Control Web Panel, which was formerly known as CentOS Web Panel and comes in both free and paid versions, is a web hosting control panel that is both open source and free to use. It was developed to allow for the quick and easy management of servers (both dedicated and virtual private servers) without the need to use an ssh console for everything. This control panel provides a large number of choices and features for the administration of servers. Some of them include admin/client access in the panel, an auto-installer for Softculous, MySQL, phpMyAdmin, Apache, SSL, and DNS, amongst others.
This vulnerability, which has been assigned the tracking number CVE-2022-44877, refers to a situation of unauthenticated remote code execution and is brought about by a flaw in the /login/index.php component of Centos Web Panel 7. A vulnerability in the Centos Web Panel 7 before version v0.9.8.1147 enables unauthenticated attackers to execute arbitrary system actions by sending specially crafted HTTP requests. The vulnerability is located in the /login/index.php component.
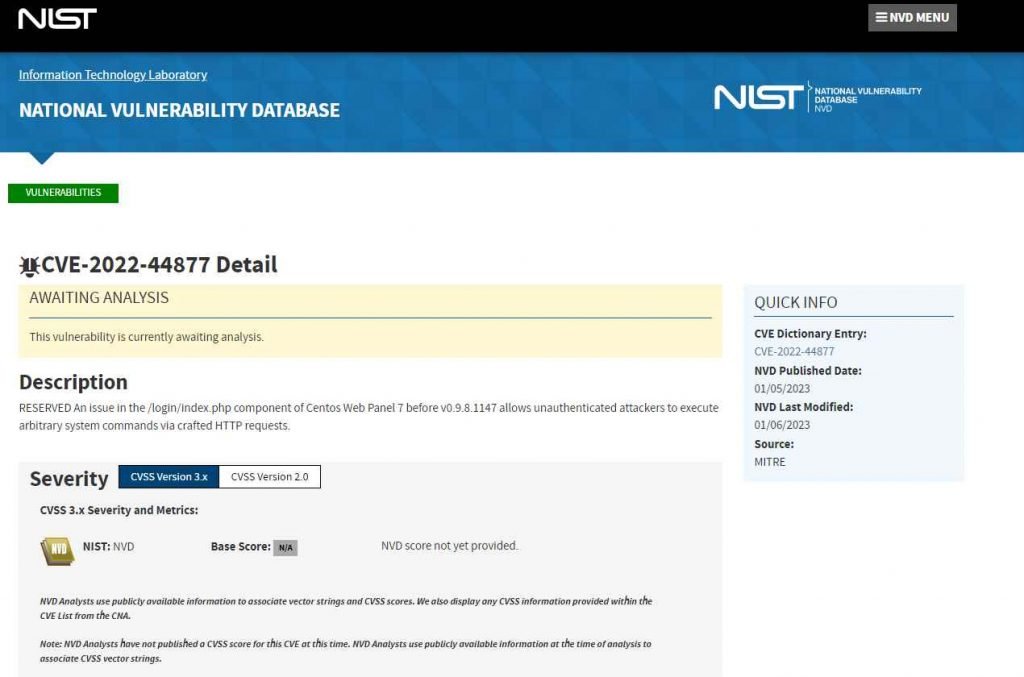
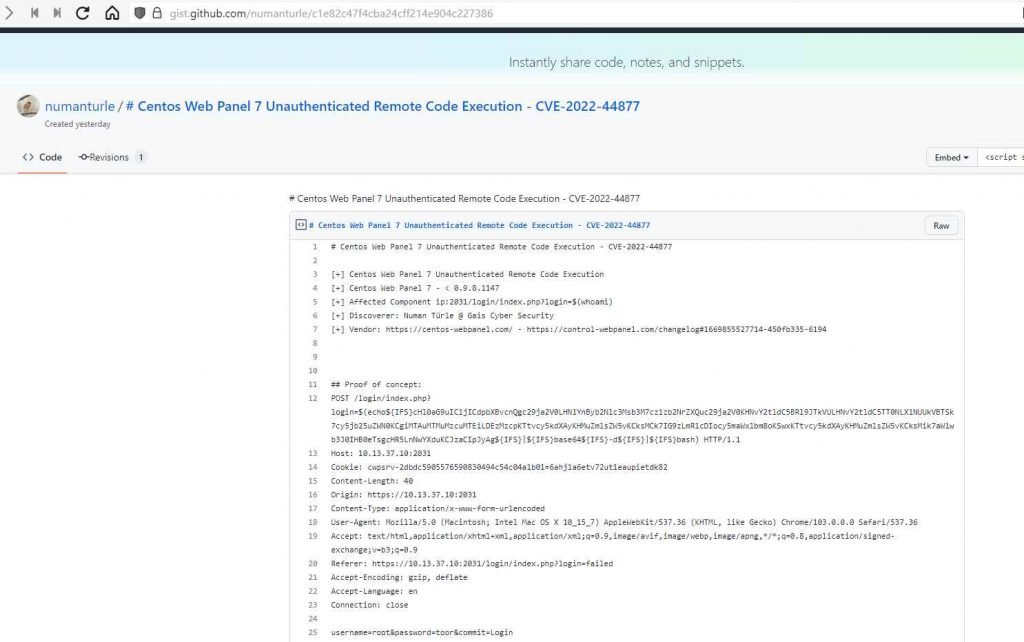
This indicates that the only thing an attacker has to do in order to exploit the vulnerability and take advantage of it is to submit a malicious HTTP request to a server that is affected by it. An attacker from a remote location may get complete remote code execution on the server if they successfully exploit the CVE-2022-44877 vulnerability.
Internet search engines such as Shodan and Censys demonstrate that more than 200,000 individual servers are using CentOS Web Panel. Recent updates implemented by CWP developers provide a fix for this issue.
The Control Web Interface (CWP) web hosting panel has a significant vulnerability that might let hackers remotely access servers, according to a security researcher who published the PoC of the exploit.
It is strongly suggested that website administrators who are running an impacted installation of the aforementioned flaws change as soon as possible to a version of Control Web Panel that is not affected by the bugs (v0.9.8.1147 or a subsequent version).

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











