Jira Align is a software-as-a-service (SaaS) platform that enables businesses to grow their cloud installations of the wildly popular bug tracking and project management tool Atlassian Jira.
A high severity (CVSS 8.8) authorization controls issue was discovered by a Bishop Fox security researcher. It enables users with the ‘people’ permission to raise their privilege, or that of any other user, to “super admin” using the MasterUserEdit API. According to Jake Shafer, a senior security consultant, super administrators have the ability to change security settings, reset user accounts, and reconfigure Jira connections, among other things.
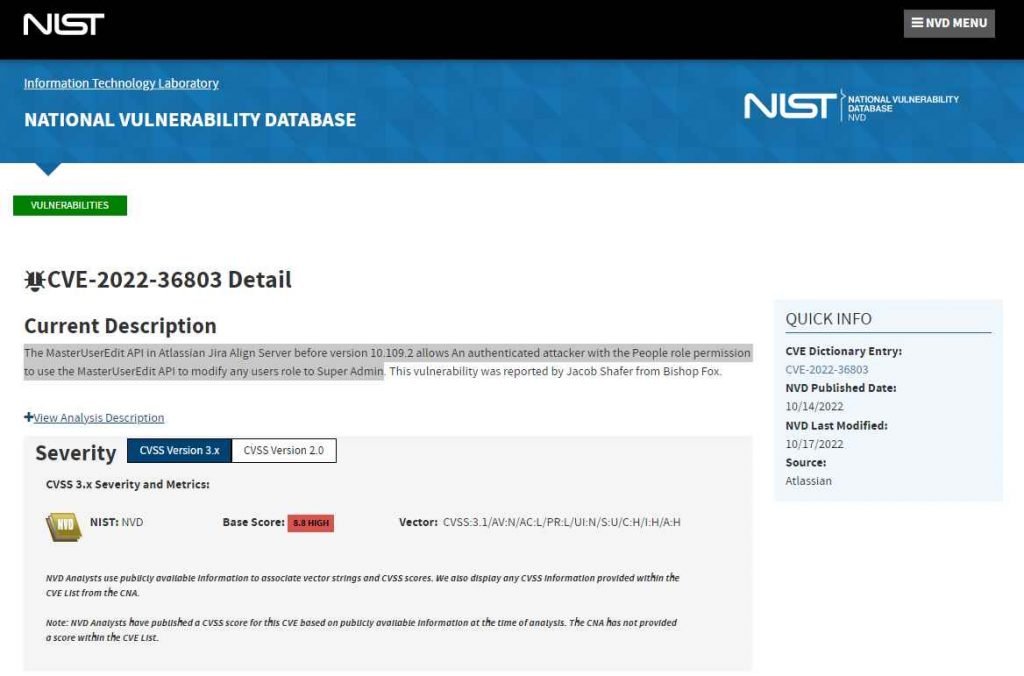
Additionally, attackers had access to “whatever the SaaS client had in their Jira deployment or simply take the entire thing down.”
The setting of an instance determines the function of the “people” permissions. “ This permission was introduced to the “program manager” position in the testing sandbox environment, although it may also be used by any role having the “people” permission. The API call may be made using a POST request including their session cookies, or it could be done by “intercepting the role change request straight to the API and altering the cmbRoleID parameter to 9”.
The Jira Align ManageJiraConnectors API, which controls external connections, houses the SSRF.
TxtAPIURL, a user-supplied URL value, refers to the appropriate API address. Jira Align added /rest/api/2/ automatically on the server side, but the additional ‘#’ addition “would let an attacker to provide any URL”
In the “worst-case scenario,” two Jira Align security flaws might be coupled by hostile users with minimal privileges to attack Atlassian’s cloud infrastructure.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











