The Windows Common Log File System (CLFS) Driver has an elevation of privilege vulnerability identified as CVE-2022-37969 (CVSS score: 7.8). For reporting this vulnerability, Microsoft gave credit to Quan Jin of DBAPPSecurity, Genwei Jiang with Mandiant, FLARE OTF, CrowdStrike, and Zscaler ThreatLabz. Software clients can make advantage of the general-purpose logging service known as the Common Log File System (CLFS) whether they are operating in kernel mode or user mode. Microsoft published Patch Tuesday on September 13 to address this and additional 62 Windows security flaws.
An attacker must already have access to the target system and the capacity to execute code there. In situations where the attacker does not already have such capability on the target machine, this approach does not provide remote code execution, according to Microsoft’s advice. Microsoft claims that this flaw has already been used in the wild.
The base block for the base log file (BLF) in CLFS.sys’s Base Block does not perform a tight bounds check for the SignaturesOffset field, which is the root cause of the vulnerability. A bogus Client Context in the base log file and a specifically constructed client context array can both use CLFS to replace the SignaturesOffset field with an incorrect value. When a Symbol is allocated, this results in a validation bypass for the cbSymbolZone field. Invalid cbSymbolZone fields can therefore result in an out-of-bound writing at any offset.
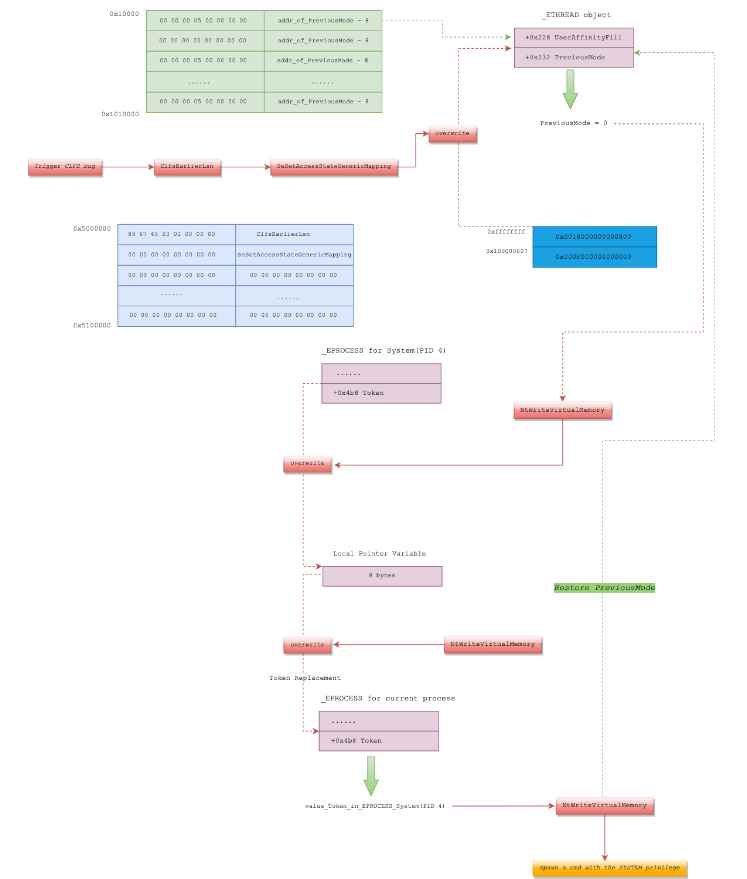
A proof-of-concept (PoC) code to exploit the CVE-2022-37969 security flaw has been made available by Zscaler ThreatLabz. “The attack for Windows 11 initially exploits the CLFS flaw to carry out an arbitrary write for the PipeAttribute object. To accomplish token substitution, the attack then initiates a second trigger of the CLFS vulnerability. The site stated that “for Windows 10, the attack only has to exploit the CLFS vulnerability once and uses the PreviousMode approach to create an arbitrary write primitive before invoking the NtWriteVirtualMemory function to finish the token substitution.
It’s important to note that CVE-2022-37969 might allow for a full system takeover if it is successfully exploited.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











