The local privilege escalation vulnerability in the Linux Kernel was reported by Redhat, and its CVE code is 2022-3977. The problem is that the most recent Linux kernel upstream contains a use-after-free vulnerability called mctp sk unhash that may be exploited to elevate privileges to root. When a program tries to utilize memory that has been released or no longer assigned to it after it has been given to another application, it is known as a use-after-free vulnerability. In cyber attack situations, this might result in arbitrary code execution or provide an attacker access to remote code execution capabilities. It can also cause crashes and unintentional data overwriting.
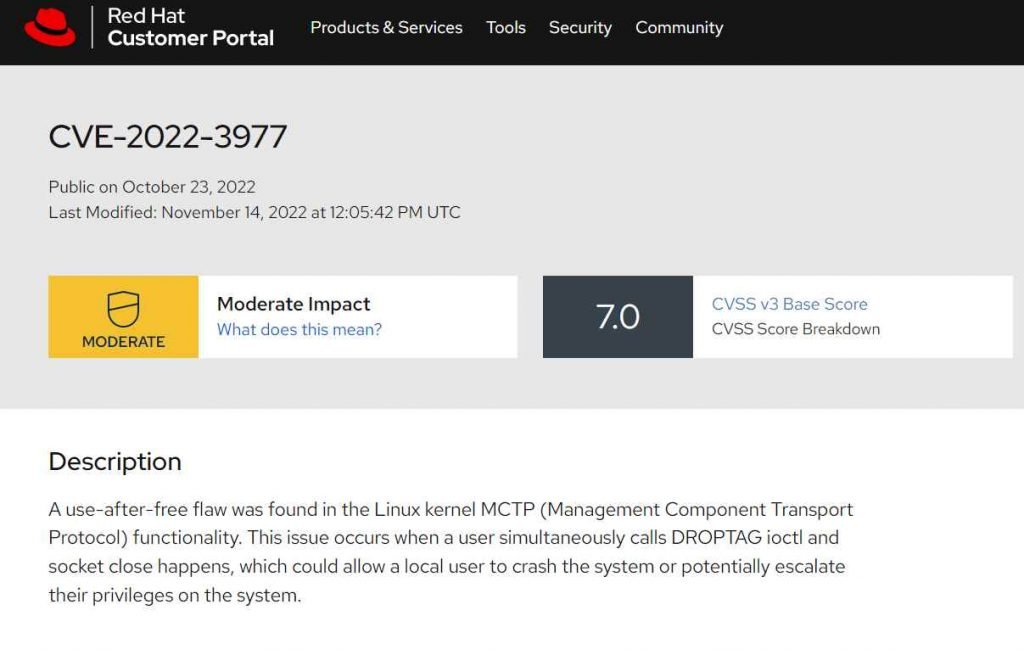
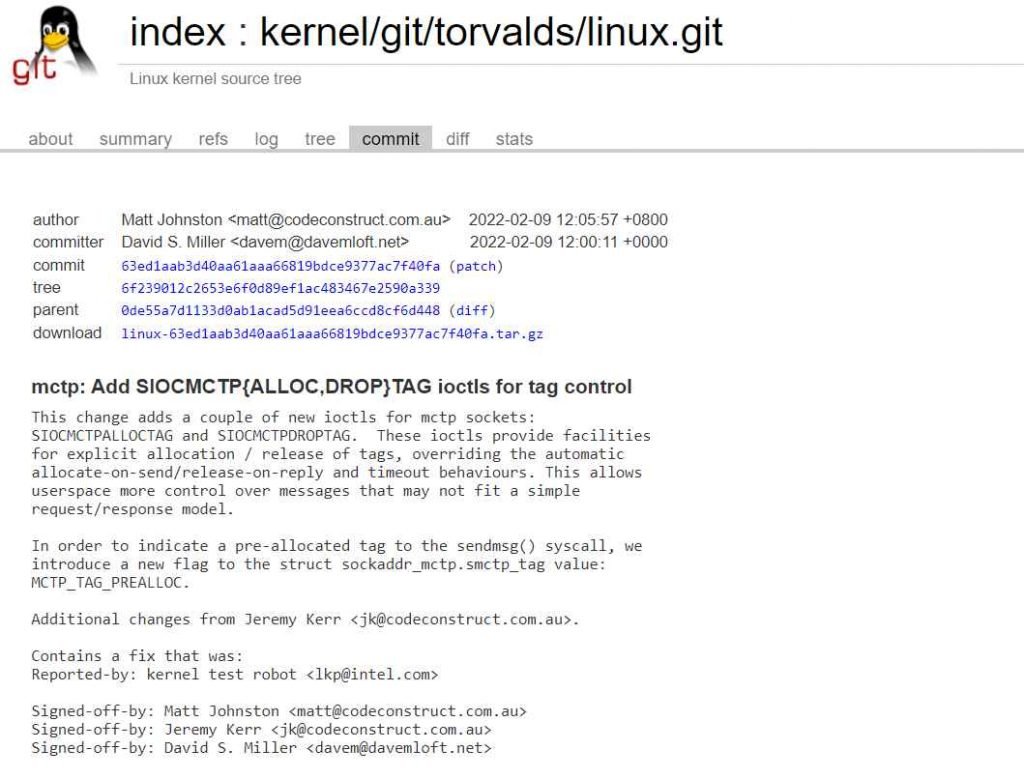
The concurrent DROPTAG ioctl and socket close may result in a race scenario, which is the cause of the vulnerability . The Active Defense Lab of Venustech has reported the vulnerability . “An unprivileged user duplicated it using new namespaces. Local Privilege Escalation would result from it (LPE). It was first made available in v5.18.0; the commit is 63ed1aab3d40aa61aaa66819bdce9377ac7f40fa. It had an impact on stable and upstream v6.0.0. The mctp kernel module, however, is not loaded automatically, according to the seclists website.
With the help of latest commit, the Linux kernel’s CVE-2022-3977 vulnerability was patched. Currently, security fixes have been formally released by Linux kernel maintainers. It is advised that users update Linux servers right away and install other distro’s fixes as soon as they become available.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











