Splunk Inc. is a San Francisco, California-based American software firm that develops Web-based software for finding, monitoring, and analyzing machine-generated data. Splunk Enterprise allows you to search, analyze, and visualize your data so that you can act swiftly on insights from your whole IT environment.
Splunk announced the release of a new quarterly patch set for Splunk Enterprise that includes patches for nine critical vulnerabilities last month.
The most serious of these vulnerabilities are remote code execution (RCE) problems with a CVSS score of 8.8. An flaw in the dashboard PDF creation component might enable a remote, authorized attacker to execute arbitrary code on the system, as tracked by CVE-2022-43571. Due to code injection in Splunk Enterprise’s SimpleXML dashboard, a remote attacker with low privileges may create a specially designed data package to conduct PDF export operations and ultimately gain arbitrary code execution.
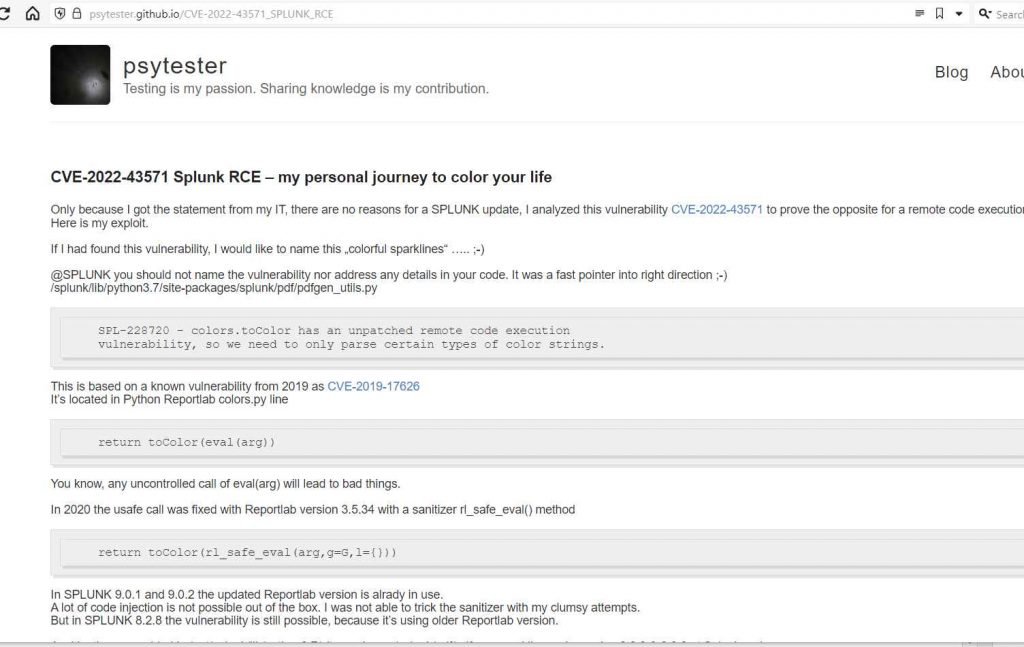
On his blog, a security researcher has provided proof-of-concept (PoC) code for the CVE-2022-43571 vulnerability, which executes code on Splunk Enterprise through the dashboard PDF generating component.
The expert’s proof-of-concept for CVE-2022-43571 includes a payload that is included on a SimpleXML dashboard with sparklines. To initiate code injection, the attacker navigates to Export–>Generate PDF
With the release of Splunk Enterprise versions 8.1.12, 8.2.9, and 9.0.2, this issue has been rectified.
It is advised that impacted customers update and upgrade to the most recent version as soon as possible.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










