Earlier we published an article that provided details of a data breach that occurred on Twitter and affected 5.4 million accounts. Now, the exact same information has been published on a hacker forum that emerged as an alternative to the well-known and large Raidforums. Having said that, there is more to it. Due to the fact that Twitter is now at the center of yet another dispute, it would seem that the year 2022 will not be kind to the social media platform. On November 23, a cyber security researcher located in Los Angeles made public the news that Twitter had been the victim of a major security breach, which purportedly impacted millions of users in both the United States and the European Union.
On the other hand, it is not clear if this security breach is the same as the one that happened in July of this year and was also acknowledged by Twitter, or whether this security breach is entirely unique. Twitter has not commented on this question.
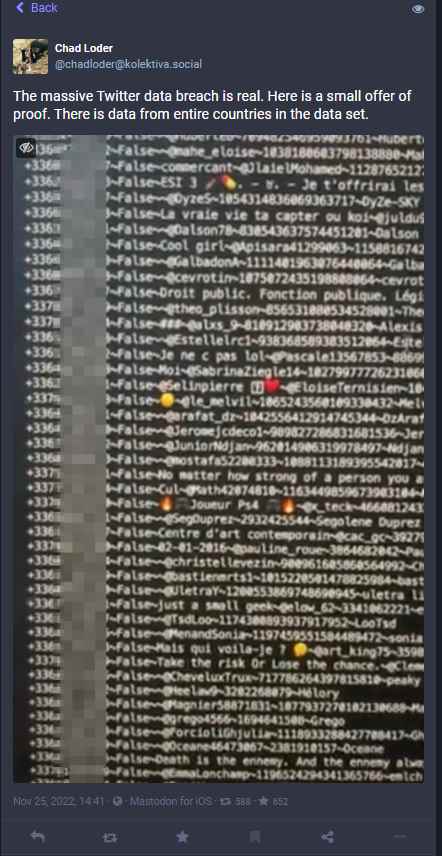
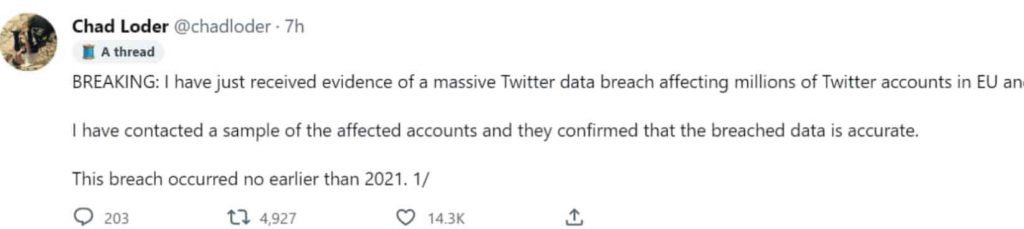
Chad Loder sent a warning to the followers of his now-closed Twitter account about the data breach, which he alleged happened “no earlier than 2021” and “has not been disclosed previously.” He indicated that he had seen the stolen data in the supposed breach and had talked to the possible victims who verified that the breach data was “correct.” He also claimed that he had seen the stolen data in the alleged breach. The researcher said on his Mastodon page that according to his study, it is likely that there are tens of millions of impacted accounts, and there is a possibility that there are hundreds of millions of affected accounts.
According to Loder, there is no way that this could have been the same breach since Twitter “lied” about the incident that occurred in July. In addition to this, he said that the material in question was presented in a “totally different way” and that it had “differently impacted accounts.” Within twenty-four hours of Loder tweeting on this topic, his account on Twitter was suspended on the grounds that he had “violated the Twitter rules.”
It is quite probable that both breaches took use of the same vulnerability, which was discovered and disclosed for the first time in January. It enabled anybody to locate the Twitter handle that was linked with a phone number or email address by entering the number or address. This is a feature that Twitter uses as an internal identity, but it can be easily transformed to a Twitter ID if you so want. Twitter recognized the existence of the vulnerability at the time and indicated that it had been fixed. However, the company did not identify anybody taking use of the weakness. On the other hand, Restore Privacy later revealed that a hacker had taken use of the weakness to compile a dataset that included the Twitter handles, email addresses, and phone numbers of millions of accounts. The data covers users of Twitter in the United Kingdom, almost every countries in the European Union, and some sections of the United States.
Affected is any Twitter account that, inside its “discoverability” settings, has selected the option to “let people locate you by phone number.” This option is not really obvious unless you go fairly far into Twitter’s settings, where it is also on by default. When the current events are taken into consideration, it becomes quite clear that more than one malicious actor gained access to these records. According to the reports, they were provided a dataset that had information that was quite comparable but presented in a different style. It is possible that the information may be sold to hostile parties who would then use the data for advertising reasons or maliciously target specific accounts, such as those belonging to celebrities.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











