RedEye is an open-source analytical tool for administrators to view and report command and control (C2) activities, according to the U.S. Cybersecurity and Infrastructure Security (CISA) organization. RedEye is a cooperative effort between CISA and the DOE’s Pacific Northwest National Laboratory that can read attack framework logs and show complicated data in a more palatable manner.
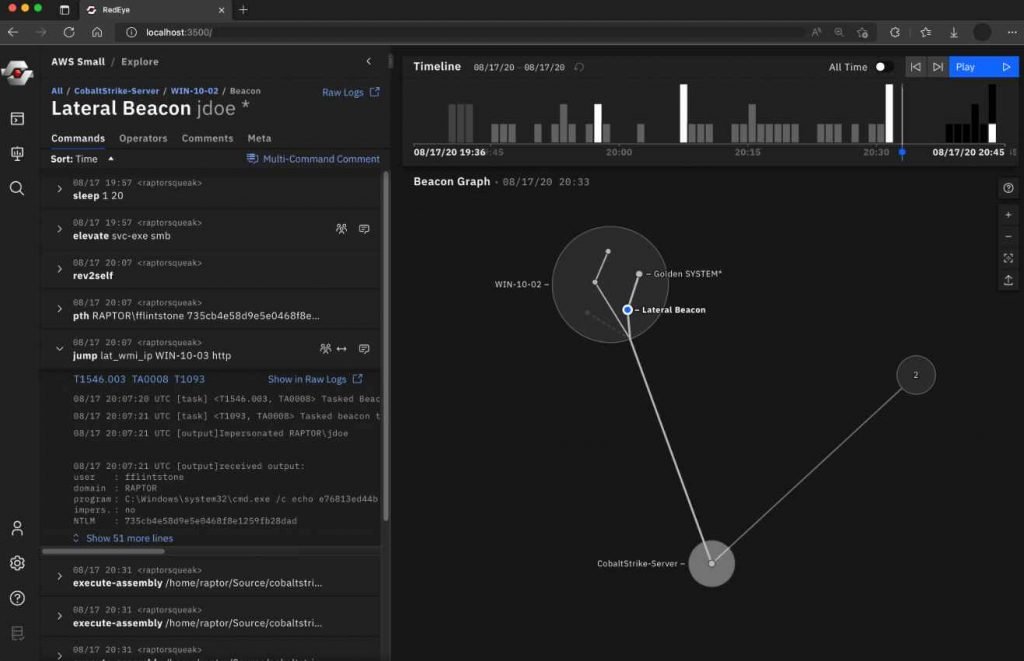
RedEye is a tool that both red and blue teams may use to quickly assess data and make useful decisions.
It enables efficient decision-making in response to a Red Team evaluation, enables an administrator to evaluate mitigation methods, and assesses and displays complicated data. The application analyzes logs, including those from Cobalt Strike, and provides the information in a way that is simple to understand. Then, users may tag and comment on the actions that are shown in the tool. The RedEye’s presentation mode may be used by operators to show stakeholders their results and procedure.
RedEye can effectively help an operator:
Instead of manually reading through hundreds of lines of log information, replay and show the Red Team’s assessment actions as they happened.
To facilitate efficient decision-making, present and analyze complicated evaluation data.
Improve your understanding of the attack strategy used and the compromised hosts during a Red Team assessment or penetration test.
Downloading the most recent RedEye binaries for your operating system from GitHub’s Downloads section is the quickest method to get started.
Cobalt Strike log uploads are presently supported by RedEye, which also provides Red Team and Blue Team modes.
You may submit campaign records, investigate, and make presentations in the Red Team mode. Run RedEye using the SERVER BLUE TEAM=false environment setting or the —redTeam parameter to activate this mode.
Reviewing a read-only campaign exported by a Red Team is possible in the Blue Team mode. By default, this mode is in use. The same RedEye program binary may be used to launch both Red Team and Blue Team modes.
It has been verified to function on
Linux
Ubuntu 18 and newer
Kali Linux 2020.1 and newer
Others may be supported but are untested
macOS
El Capitan and newer
Windows
Windows 7 and newer
ARM support is experimental
RedEye may also create presentations that can be shared with clients and partners using the feedback from analysts and the campaign’s strategies.
Clients may export all campaign-related data for evaluation, along with analyst feedback.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











