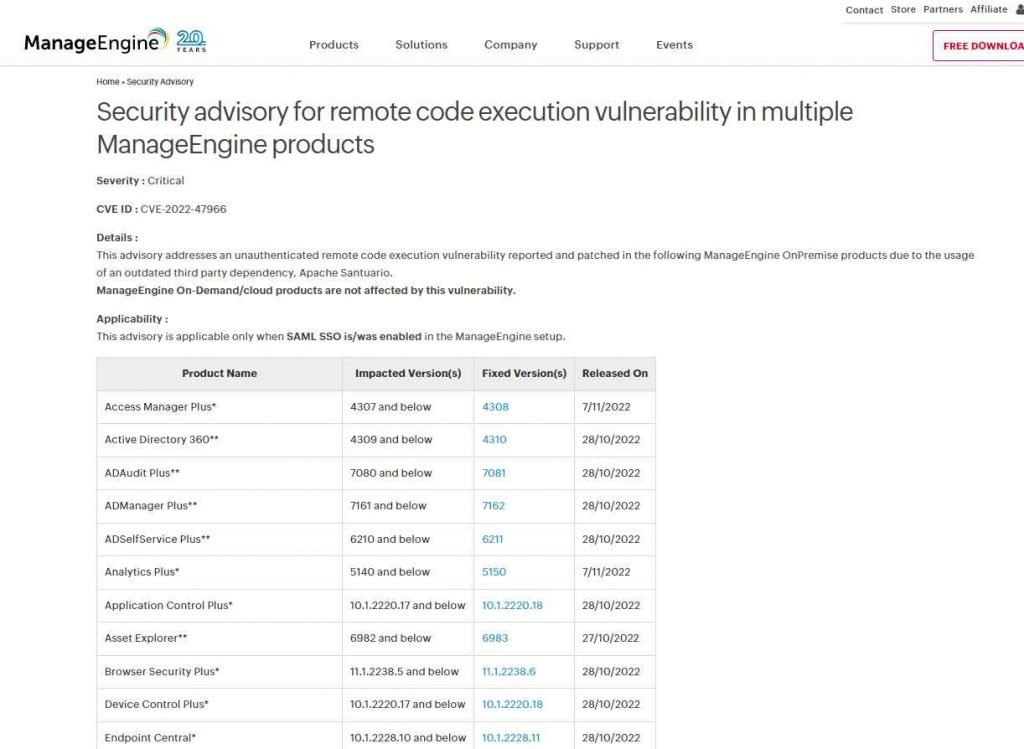
The following ManageEngine products are vulnerable to the CVE-2022-47966 exploit:
- Access Manager Plus
- Active Directory 360
- ADAudit Plus
- ADManager Plus
- ADSelfService Plus
- Analytics Plus
- Application Control Plus
- Asset Explorer
- Browser Security Plus
- Device Control Plus
- Endpoint Central
- Endpoint Central MSP
- Endpoint DLP
- Key Manager Plus
- OS Deployer
- PAM 360
- Password Manager Pro
- Patch Manager Plus
- Remote Access Plus
- Remote Monitoring and Management (RMM)
- ServiceDesk Plus
- ServiceDesk Plus MSP
- SupportCenter Plus
- Vulnerability Manager Plus
James Horseman, a member of the red team at Horizon3.ai, has published a proof-of-concept (PoC) exploit and a technical analysis for an authentication remote code execution vulnerability in Zoho’s ManageEngine products (CVE-2022-47966). He has also issued a warning to organizations that they should be prepared for “spray and pray” attacks across the internet.
Before now, James Horseman has made accessible proof-of-concept (PoC) attack code for CVE-2022-47966. Indicators of Compromise (IOCs), which are connected with the vulnerability, were previously provided by Horseman. “The data from Shodan indicates that there are likely more than a thousand instances of ManageEngine products that are now configured to communicate using SAML and are accessible through the internet,” Horseman said.
The proof of concept is only functional with software that uses Apache Santuario (xmlsec) versions less than or equal to 1.4.1. Examples of such software include ServiceDesk Plus, Endpoint Central, ADManager Plus, and ADSelfService Plus.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










