This flaw, which has been identified that affects the ksmbd NTLMv2 authentication in the Linux kernel, is known to quickly cause the operating system on Linux-based computers to crash. Namjae Jeon is the developer of KSMBD, which is an open-source In-kernel CIFS/SMB3 server designed for the Linux Kernel. It is an implementation of the SMB/CIFS protocol in the kernel space that allows for the sharing of IPC services and files over a network.
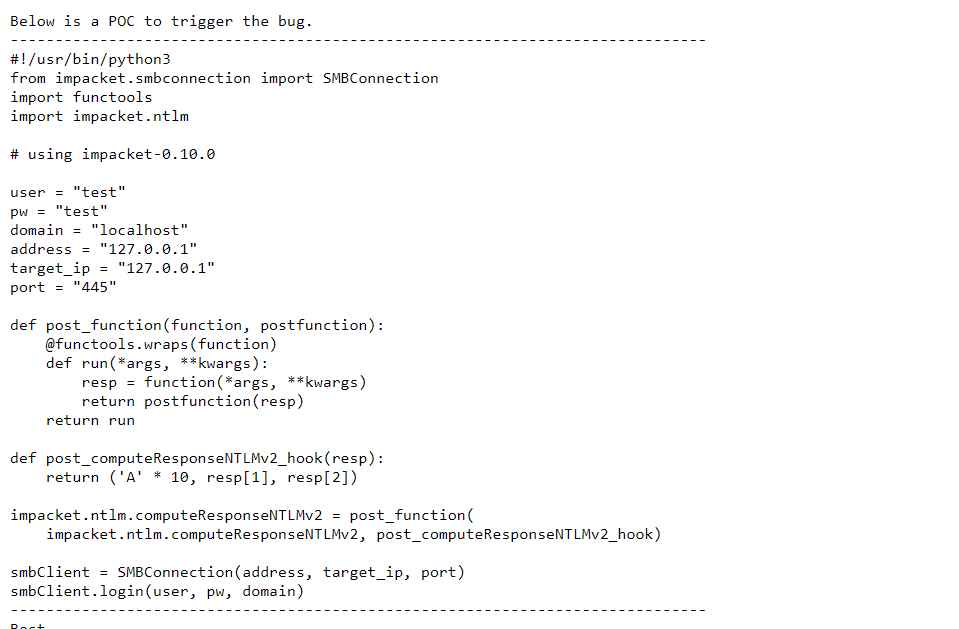
In order to take advantage of the vulnerability, you will need to transmit corrupted packets to the server, personal computer, tablet, or smartphone that you are targeting. The attack causes what is known as “a memory overflow flaw in ksmbd decodentlmssp auth blob,” which states that nt len may be less than CIFS ENCPWD SIZE in some circumstances. Because of this, the blen parameter that is sent to ksmbd authntlmv2, which runs memcpy using blen on memory that was allocated by kmalloc(blen + CIFS CRYPTO KEY SIZE), is now negative. It is important to take note that the CIFS ENCPWD SIZE value is 16, and the CIFS CRYPTO KEY SIZE value is 8. As the heap overflow happens when blen is in the range [-8, -1], we think that the only possible outcome of this problem is a remote denial of service and not a privilege escalation or a remote code execution.
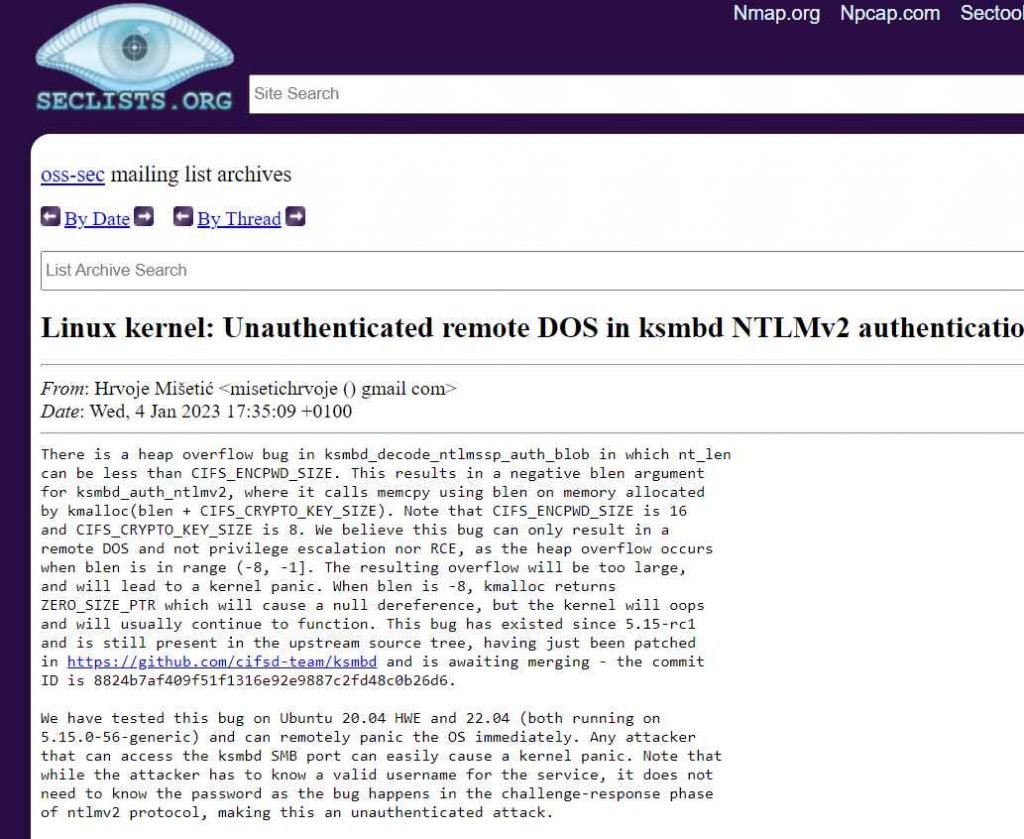
The vulnerability is caused by the way that the Linux kernel handles NTLMv2 authentication in versions 5.15-rc1 and later. The developers of the Linux kernel have not made a fix available.
A security researcher found this vulnerability, which indicates that the Linux kernel is susceptible to a potentially critical vulnerability. This vulnerability may be used by an unauthenticated attacker operating from a remote location to perform denial-of-service (DoS) attacks.
The fact that proof of concept code is presently accessible online brings the immediate threat to device owners to a somewhat higher level. Users are strongly encouraged to upgrade their Linux servers as soon as possible and to install patches for other distributions as soon as they become available.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











