Common Weakness Enumeration (CWE) is Managed by MITRE and it a released top 25 Most Dangerous Software vulnerabilities list. This list shows the currently most common and impactful vulnerabilities. Often easy to find and exploit, these can be exploited that can allow threat actors to completely take over a system, steal data, or bring down applications.
The 2022 CWE Top 25 was obtained by analyzing public vulnerability data from the NVD. For the 2022 list, data was used from the Known Exploited Vulnerabilities (KEV) Catalog, established in conformity with “Binding Operational Directive 22-01- Reducing the Significant Risk of Known Exploited Vulnerabilities” by CISA. The KEV is an authoritative source of vulnerabilities that are known to have been exploited by threat actors.
After the data collection, remapping and analysis process, a scoring formula was used to calculate a rank order of vulnerabilities that combines the frequency that a CWE is the root cause with the severity of its exploitation calculated by CVSS.
Many cyber security professionals will find the CWE Top 25 a practical and convenient resource to help mitigate vulnerabilities. Professionals who perform mitigation and risk decision-making using the 2022 CWE Top 25 List should consider including these additional vulnerabilities in their analyses because all vulnerabilities can be exploited under the right conditions.
Below is a list of the vulnerabilities, including the overall score of each. The KEV Count (CVEs) shows the number of CVE-2020/CVE-2021 records from the CISA KEV list that were mapped to the given vulnerability.
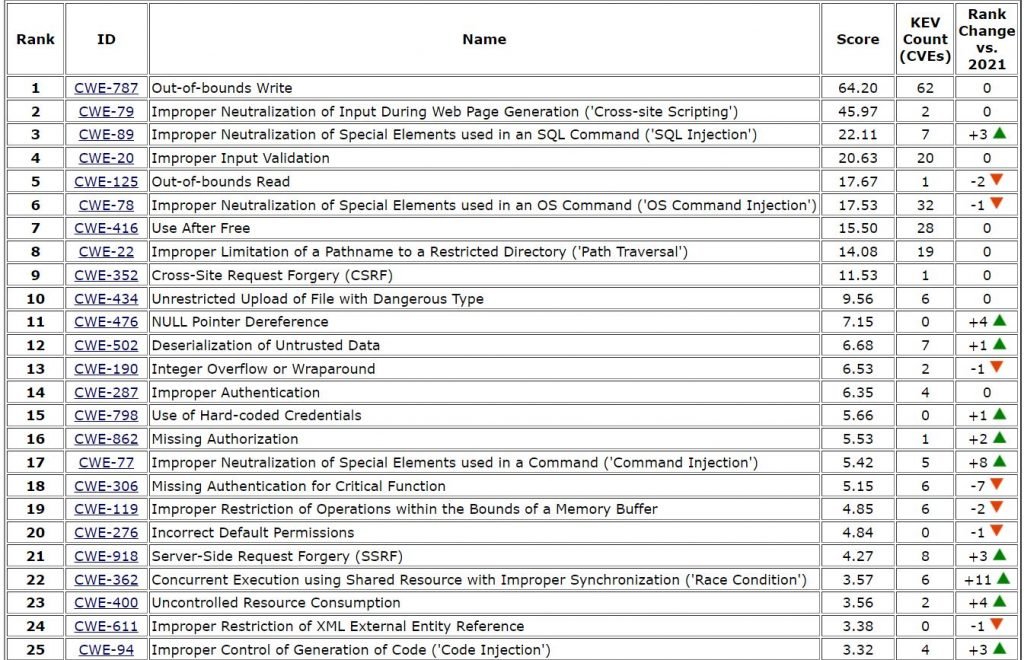
There are several notable shifts in ranked positions of vulnerabilities types from last year’s list, including several vulnerabilities dropping away or making their first appearance in a Top 25.
The biggest movers up the list are:
- CWE-362 (Concurrent Execution using Shared Resource with Improper Synchronization (‘Race Condition’)): from #33 to #22
- CWE-94 (Improper Control of Generation of Code (‘Code Injection’)): from #28 to #25
- CWE-400 (Uncontrolled Resource Consumption): from #27 to #23
- CWE-77 (Improper Neutralization of Special Elements used in a Command (‘Command Injection’)): from #25 to #17
- CWE-476 (NULL Pointer Dereference): from #15 to #11
The biggest downward movers are:
- CWE-306 (Missing Authentication for Critical Function): from #11 to #18
- CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor): from #20 to #33
- CWE-522 (Insufficiently Protected Credentials): from #21 to #38
- CWE-732 (Incorrect Permission Assignment for Critical Resource): from #22 to #30
New entries in the Top 25 are:
- CWE-362 (‘Race Condition’): from #33 to #22
- CWE-94 (Code Injection): from #28 to #25
- CWE-400 (Uncontrolled Resource Consumption): from #27 to #23
Entries that fell off the Top 25 are:
- CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor): from #20 to #33
- CWE-522 (Insufficiently Protected Credentials): from #21 to #38
- CWE-732 (Incorrect Permission Assignment for Critical Resource): from #22 to #30

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











