Recent cyberattacks utilizing the Play ransomware were spotted targeting Exchange servers. These attacks used a novel exploit chain that circumvented the protections provided by Microsoft’s ProxyNotShell.
When the researchers were looking into Play ransomware infections, they found that the most prevalent entry vector was Microsoft Exchange, therefore they discovered that the vulnerability CVE-2022-41082 was being exploited in the wild.
They speculated that the attackers may have used the ProxyNotShell exploit chain, but they were unable to find any indication that the CVE-2022-41040 vulnerability had been exploited. Instead, they found that the OWA endpoint was being used to make POST requests.
In the interim, a threat researcher from Huntress Labs named Dray Agha was successful in obtaining attack tools from an open repository. Among these tools was a proof-of-concept script that used an unidentified OWA exploit approach as well as the CVE-2022-41082 vulnerability.
Researchers from CrowdStrike were able to deploy the OWASSRF exploit effectively against unpatched Exchange servers, but they were unable to duplicate the attack on systems that had been fixed. And because the November KB5019758 patch fixes a DLL hijacking flaw as well as a flaw whose CVSS score is CVE-2022-41040 and has been marked “exploitation more likely,” they assess that “it is highly likely that the OWA technique employed is in fact tied to CVE-2022-41080.” [CVE-2022-41080] is a vulnerability that allows remote code execution.
One of the two vulnerabilities that four researchers from 360 Noah Lab and VcsLab of Viettel Cyber Security recently combined to accomplish remote code execution on Exchange on-premises, Exchange Online, and Skype for Business Server is known as CVE-2022-41080. They informed Microsoft, which patched CVE-2022-41080 in November and the other vulnerability in December after receiving the information.
After gaining initial access using this newly discovered attack approach, the threat actor maintained access by utilizing legal Plink and AnyDesk executables, and they employed anti-forensics tactics on the Microsoft Exchange server in an effort to conceal their activities.
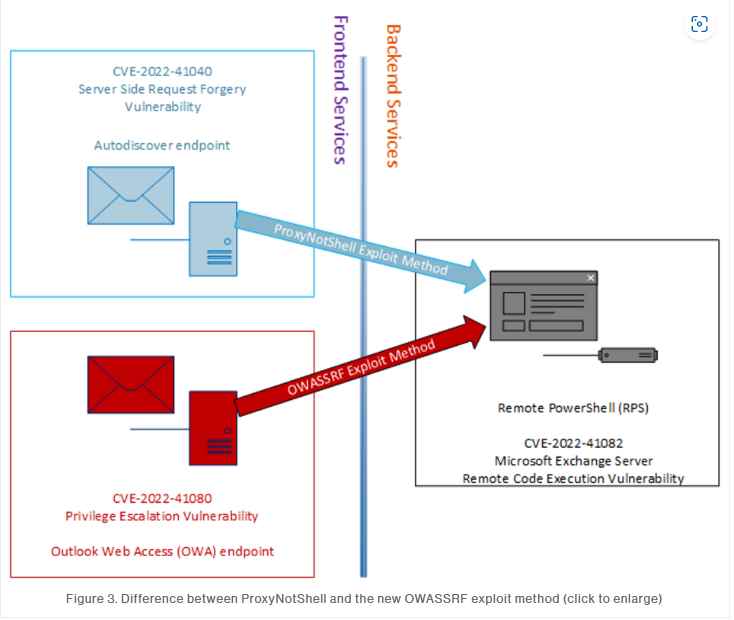
In order to gain remote code execution on Microsoft Exchange servers, cybercriminals armed with ransomware are using a newly discovered exploit chain that makes use of one of the ProxyNotShell vulnerabilities (CVE-2022-41082). The ProxyNotShell exploit chain made use of the SSRF vulnerability CVE-2022-41040, which was found in the Autodiscover endpoint of Microsoft Exchange. This new exploit chain makes use of the CVE-2022-41080 vulnerability, which allows for privilege escalation to be achieved through Outlook Web Access (OWA).
Implementing the fixes that were made available for Microsoft Exchange in November 2022 is the only way to stop the exploit chain that has been given the name OWASSRF by the researchers.
Recommendations
Because the URL rewriting mitigations for ProxyNotShell are ineffective against this attack approach, companies and other organizations should implement the patches that were released on November 8, 2022 for Exchange in order to avoid exploitation. In the event that you are unable to quickly implement the KB5019758 patch, you should deactivate OWA until the fix can be applied. When it is feasible to do so, follow the instructions provided by Microsoft and turn off remote PowerShell for users who are not administrative.
Install sophisticated endpoint detection and response (EDR) tools on each and every endpoint in order to identify online services that are generating command line or PowerShell processes.
Think about applying controls at the application level, such as web application firewalls.
Be certain that the X-Forwarded-For header is set up to report the actual external IP addresses of requests made to proxied services.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











