Google sent out emergency patches for its Chrome web browser on Thursday to fix a security hole that the company says is being used in the wild.
Google called the high-risk bug a GPU heap buffer overflow and gave it the number CVE-2022-4135. On November 22, 2022, Clement Lecigne of Google’s Threat Analysis Group is said to have found the flaw and told Google about it.
It is common for buffer overflows to be able to be utilized to run arbitrary code, which is often beyond the purview of the implicit security policy of a program. Not only may heap-based overflows be used to access sensitive user data, but they can also be used to replace function pointers that may be residing in memory, which then directs execution to the malicious code of the attacker. Even in programs that do not overtly employ function pointers, the run-time will often nonetheless leave a large number of them in memory. A buffer overflow situation is known as a heap overflow condition when the buffer that may be overwritten is allocated in the heap section of memory. This often indicates that the buffer was created with the help of a function such as malloc (). Because to the vulnerability, a malicious hacker who had already gained control of the renderer process may theoretically escape the sandbox by using a specially constructed HTML page.
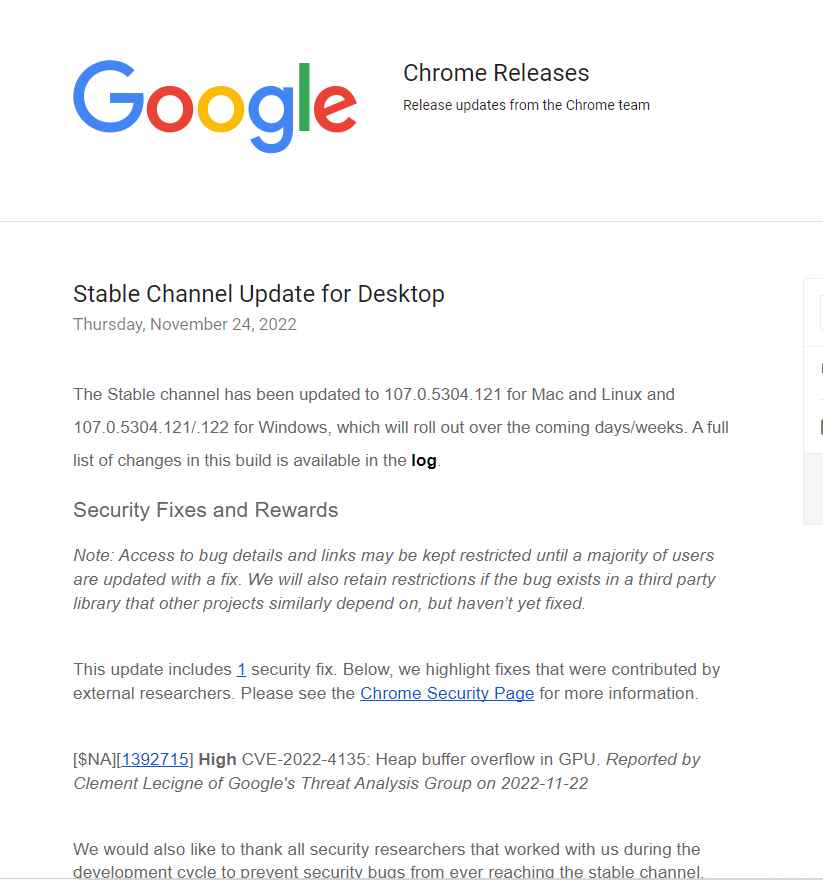
Google said in an alert, “Google is aware that an exploit for CVE-2022-4135 exists in the field,” without providing any other details on how the security flaw was exploited in attacks or who may have weaponized it.
Google has provided an urgent security update to patch this vulnerability in order to assure user safety; the relevant version number for Mac, Linux, and Windows is Google Chrome 107.0.5304.121/.122.
Google Chrome users may use the About page in the settings to see the current version number and to automatically check for updates. The online installation package may be automatically updated if the user installs it. The user must manually download the latest version to update if they utilize the offline installation package. As soon as the solutions become available, users of Chromium-based browsers including Microsoft Edge, Brave, Opera, and Vivaldi are encouraged to install them.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











