With the use of the Splunk software, real-time data can be collected, indexed, and corroborated in a searchable repository from which graphs, reports, alarms, dashboards, and visualizations may be produced. Machine data is used by Splunk to find patterns in data, provide metrics, identify issues, and provide information for business operations.
On November 2, Splunk announced the availability of a new batch of quarterly patches for Splunk Enterprise that resolve eight high-severity vulnerabilities.
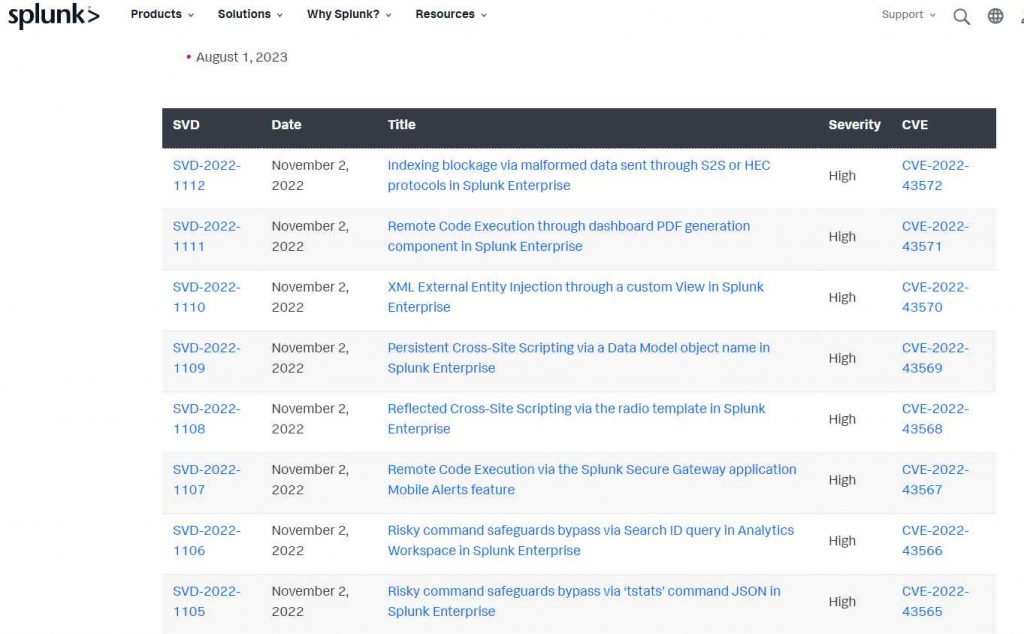
1. CVE-2022-43572 – Indexing blockage via malformed data sent through S2S or HEC protocols in Splunk Enterprise
CVSSv3.1 Score: 7.5, High
Description
Sending a corrupt file to an indexer over the Splunk-to-Splunk (S2S) or HTTP Event Collector (HEC) protocols causes a blockage or denial-of-service, prohibiting further indexing, with Splunk Enterprise versions below 8.2.9, 8.1.12, and 9.0.2.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
2. CVE-2022-43571 – Remote code execution using the Splunk Enterprise dashboard PDF creation component
CVSSv3.1 Score: 8.8, High
Description
The dashboard PDF generating component in Splunk Enterprise versions 8.2.9, 8.1.12, and 9.0.2 and earlier allows an authorized user to execute arbitrary code.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
3. CVE-2022-43570 – XML External Entity Injection in Splunk Enterprise using a personalized view.
CVSSv3.1 Score: 8.8, High
Description
An authorized user can do an extensible markup language (XML) external entity (XXE) injection using a custom View in Splunk Enterprise versions below 8.1.12, 8.2.9, and 9.0.2. Splunk Web embeds wrong documents into an error as a result of the XXE injection.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
4. CVE-2022-43569 – Persistent Cross-Site Scripting in Splunk Enterprise through a Data Model object name
CVSSv3.1 Score: 8.0, High
Description
An authorized user may inject and save arbitrary scripts that may result in permanent cross-site scripting (XSS) in the object name of a Data Model in Splunk Enterprise versions earlier than 8.1.12, 8.2.9, and 9.0.2.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
5. CVE-2022-43568 – Reflected Cross-Site Scripting in Splunk Enterprise’s radio template
CVSSv3.1 Score: 8.8, High
Description
When output mode=radio is selected, a View in Splunk Enterprise versions below 8.1.12, 8.2.9, and 9.0.2 causes reflected cross-site scripting through JSON in a query parameter.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
6. CVE-2022-43567 – Remote Code Execution via the mobile alerts function of the Splunk Secure Gateway application
CVSSv3.1 Score: 8.8, High
Description
An authorized user can remotely execute any operating system command in Splunk Enterprise versions below 8.2.9, 8.1.12, and 9.0.2 by sending specially designed queries to the mobile alerts function in the Splunk Secure Gateway app.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
7. CVE-2022-43566 – Risky command security bypassed by the Analytics Workspace’s Search ID query in Splunk Enterprise
CVSSv3.1 Score: 7.3, High
Description
An authorized user can perform dangerous commands in the Analytics Workspace by exploiting a higher privileged user’s access in Splunk Enterprise versions below 8.2.9, 8.1.12, and 9.0.2 in order to get around SPL protections for risky commands. Due to the vulnerability, the attacker must phish the victim by convincing them to send a request through their browser. The vulnerability cannot be used arbitrarily by the attacker.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.
8. CVE-2022-43565 – Risky command protections in Splunk Enterprise are circumvented by the ‘tstats’ command JSON.
CVSSv3.1 Score: 8.1, High
Description
he way the ‘tstats’ command handles Javascript Object Notation (JSON) in Splunk Enterprise versions below 8.2.9 and 8.1.12 enables an attacker to go around SPL protections for dangerous commands. Due to the vulnerability, the attacker must phish the victim by convincing them to send a request through their browser.
Mitigation
For Splunk Enterprise, upgrade versions to 8.1.12, 8.2.9, 9.0.2, or higher.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











