Microsoft’s threat intelligence team claims that the DEV-0270 group (also known as Nemesis Kitten or Phosphorus) has been abusing Windows’ BitLocker feature in its attacks and using it to encrypt data on its victims’ drives with the subsequent request for ransom to them.
Microsoft analysts comment that attackers are increasingly taking advantage of LOLBINs (Living Off the Land Binaries), a technique that is based on taking advantage of the system’s own binaries to cause significant damage in an attack, with a relatively low detection rate in these attacks.
It uses BitLocker, a data protection feature that provides full-volume encryption on devices running Windows 10, Windows 11, or Windows Server 2016 and higher. According to the investigation, the group uses DiskCryptor, an open source disk encryption system for Windows that enables full encryption of a device’s hard drive.
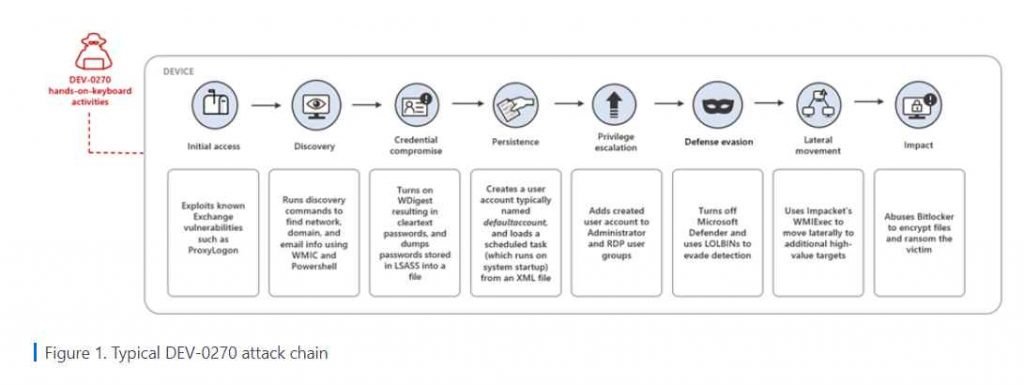
From the access of the attackers to the computers to the appearance of the ransom note of the blocked computers, approximately two days passed and the notes demanded the payment of the amount of 8,000 dollars in exchange for the keys to unlock the information.
For domain controller discovery, attackers make use of the following PowerShell and WMI commands:
“powershell.exe” /c Get-WMIObject Win32_NTDomain | findstr DomainController
“findstr.exe” DomainController
Microsoft says this group of attackers is a branch of the Iran-backed “Phosphorus” group (also known as Charmin Kitten and APT35) known for targeting high-profile victims linked to governments, NGOs and advocacy organizations around the world.
The DEV-0270 cluster is being operated by a well-known Iranian company under two aliases: Secnerd (secnerd[.]ir) and Lifeweb (lifeweb[.]it).
These organizations are also linked to Najee Technology Hooshmand (ناجی تکنولوژی هوشمند), located in Karaj, Iran, according to investigations.
The group is often opportunistic in its targeting: they scan the Internet to find servers and devices, making organizations with vulnerable and detectable servers and devices susceptible to these attacks.
Since many of the DEV-0270 attacks have exploited known vulnerabilities in Exchange (ProxyLogon) or Fortinet (CVE-2018-13379), companies are advised to patch their servers and equipment to block exploit attempts and subsequent hacking attacks. ransomware.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.










