The newly discovered information stealer known as “RisePro” is being delivered through the pay-per-install malware downloader service known as “PrivateLoader,”.
RisePro is a backdoor that is written in C++ and it gathers potentially sensitive information from workstations that have been hacked. It then tries to exfiltrate this information as logs.
Malware known as log (or information) stealers are a sort of Trojan that collects data with the intention of transmitting it to an adversary. The credentials that are often targeted are those that are stored in browser profiles.
The well-known malware families Redline, Raccoon, Vidar, Metastealer, Eternity, and Prynt are all examples of this kind of malicious software.
Risepro is the name of the most recent piece of malware that steals information, and the evidence that has been gathered as a result of its usage is already at more than 2200 inside the Russian Market market place. On December 9, 2022, the vendor Mo####yf placed the first piece of proof on the market for public consumption.
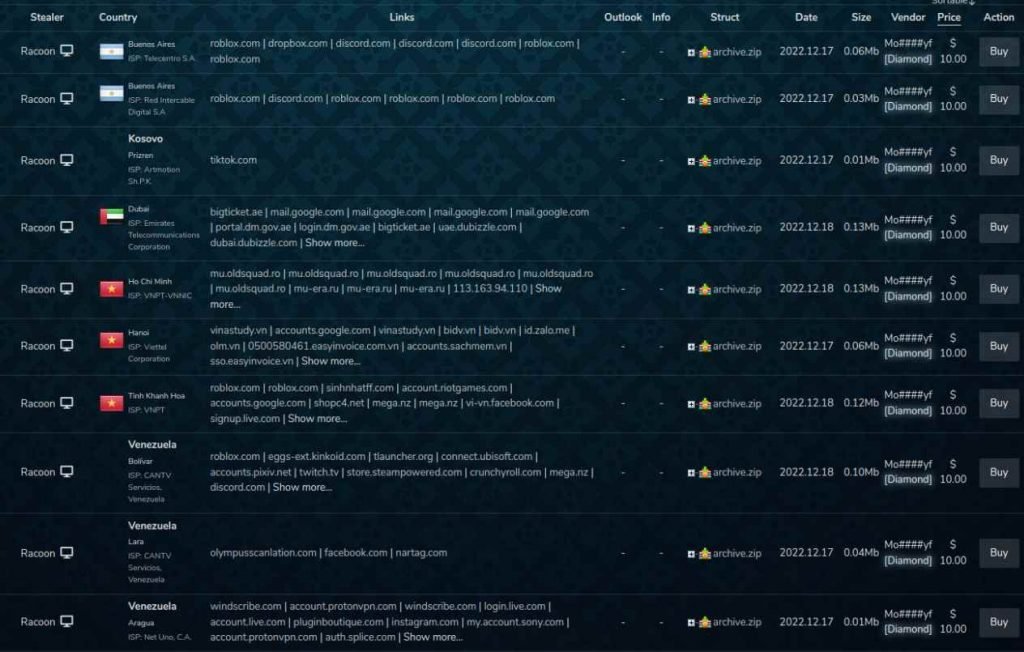
The structure that can be seen inside the record is quite comparable to the structure that can be seen within records that were created as a result of the actions of other malware.
Within the Joe Sandbox, further information on the virus has been discovered, and may be seen at https://www.joesandbox.com/analysis/731772/1/html. The MD5 hash of the malicious software and the IP address of the command and control (C2) server were the pieces of information that proved to be the most helpful.
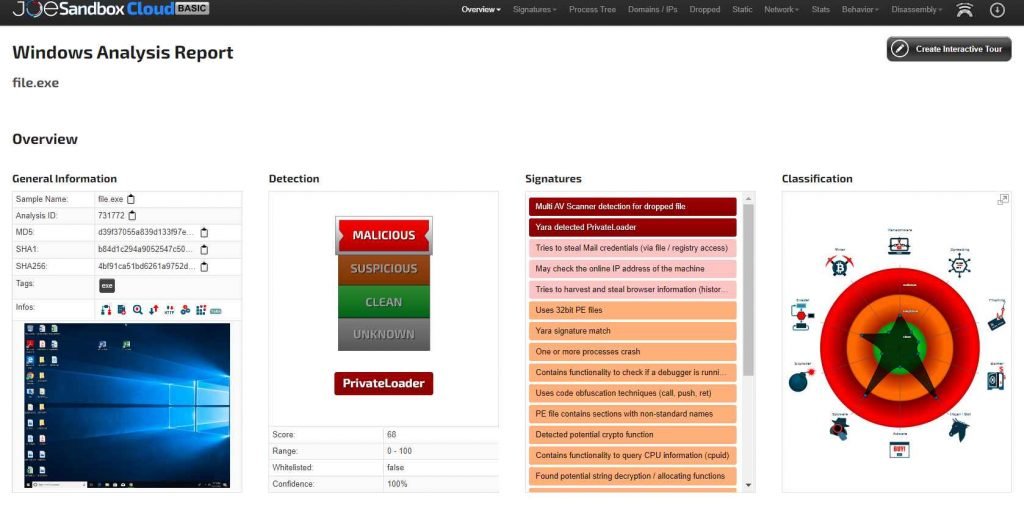
According to Flashpoint, the malicious software seems to have been modeled after Vidar stealer, a piece of code that has been the subject of research on many occasions in the past.
Vidar is a fork of the Arkei stealer itself, and it is notorious for downloading a number of dependencies and configuration settings from its command-and-control (C&C) server. Vidar is a fork of the Arkei stealer. The information stealer was deciphered in 2018, and before to that, multiple clones of it were seen. These clones included the ‘Oski’ and ‘Mars’ thieves.
Analysis of the malware reveals that RisePro is very likely a clone of Vidar since it was seen leveraging dropped dynamic link library (DLL) dependencies in the same way that Vidar does. On the other hand, RisePro has characteristics that are shared with other information stealers currently available.
According to Flashpoint, Russian Market has a listing of more than 2,000 logs that were allegedly exfiltrated using RisePro. This fact may suggest that the information stealer is growing popularity among hackers.
Malware of this kind is updated often in order to thwart anti-malware systems that rely on signature detection. Even if a scan is performed today that would identify it, this does not indicate that your information was not taken the day before. There is no clear indication of the identity of the attacker or the software that was used to infect the system.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











