Platform certificates, also known as platform keys, are used by OEM Android device makers to certify the core ROM images of their devices. These images include the Android operating system and any related applications.
The application signing certificate that was used to sign the “android” program that was stored on the system image is known as a platform certificate. The “android” program runs with a highly privileged user id called android.uid.system and retains system rights, including permissions to access user data. This is because it has the ability to hold the android.uid.system user id.
If applications, even malicious ones, are signed with the same platform certificate and assigned the highly privileged ‘android.uid.system’ user id, then these applications will also gain system-level access to the Android device. This access can be gained by signing the application with the platform certificate.
An abusive usage of platform keys was detected by Lukasz Siewierski, a Reverse Engineer in Google’s Android Security team. This information was published in a report that is currently available to the public on the Android Partner Vulnerability Initiative (AVPI) issue tracker.
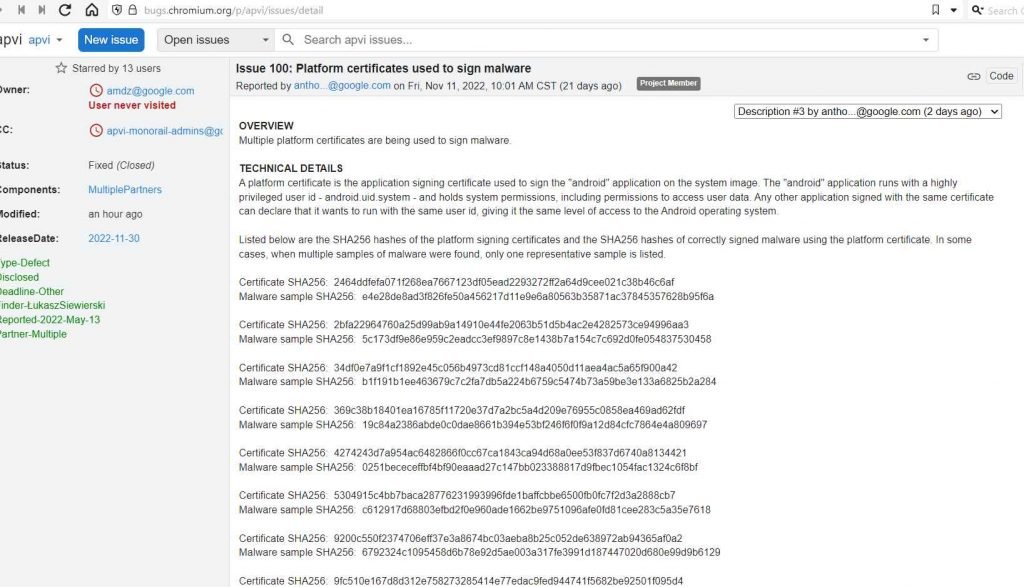
Siewierski discovered many malware copies that were signed using these 10 Android platform certificates. He supplied the SHA256 hashes for each of the samples as well as the certificates that were digitally signed.
There is no evidence available at this time on the circumstances that led to these certificates being misused to sign malware. It is unknown if one or more threat actors stole the certificates, or whether an authorized employee signed the APKs using the vendor keys.
In addition, there is no information on the locations of these malware samples, such as whether they were discovered on the Google Play Store, if they were spread via third-party shops, or whether they were used in malicious activities.
Google notified all impacted vendors of the misuse and gave them advice to avoid such problems by rotating their platform certificates, looking into the breach to determine how it occurred, and limiting the amount of applications signed with their Android platform certs.
There is no evidence to suggest that this malicious code was ever distributed via the Google Play Store. Always and without fail, our standard piece of advice to users is to check that they are on the most recent version of Android.
Using APKMirror to search for apps that have been signed with these certificates that could have been compromised is a simple way to get an overview of all Android apps that have been signed with these certificates.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











