The Cyber Security Agency of the United States (CISA) added to its catalog of vulnerabilities that are being actively exploited a recently discovered flaw in UnRAR.
About the UnRAR vulnerability
As CVE-2022-30333, this is a path traversal vulnerability in the version of RAR for Linux and UNIX systems. If successfully exploited, a malicious actor is capable of downloading arbitrary files to the victim’s system just by decompressing a RAR file.
The vulnerability, which affects any version of Linux and UNIX that uses UnRAR, received a score of 7.5 on the CVSS severity scale and was disclosed in June.
SonarSOurce researchers were the ones who discovered the flaw and published a report explaining how it could be used to compromise a Zimbra webmail service server and gain access to the mail server.
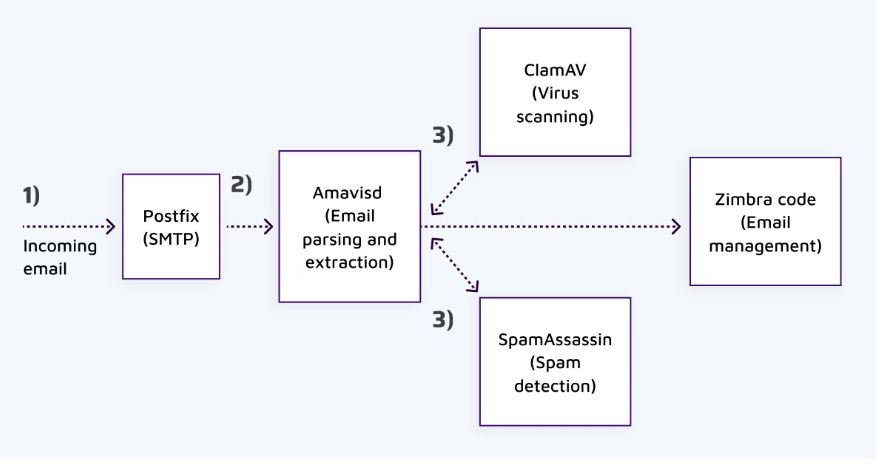
In the specific case of Zimbra, because the service uses UnRAR to automatically extract attachments and scan them for malware or spam, an attacker could send an email with a RAR file attached and compromise the victim without the need for interaction with Zimbra. the attachment. For its part, Rarlab released version 6.12 in May, which contains the patch that repairs CVE-2022-30333 in all versions of RAR for Linux and UNIX.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











