Researchers from the cyber security firm Imperva Red Team have disclosed information on a newly found and fixed vulnerability that affected over 2.5 billion Google Chrome users as well as all Chromium-based browsers such as Edge and Opera.
The vulnerability, which is identified as CVE-2022-3656, makes it possible for remote attackers to acquire sensitive user data such as passwords for cloud service providers and knowledge about cryptocurrency wallets. After further investigation, it was determined that the problem was caused by the manner in which the Chrome browser dealt with symlinks when processing directories and files.
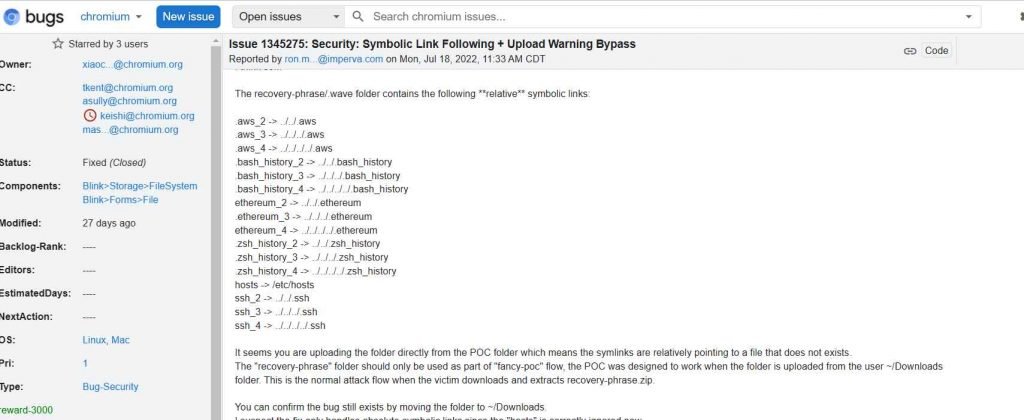
Because of this vulnerability, an attacker can use social engineering to convince a victim to visit a website that has been compromised and then download a ZIP archive file from that website. The file will contain a symlink to a valuable folder or file that is already present on the device, such as wallet keys. The user is requested to input their recovery keys whenever this file is sent back to this site as a component of an infection chain, such as a crypto wallet service.
The perpetrator of the attack may now go via the symbolic link to reach the original file that contains the key word. Researchers from Imperva developed a proof-of-concept that uses CSS trickery to change the size of the file input element. This ensures that the file uploads correctly regardless of where the folder is dropped on the page, and that information may be effectively stolen.
The researchers referred to the vulnerability as SymStealer. The problem arises when the adversary makes use of the file system in order to circumvent program constraints and access files that should not be accessed. According to the findings of Imperva’s investigation, when a user drags and drops a folder right into a file input element, the browser recursively resolves all symlinks without showing a warning message first.
To provide you with some background knowledge, a symlink is sometimes referred to as a symbolic link. It is a file that directs the operating system to another directory or file and tells it to treat it as if it were saved at the location of the symlink. In most cases, this function assists users in the process of establishing shortcuts, organizing files, and redirecting file routes.
But the study conducted by Imperva showed that this functionality had the potential to be abused in order to generate vulnerabilities such as this one, which occurred as a result of the way browsers interacted with symlinks for the processing of file and directory structures. A different term for this problem is “symbolic link following.”

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











