Researchers from HackSys Inc. have provided further information on a security issue in the code execution of Foxit PDF Reader.
On vulnerable installations of Foxit PDF Reader 11.2.1.53537, remote attackers are able to carry out the execution of arbitrary code thanks to this issue. Exploiting this issue requires user involvement in the sense that the victim must visit a malicious website or open a malicious file in order for the attack to work. The exact vulnerability may be found in the way that Doc objects are handled. The problem stems from the fact that there was no attempt made to verify that an object really existed before conducting actions on the object. An adversary may exploit this vulnerability to run code in the context of the currently running process if they are successful.
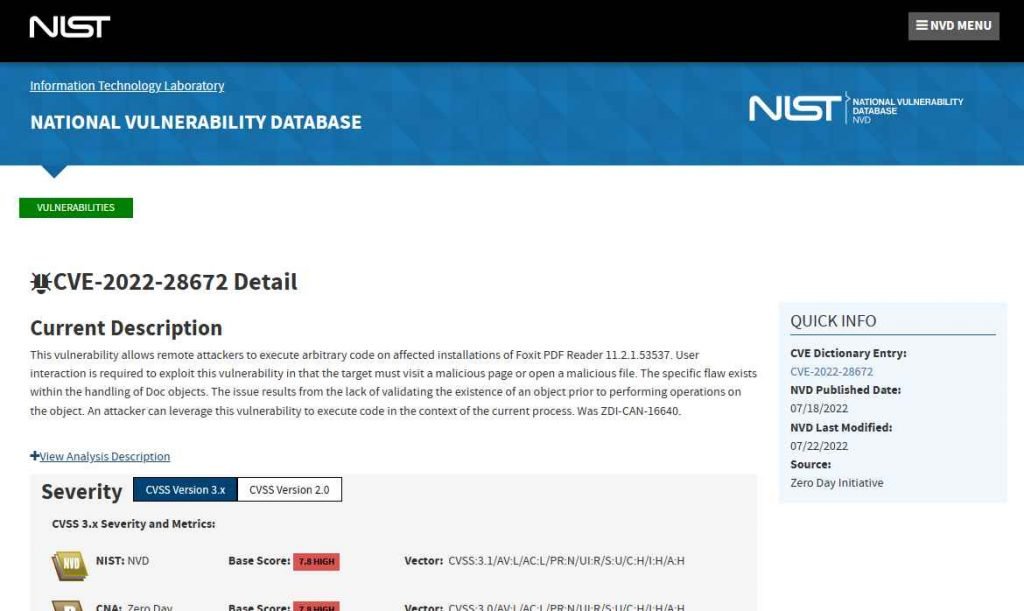
According to the CVSS vulnerability scoring methodology, the vulnerability that is being tracked under the identifier CVE-2022-28672 has a high severity level of 7.8. The vulnerability was fixed in the latest security update for Foxit PDF Reader, version 10.1.8, which was made available on June 21, 2022.
An in-depth examination of the issue and publicly revealed CVE-2022-28672 PoC code was carried out by researchers Krishnakant Patil and Ashfaq Ansari of HackSys Inc.
The processing of Doc objects has a use-after-free error, which is the root source of the problem. When a virtual method is run in Foxit Reader, it is feasible to cause the program to crash at a certain position if the heap spraying process is properly controlled using the script that is given. The attacker is granted the ability to control the state of the object and possibly execute arbitrary code inside the context of the Foxit process as a result of this vulnerability.
At this time, the researcher publishes the proof-of-concept code for CVE-2022-28672 on Github. This code enables remote code execution in susceptible instances of Foxit PDF Reader. This vulnerability, which has since been fixed, had the potential to allow an attacker to execute arbitrary code. Users are strongly encouraged to upgrade to the most recent version of the program as quickly as they can.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











