A security investigator has discovered three new code execution flaws in the Linux kernel that might be exploited by a local or external adversary to take control of the vulnerable computers and run arbitrary code.
The roccat_report_event function in drivers/hid/hid-roccat.c has a use-after-free vulnerability identified as CVE-2022-41850 (CVSS score: 8.4). A local attacker might exploit this flaw to run malicious script on the system by submitting a report while copying a report->value . Patch has be released to addresses the Linux Kernel 5.19.12 vulnerability CVE-2022-41850.
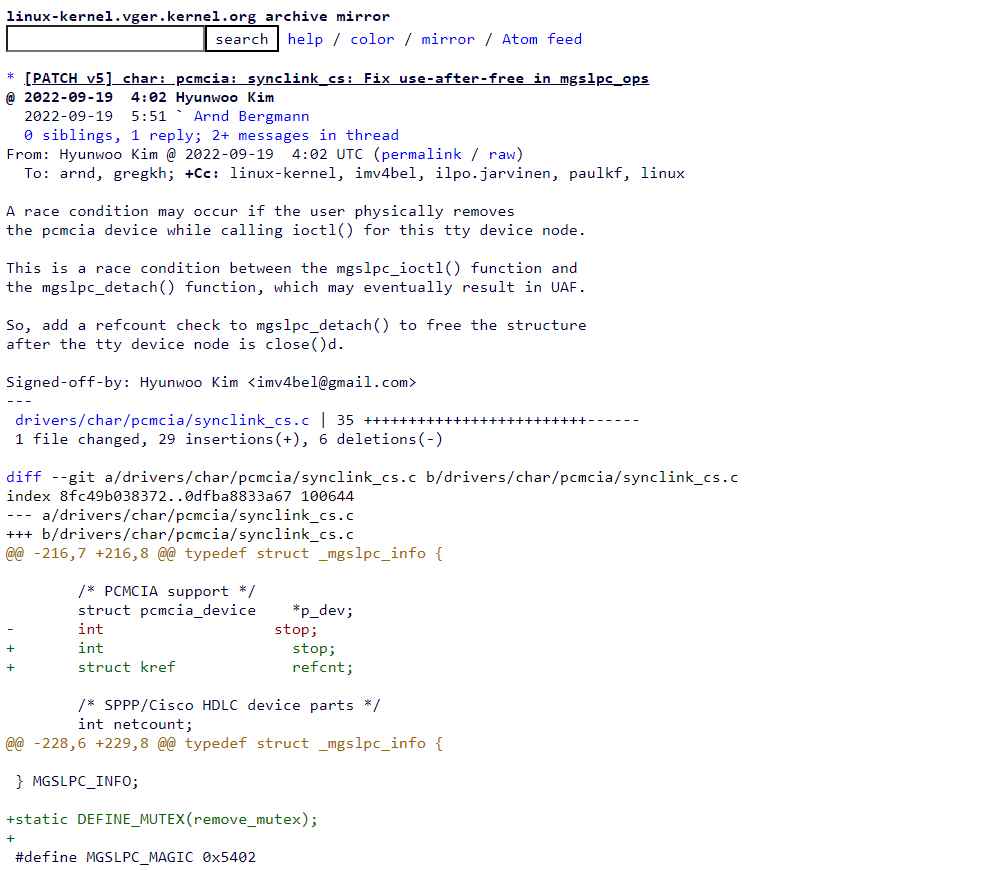
The second flaw tracked as CVE-2022-41848 (CVSS score: 6.8), is also a use-after-free flaw due to a race condition between mgslpc_ioctl and mgslpc_detach in drivers/char/pcmcia/synclink_cs.c. By removing a PCMCIA device while calling ioctl, an attacker could exploit this vulnerability to execute arbitrary code on the system. The bug affects Linux Kernel 5.19.12 and was fixed via this patch.
Due to a compatibility issues between mgslpc ioctl and mgslpc detach in drivers/char/pcmcia/synclink cs.c, the second vulnerability, tagged as CVE-2022-41848 (CVSS score: 6.8), is likewise a use-after-free vulnerability. An adversary might use this flaw to run malicious script on the computer by deleting a PCMCIA device while executing ioctl. There is a patch that corrects this flaw that was present in the Linux Kernel 5.19.12.
The third vulnerability is identified as CVE-2022-41849. Due to a race situation between ufx ops open and ufx usb disconnect in drivers/video/fbdev/smscufx.c, (CVSS score: 6.8) causes a use-after-free vulnerability. A physical adversary might use this flaw to execute malicious code on the machine by removing a USB device while running open(). There is patch that rectifies this vulnerability that was present in the Linux Kernel 5.19.12.
Administrators are urged to upgrade their Linux machines as soon as their different distros send them the necessary updates. Additionally, it is advised that they only permit trustworthy people to access local systems and always keep an eye on any compromised ones.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











