In this tutorial, the specialists of the Cyber Security 360 course of the International Institute of Cyber Security (IICS) will show us how to use ZANTI, a pentesting tool that allows attacks against a certain network, in addition to operating routers, auditing passwords, creating and running HTTP servers, scanning devices for open ports, and more.
Using this tool, a hacker can crack passwords on Android and also change HTTP requests and responses, triggering wireless network compromise scenarios via an Android phone.
As usual, we remind you that this tutorial was prepared for informational purposes only and does not represent a call to action, so IICS is not responsible for the misuse that may be given to the information contained herein.
Before we continue, let’s take a look at all the actions we can take using ZANTI:
- Hack HTTP sessions using Man-in-The-Middle (MiTM) attacks
- Download capture
- Modification of HTTP requests and responses through MiTM attacks
- Router hijacking
- Password interception
- Scanning devices for Shellshock and SSL Poodle vulnerabilities
- Detailed nmap scanning
Installing ZANTI
Follow the steps listed by the experts in the Cyber Security 360 course to install ZANTI correctly:
- Go to the official website from https://www.zimperium.com/zanti-mobile-penetration-testing
- Enter an email address
- The download link will be available shortly
- Download the APK
- Select the option Install from unknown sources if necessary
- Install the APK
- Open the app, grant the required permissions and connect to a WiFi network
Let’s take a closer look at the features of the tool.
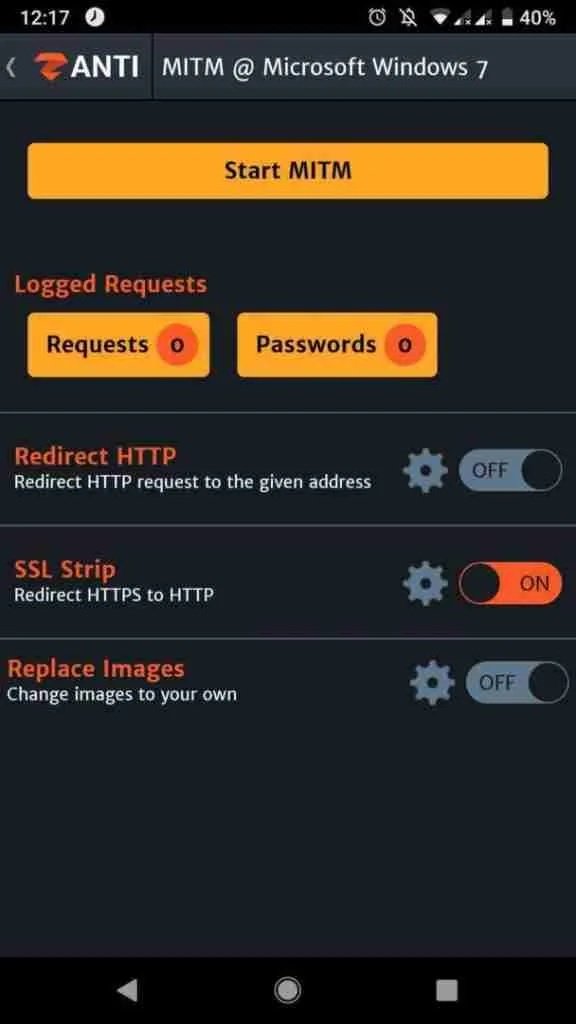
Hack HTTP sessions with MiTM
You can redirect all HTTP traffic to a specific server or site by default, as soon as the “HTTP Redirect” feature is enabled. You can also redirect it to a specific website by clicking on the settings icon, and then you will find a place to enter the URL.
Download capture
This feature allows you to connect to the host’s downloads folder and get a copy of all its contents. For example, if you select “.pdf” from the menu and click “Upload File”, all PDF files will be downloaded to your phone.
This tactic can be especially useful when it comes to social engineering, mention the experts of the Cyber Security 360 course.
Modification of HTTP requests and responses through MiTM attacks
Using zPacketEditor you can change http requests and responses on your network. It is an interactive mode that allows you to edit and submit each request and response. However, this is complicated and may not work on all phones.
Hijack routers
Router pwn is a web application for exploiting router vulnerabilities. This is a set of local and remote exploits ready to run.
For use, click on “Routerpwn.com”, then select your router provider; you can check for other vulnerabilities, so if you wish you can find out more about these flaws.
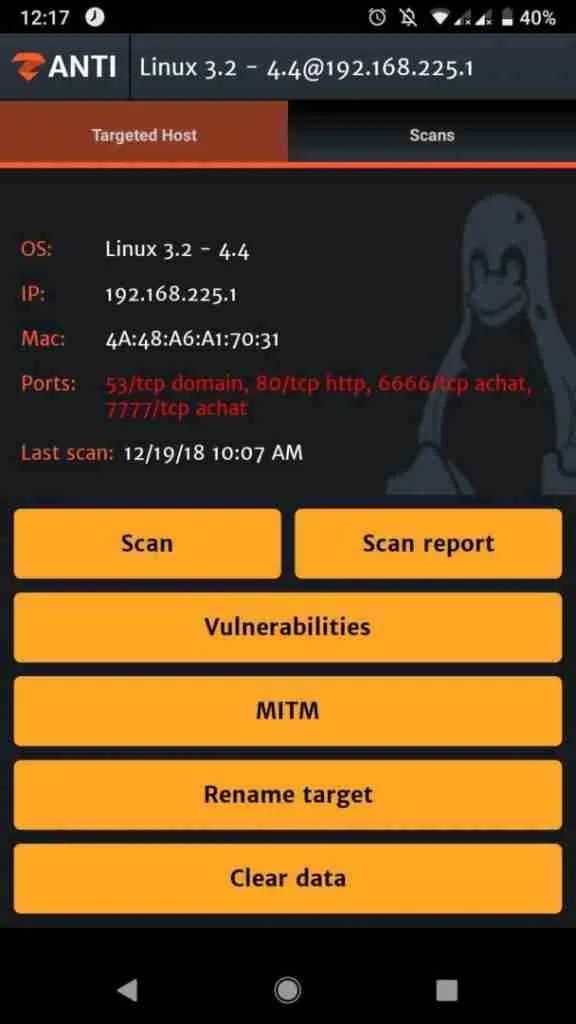
Password interception
This is the main feature of ZANTI and allows the capture of passwords in networks, mention the experts of the Cyber Security 360 course. For this, select the target device and click the MITM button; you can find the results in the saved passwords section.
Scanning devices for Shellshock and SSL Poodle vulnerabilities
First, select the device; click on “Shellshock/SSL Poodle” and you can scan the target device. Wait for a while and then get the result. If the device is vulnerable, you can use it.
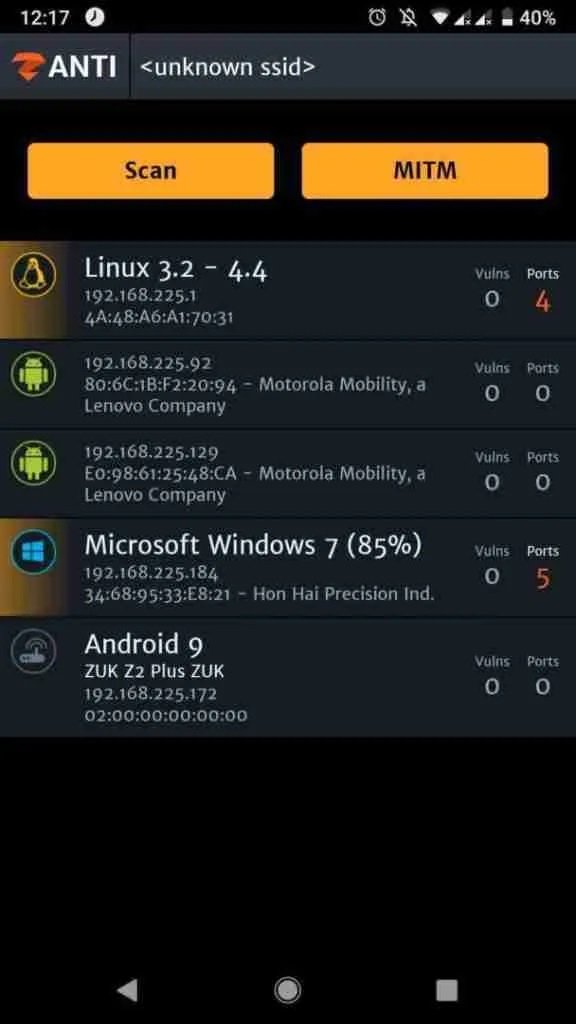
nmap scanning
This feature gives you all the important sensitive information about the target and network, open ports, IP addresses, operating systems, etc. It can be very useful to find exploits and hacks related to our goal, mention the experts of the Cyber Security 360 course.
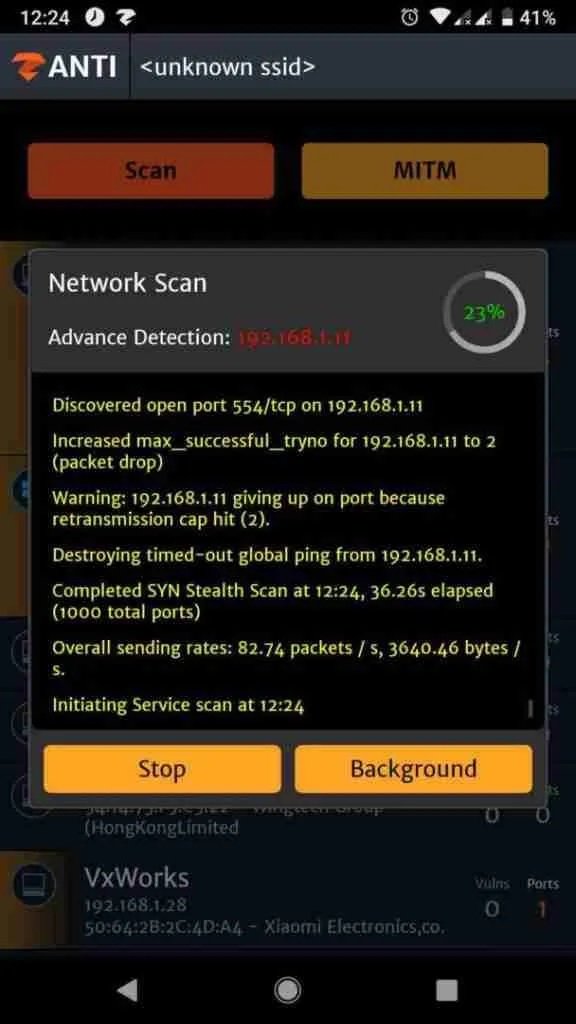
These have been some basic concepts for the use of the ZANTI tool, which can prove very useful for hacking Android devices over wireless networks.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and to learn more about the Cyber Security 360 course.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










