Details and screenshots of a version of the Pegasus spyware software designed for Israeli police were leaked. This spyware was referred to by police by a different name: Seifan.
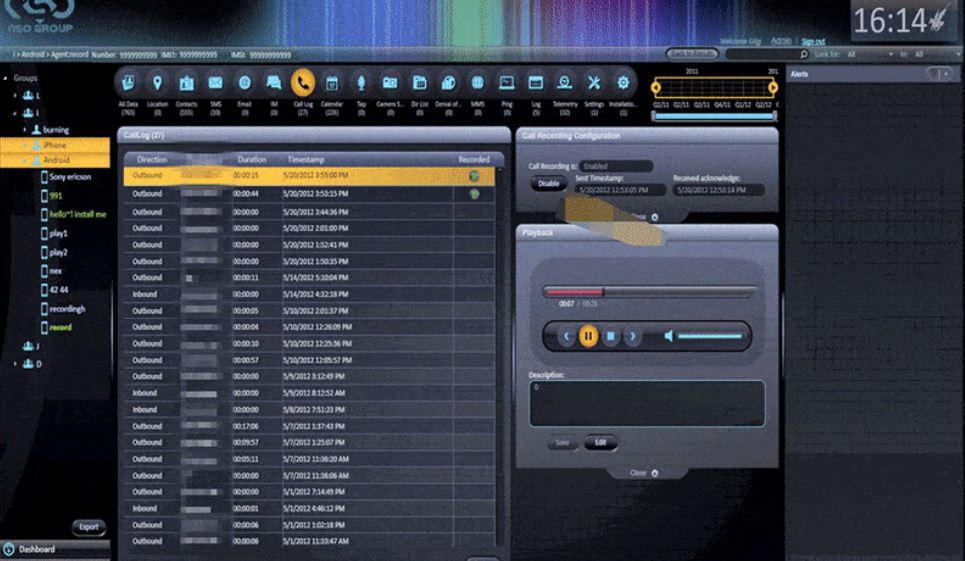
The spyware’s software included various capabilities ranging from listening to any phone call on a victim phone, reading text messages, to remotely listen via microphone and start the camera without the victim’s knowledge. The spyware also allowed get location, contacts list, SMS, WhatsApp messages, emails, instant messaging, outgoing and incoming calls, calendar, remote recordings and remote camera use
Earlier, the former Israeli police commissioner said that “The Police don’t have Pegasus”. In response, an investigative committee led by Courts for checking whether police used the spyware to hack into people’s phones without permission found out that the police had Seifan.
Court discovered that even though there had been no eavesdropping without court orders, the spyware was deployed in 2016. The phone data collected was more than what was legally allowed by court orders and the organization still holds the information in the databases of its cyber department.
According to Israel newspaper Haaretz, the leaked presentation highlighted the screenshots of the spyware, which included covertly monitoring “protected messages” as well as voice and text chats on advanced cell phones. Police had complete control of the victim’s cell phone after infecting it.
The spyware and capabilities of the police-implemented system, were ever presented to the cabinet ministers. Screenshots from the prototype of the system the police intended to use were included in the presentation and show the NSO logo and the product name Pegasus itself.
Another capability of Seifan is “volume listening” and is considered much more intrusive. It means listing calls in real time via activating a phone microphone remotely and listening to real time calls vai it. Rather than hacking into a cell phone sim card. This type of wiretapping requires an order from a district court president or their deputy.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











