Today, the specialists of the Cyber Security 360 course of the International Institute of Cyber Security (IICS) will show us in detail the use of Fuzz Faster U Fool (ffuf), a free and easy-to-use fuzzing tool, using the command line method for configuration on web servers.
Created by Twitter user @joohoi, cybersecurity professionals around the world have praised ffuf for its advanced capabilities, versatility, and ease of use, making it one of the top choices in fuzzing.
Before keep going, as usual, we remind you that this article was prepared for informational purposes only and does not represent a call to action; IICS is not responsible for the misuse that may occur to the information contained herein.
INSTALLATION
According to the experts of the Cyber Security 360 course, ffuf runs on a Linux terminal or Windows command prompt. Upgrading from the source code is no more difficult than compiling, except for the inclusion of “-u”.
go get -u github.com/ffuf/ffuf
For this example Kali Linux was used, so you will find ffuf in the apt repositories, which will allow you to install it by running a simple command.
apt install ffuf
After installing this program, you can use the “-h” option to invoke the help menu.
ffuf –h
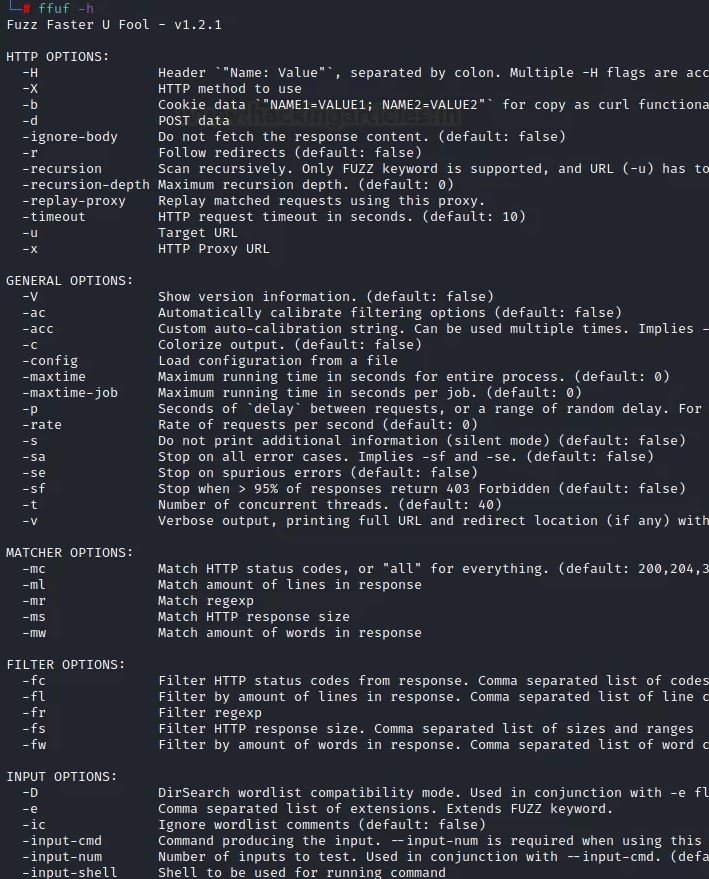
ENTRY OPTIONS
These are parameters that help us provide the data needed for a web search of a URL using word lists.
Normal attack
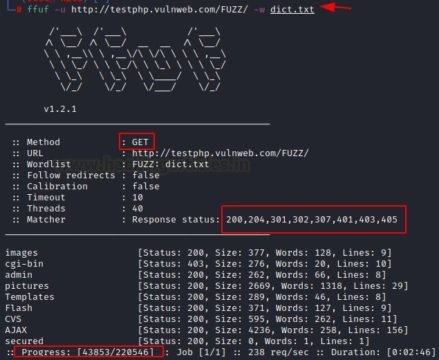
For a normal attack, use the parameters “-u” for the target URL and “-w” to load the word list.
ffuf -u http://testphp.vulnweb.com/FUZZ/ -w dict.txt
After you run the command, you will need to focus on the results.
- First, it’s worth noting that by default it works on HTTP using the GET method
- You can also view the status of the response code (200, 204, 301, 302, 307, 401, 403, and 405). You can track the progress of the attack being performed
Using multiple word lists
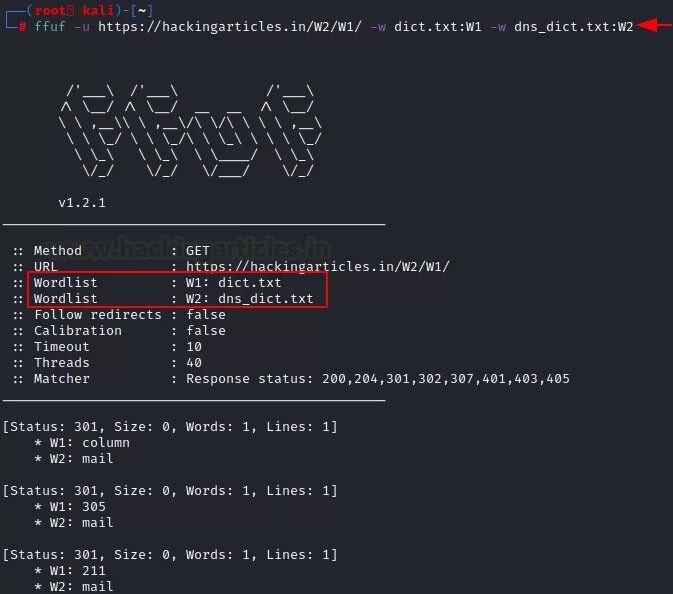
The experts of the Cyber Security 360 course mention that a single list of words is not always enough to get the desired results. In these cases, you can apply multiple word lists at the same time, one of the most attractive functions of ffuf. In this example, we have granted the program access to two dictionaries (txt:W1 and txt:W2), which the tool will run at the same time:
ffuf -u https://ignitetechnologies.in/W2/W1/ -w dict.txt:W1 -w dns_dict.txt:W2
Ignore a comment in a word list
Usually, the default word list has some comments that can affect the accuracy of the results. In this case, we can use the “-ic” parameter to delete the comments. Also, to remove any banners in the tools used, use the “-s” parameter:
ffuf -u http://testphp.vulnweb.com/FUZZ/ -w dict.txt
Here we can notice that some comments are shown in the results if the above command is executed. After using the “-s” and “-ic” parameters, all comments and banners will be removed.
ffuf -u http://testphp.vulnweb.com/FUZZ/ -w dict.txt -ic –s
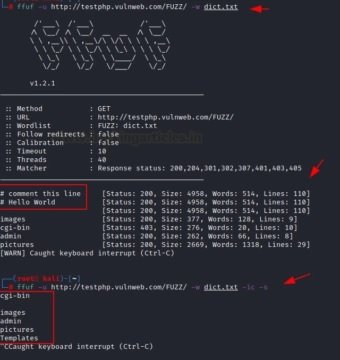
Extensions
It is also possible to search for a file with a specific extension on a web server using the “-e” option. All you need to do is specify the extension and name of the file along with the parameter in the appropriate command format:
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -e .php
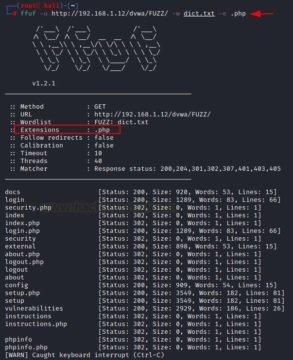
Different queries and modes
Burp Suite is a professional platform for monitoring the security of web applications. The “cluster bomb” function allows using multiple payloads, mention the experts of the Cyber Security 360 course. There is a separate payload package for each given location; the attack goes through each payload packet one by one, checking all possible options.
There are several parameters of this tool that make it easy to use the script. For example, the “-request” parameter allows you to use the request in an attack, while “-request-proto” allows you to define the parameter itself, and “-mode” helps you choose the attack mode.
First, random credentials are used on the target URL page and the proxy server is configured to capture the request in interception mode in Burp Suite.
Now, on the Intercept tab, you need to change the credentials provided by adding HFUZZ and WFUZZ. HFUZZ is added before “uname” and WFUZZ before “pass”. Then, you need to copy and paste this query into the text and name according to the purposes of the project. In this case, the file was named as brute.txt.
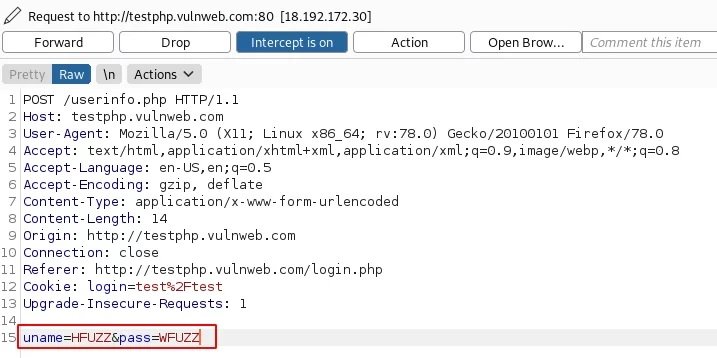
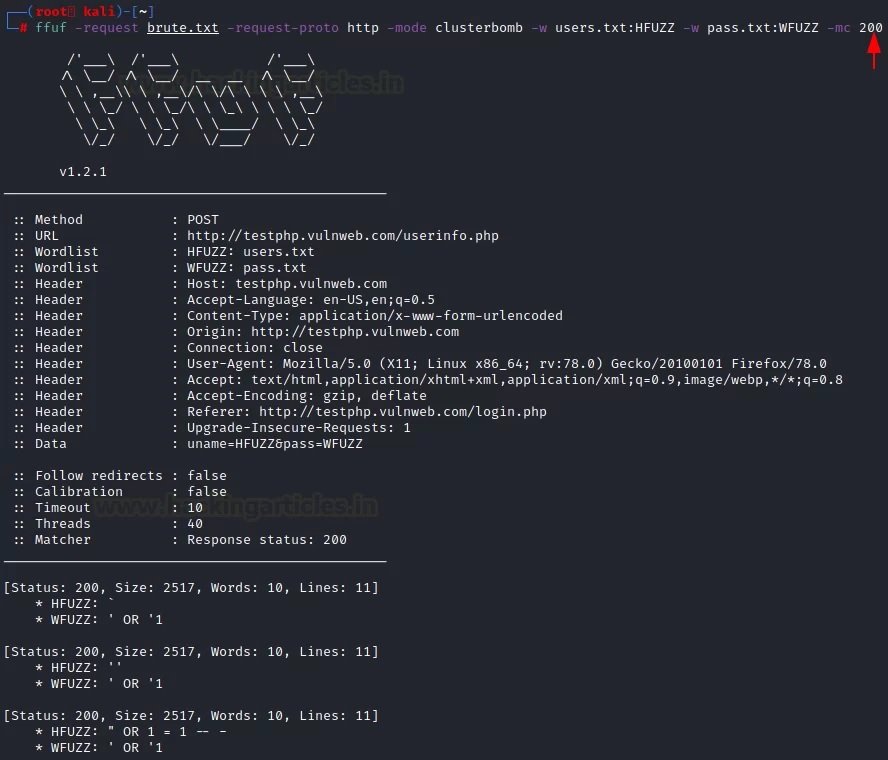
Later we will move to the main attack mode, where the “-request” parameter contains a “-request-proto” text file that will help you create a prototype of http, and “-mode” will be responsible for the “cluster bomb” attack. The lists of words in question (users.txt and pass.txt) consist of SQL injections. By entering the following command, an attack will be launched:
ffuf -request brute.txt -request-proto http -mode clusterbomb -w users.txt:HFUZZ -w pass.txt:WFUZZ -mc 200
As you can see from the results of the attack, SQL injections have been successfully found to be effective for this specific purpose.
MAPPING OPTIONS
If we want the ffuf to show only the data that is important for web fuzzing, we must pay attention to these parameters. For example, it can be HTTP code, strings, words, size and regular expressions, mention the experts of the Cyber Security 360 course.
HTTP Code
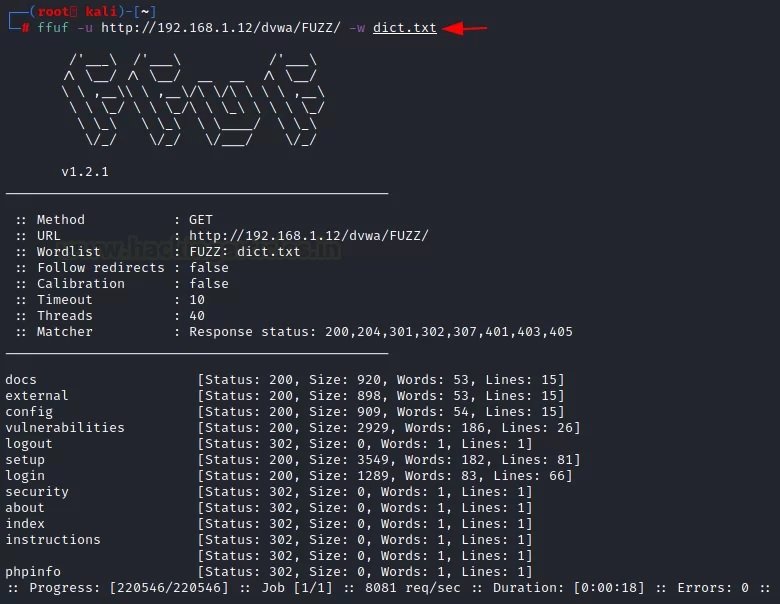
To understand this configuration, you should consider a simple attack on which you will be able to see which HTTP codes appear in the results.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt
It is clear that the codes 302 HTTP and 200 HTTP were received.
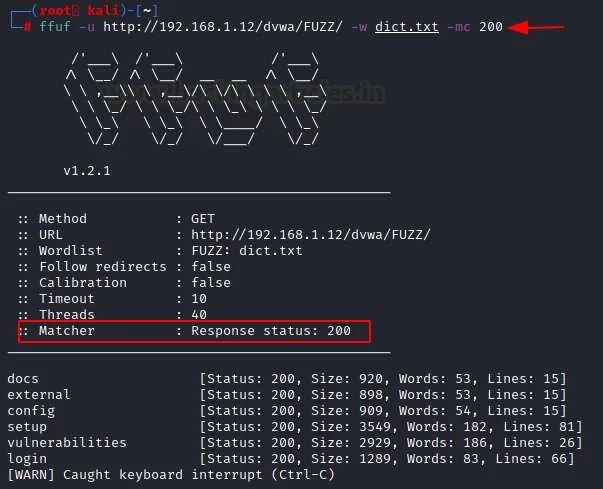
If you want to see specific attacks, such as HTTP code 200, you must use the “-mc” parameter along with a specific number. To verify that this parameter works, you just need to run the following command:
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -mc 200
Line
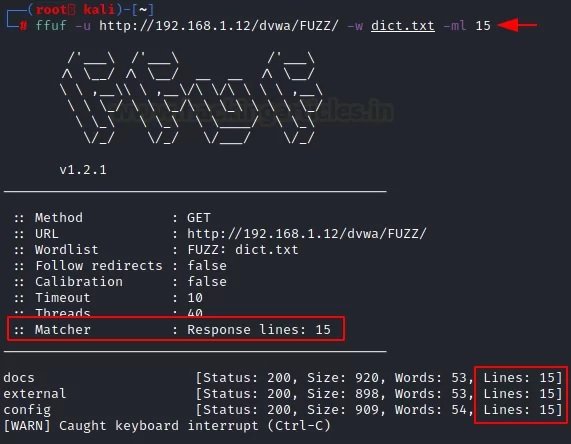
The tool returns results for specific lines in the file using the “-ml” parameter. We can use it by specifying the strings we need.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -ml 15
Words
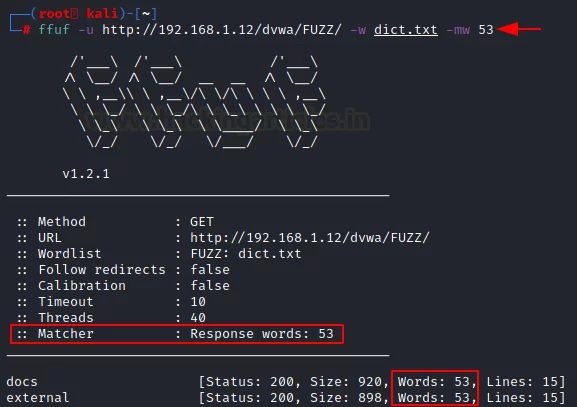
Similarly, since the above options correspond to a function, you can provide a result with a certain number of words. For this, use the “-mw” parameter along with the number of words you want to see in the results.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -mw 53
Size
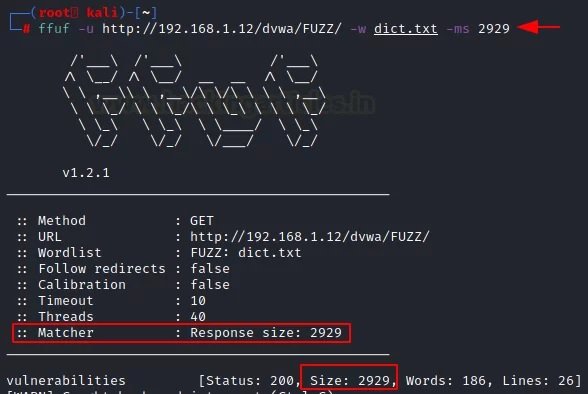
It is also possible to use the “-ms” parameter along with the specific size you want to see in the results.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -ms 2929
Regular expressions
This is the last of all the mapping options available in ffuf. LFI fuzzing will be applied by matching the string to the subsequent “root:x” pattern for this dictionary.
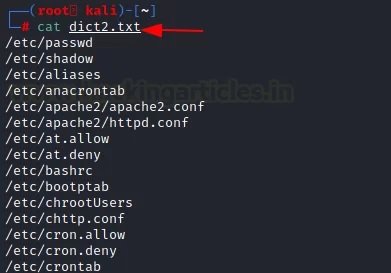
A URL is used that can provide this functionality, and with the “-mr” parameter, the corresponding string “root:x” is defined. This is what a special list of words looks like.
Using this list of words, we enter the following command to add the “-mr” parameter to the attack script:
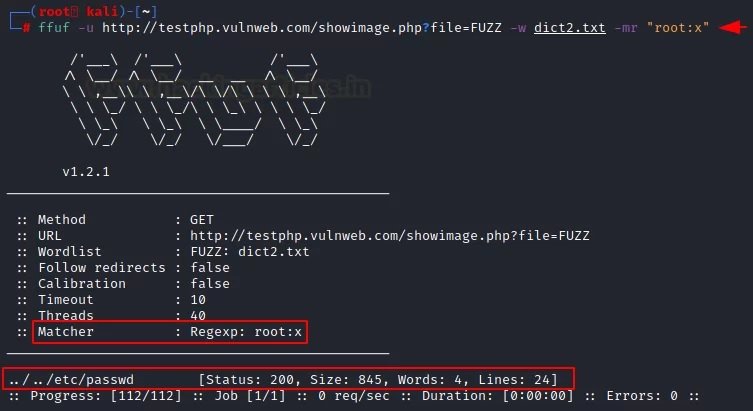
ffuf -u http://testphp.vulnweb.com/showimage.php?file=FUZZ -w dict2.txt -mr "root:x"
We received the http 200 response for /etc/passwd for this list of words.
FILTERING OPTIONS
Filtering options are the exact opposite of matching parameters. The experts of the Cyber Security 360 course recommend using these options to remove unnecessary elements during web fuzzing. It also applies to HTTP code, strings, words, size, and regular expressions.
HTTP Code
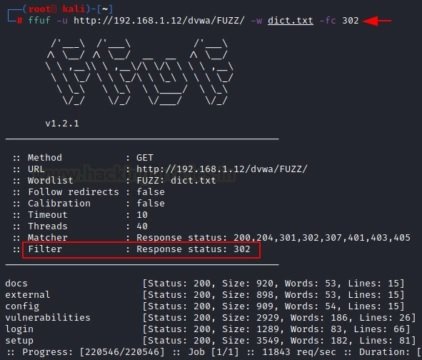
The “-fc” parameter requires a specific HTTP status code that the user wants to remove from the results.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -fc 302
Line
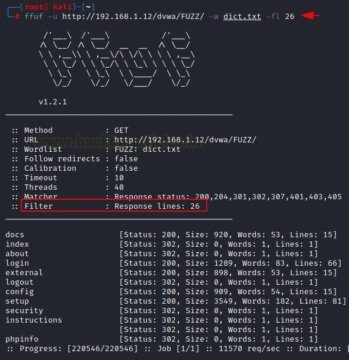
With the help of the “-fl” parameter, it is possible to remove a certain row from the result or filter it from the attack.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -fl 26
Size
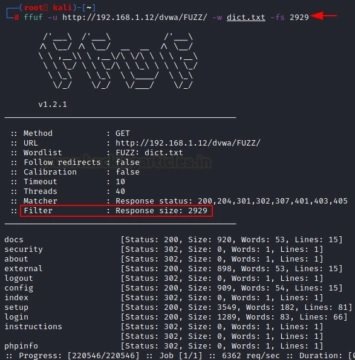
The “-fs” option allows you to filter the specified size described by the user during the attack.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -fs 2929
Words
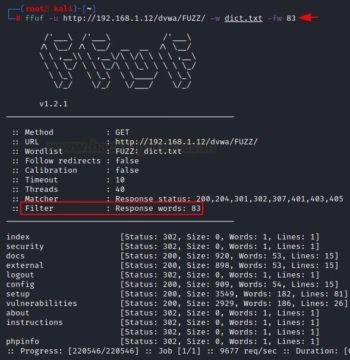
The “-fw” option allows you to filter the number of words of the results that the user wants to receive.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -fw 83
Regular expressions
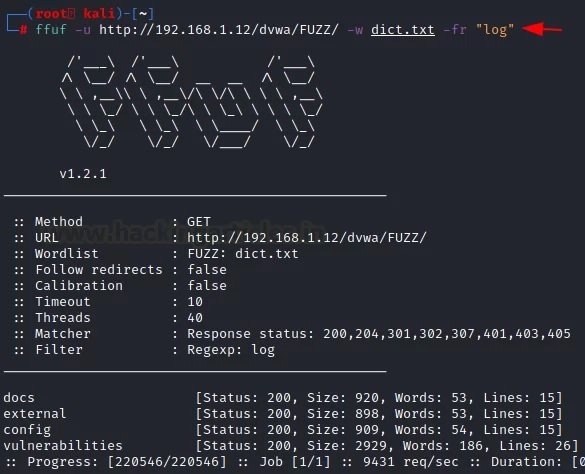
The “-fr” option allows you to delete a specific regular expression. In this case, we will try to exclude the log files from the results.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -fr "log"
GENERAL PARAMETERS
Below are the general parameters of this tool, which are completely related to the web fuzzing process.
Automatic custom calibration
Calibration is the process of providing a measuring instrument with the information it needs to understand the context in which it will be used. When collecting data, calibrating your computer ensures that the process works accurately, mention the experts of the Cyber Security 360 course.
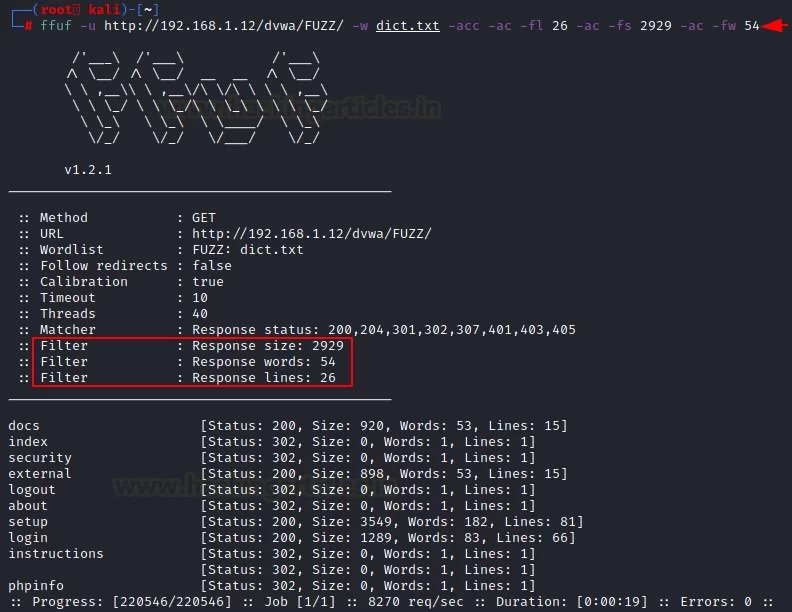
We can adjust this function according to the needs in each case using the “-acc” parameter, which cannot be used without the “-ac” parameter.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -acc -ac -fl 26 -ac -fs 2929 -ac -fw 54
Color
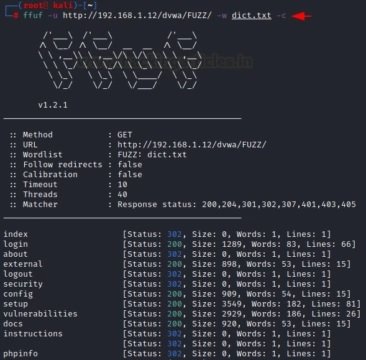
Sometimes color separation helps identify relevant details in the results. The “-c” parameter helps to divide the data into categories.ç
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt –c
Maximum task execution time
If you want to apply fuzzing for a limited period of time, you can use the “-maxtime” parameter. You must enter a command to specify the selected time interval.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -maxtime 5

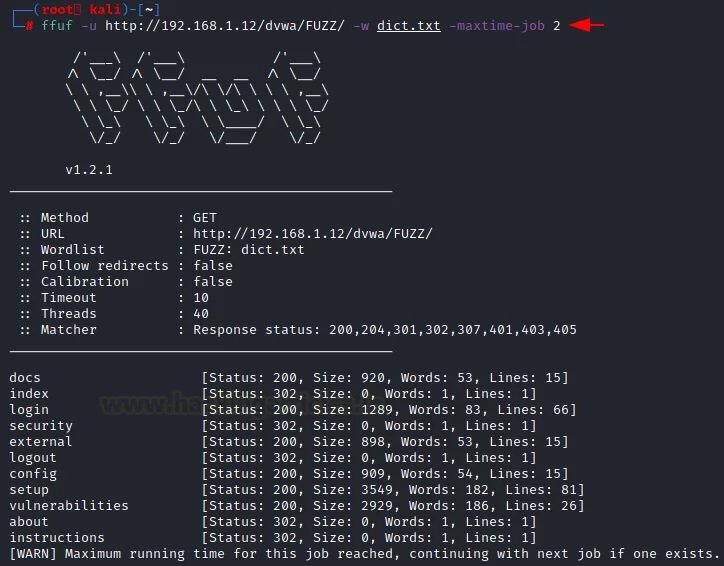
Maximum turnaround time
Using the “-max time-job” parameter, the user can set a time limit for a specific job. With this command, you can limit the time it takes to complete a task or query.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -maxtime-job 2
Delay
Using the “-p” parameter, the user will add a slight delay for each request offered by the attack. According to the experts of the Cyber Security 360 course, with this feature the consultation becomes more efficient and provides clearer results.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -p 1
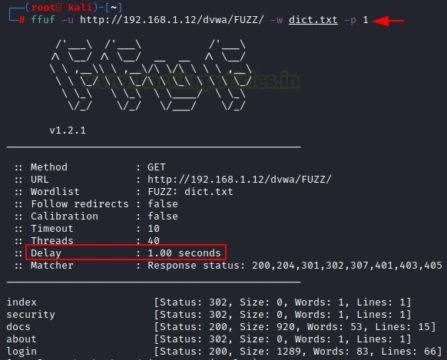
Query speed
We can select the request speed you need for each of the attacks using the “-rate” parameter. For example, we can create one request per second according to the desired attack.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -rate 500
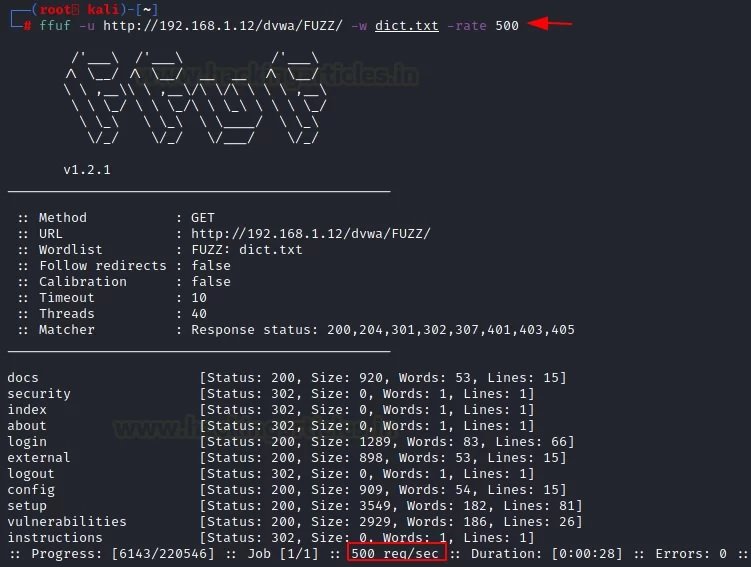
Error functions
There are three parameters that support the error function. The first parameter is “-se”, a “false error” that says whether the next request is genuine or not. The second “-sf” parameter will stop the attack when more than 95% of the requests are counted as an error. The third parameter is “-sa”, a combination of the above parameters.
In the example shown below, we will use the “-se” parameter:
Ffuf -u http://ignitetechnologies.in/W2/W1/ -w dict.txt:W1 -w dns_dict.txt:W2 –se
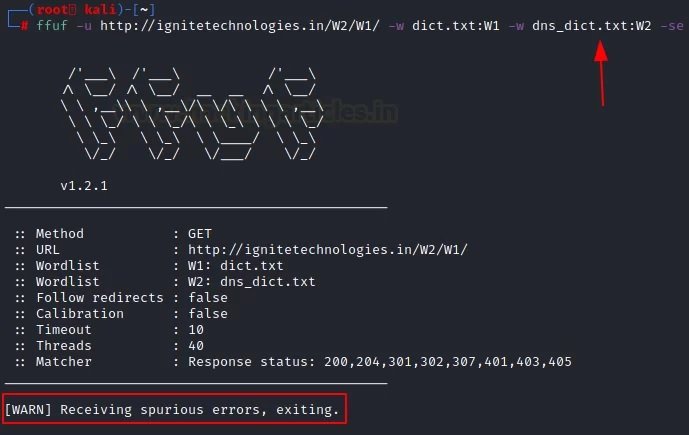
Verbose mode
Verbose Mode is a feature used in many operating systems that provide additional information about what the computer does and what drivers and applications it loads when initialized. In programming, this mode provides accurate output for debugging purposes, making it easier to debug the program itself. To access this mode, the “-v” parameter is applied.
Ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt –v
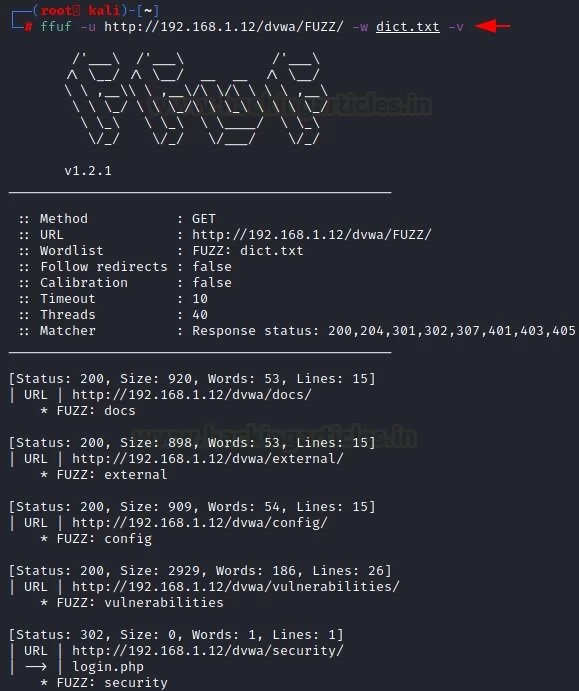
Execution threads
The “-t” parameter is used to speed up or slow down the process. By default, it is set to 40. If you want to speed up the process, you need to increase its value.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -t 1000
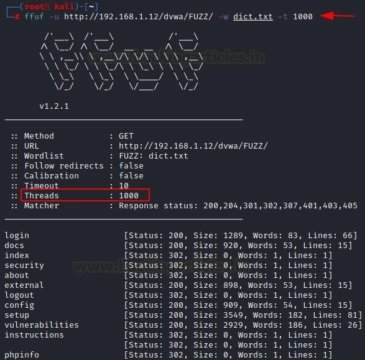
OUTPUT OPTIONS
We may save the results of attacks carried out in order to keep records, improve readability and find possible links. Enter the “-o” parameter to save the output, but you must specify its format using the “-of” parameter.
Once the attack is complete, it should be checked whether the file with the output data corresponds to this format or not, mention the experts of the Cyber Security 360 course. As you can see, the file itself refers to HTML.
Output data in CSV format
Similarly, we can create CSV files using the “-of” parameter, where csv are comma-separated values. For example:
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -o file.html -of html
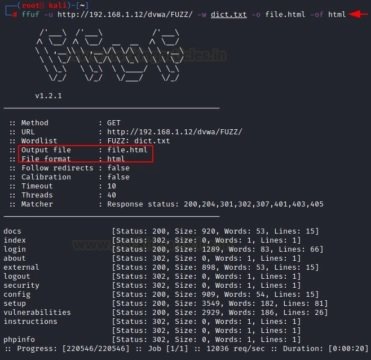
When the attack is complete, you need to check whether the file with the output data corresponds to this format or not. As you can see, the file itself belongs to the CSV.
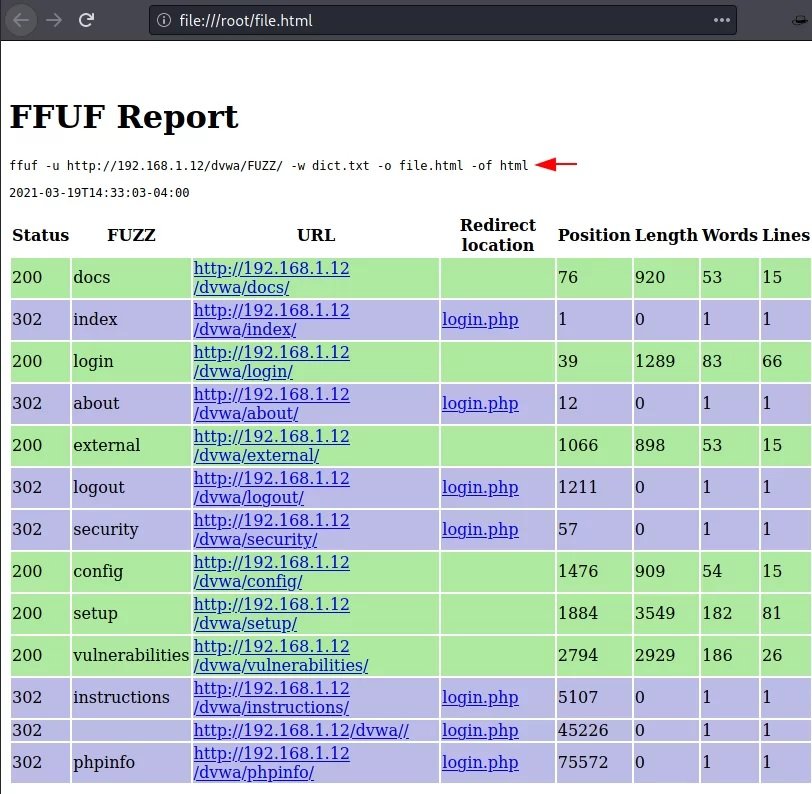
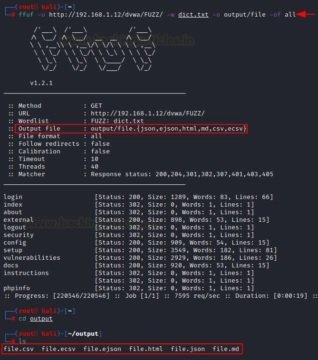
Data output in all available formats
Similarly, if you want to recover data in all formats, use the “-of all” parameter. For example, it can be json, ejson, html, md, csv, ecsv.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -o output/file -of all
Now, once the attack is complete, you need to check all the files. We can see that they were saved in various formats.
HTTP OPTIONS
Sometimes the fuzzing process requires details such as an HTTP request, cookies, and an HTTP header, mention the experts of the Cyber Security 360 course.
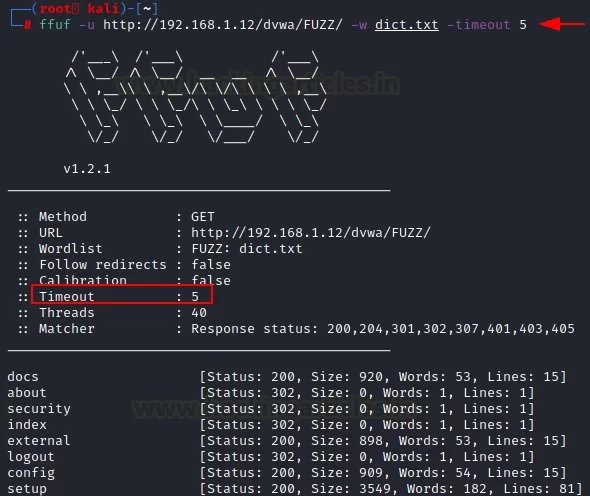
Time-out
This feature acts as a deadline for the event to complete. The “-timeout” parameter helps to activate this option.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -timeout 5
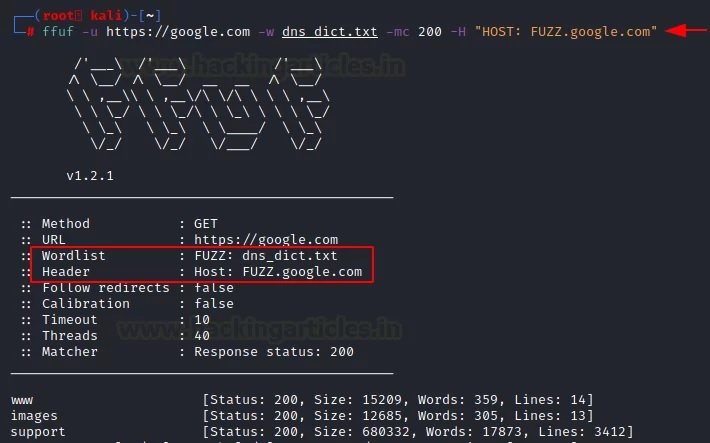
Host header
If you want to fuzz out subdomains, you can use the “-H” parameter along with the word list of the domain name.
Ffuf -u https://google.com -w dns_dict.txt -mc 200 -H “HOST: FUZZ.google.com”
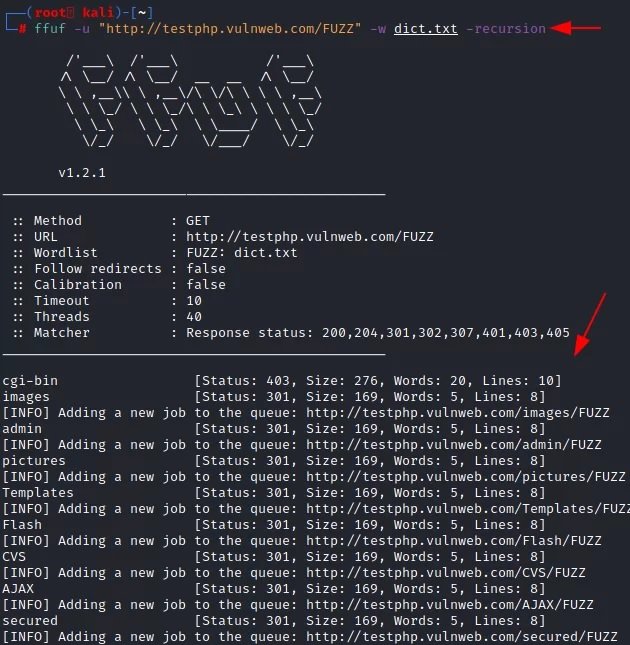
Recursion
According to the experts of the Cyber Security 360 course, this is a mechanism for reusing objects; if a program requires the user to access a function within another function, this is called a recursive call to the function. Using the “-recursion” parameter, the user can implement this functionality in their attacks.
ffuf -u "http://testphp.vulnweb.com/FUZZ/" -dict.txt –recursion
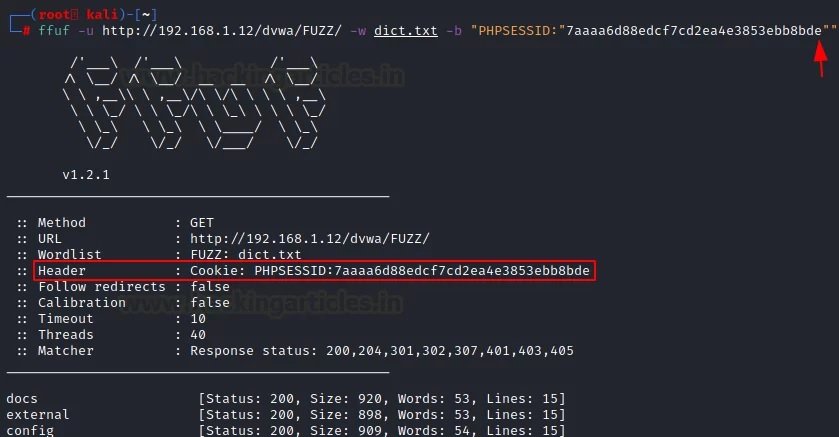
Cookie attack
There are times when fuzzing is not effective on a site where authentication is required. In these cases, we may use the “-b” parameter to use session cookies.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -b "PHPSESSID:"7aaaa6d88edcf7cd2ea4e3853ebb8bde""
Replay-proxy
There are speed limits when using the Intruder feature in the free version of Burp (Community Edition). The attack slowed down a lot, and each new “order” slowed it down even more.
In this case, the user uses the Burp Suite proxy server to get the results and evaluate them. First, you need to install the localhost proxy server on port number 8080.
Now let’s use “-replay-proxy”, which helps to get the local proxy server of the host, installed in the previous step on port number 8080.
ffuf -u http://192.168.1.12/dvwa/FUZZ/ -w dict.txt -replay-proxy http://127.0.0.1:8080 -v -mc 200
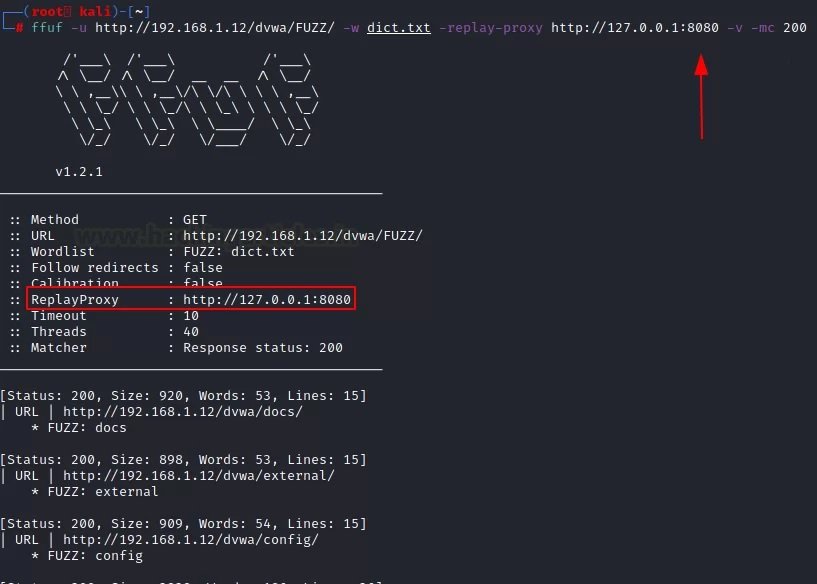
This attack will show results on two platforms. The first platform is in the Kali Linux terminal and the second is in the “HTTP history” tab in Burp Suite. With the help of various methods, you will be able to better understand the target and analyze the results of the attack.
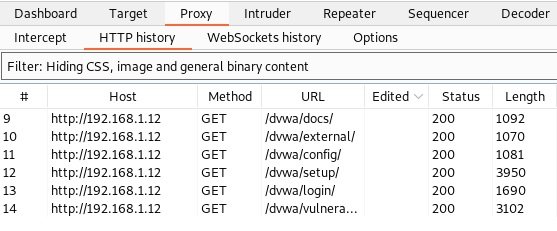
It is common to compare ffuf with other tools such as dirb or dirbuster. While ffuf can be used for deploying brute-force attacks, its real appeal lies in simplicity.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, information technologies, and to know more details about the Cyber Security 360 course.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










