BlackBerry ThreatVector researchers detailed the detection of a new malware strain for Linux systems capable of living at the expense of compromised system resources. Dubbed Symbiote, experts say that this strain is highly sophisticated and has a parasitic behavior never seen before, advancing by leaps and bounds throughout Latin America.
The main feature of Symbiote is that it requires infecting other running processes to achieve a successful engagement. Instead of using an executable as any conventional malware variant would, hackers use a shared object (SO) library loaded into running processes through LD_PRELOAD, thus infecting vulnerable systems.
After infecting running processes on the system, Symbiote provides its operators with rootkit functionalities, in addition to remote access and credential collection capabilities.
Origins
Researchers first detected the malware in November 2021, attributing its development to hacking groups against the financial sector in Latin America. By infecting a target system, Symbiote hides any hint of malicious activity, making infections virtually undetectable, even using forensic analysis techniques.
In addition to rootkit tactics, the malware also implants a backdoor in the system so that operators can log in like any user using an encrypted password and thus execute commands with high privileges.
Another interesting feature about Symbiote is its Berkely Packet Filter (BPF) hook functionality, employed by other malware variants to cover up your C&C communications. However, Symbiote uses BPF to hide malicious network traffic on infected systems.
If an administrator launches any packet capture tool on the affected Linux system, the BPF bytecode is injected into the kernel that defines which packets should be captured. In this process, Symbiote first adds its bytecode so that it can filter the network traffic it wants to hide.
Evasion tactics
This malware is highly stealthy. According to experts, Symbiote is designed to be loaded through the LD_PRELOAD directive, allowing it to be loaded before any other shared object. Thanks to it loading first, it can hijack imports from other library files uploaded for the application.
Symbiote uses this to hide its presence on the machine by connecting the libc and libpcap functions. The following screenshot shows the various malware evasion tactics:
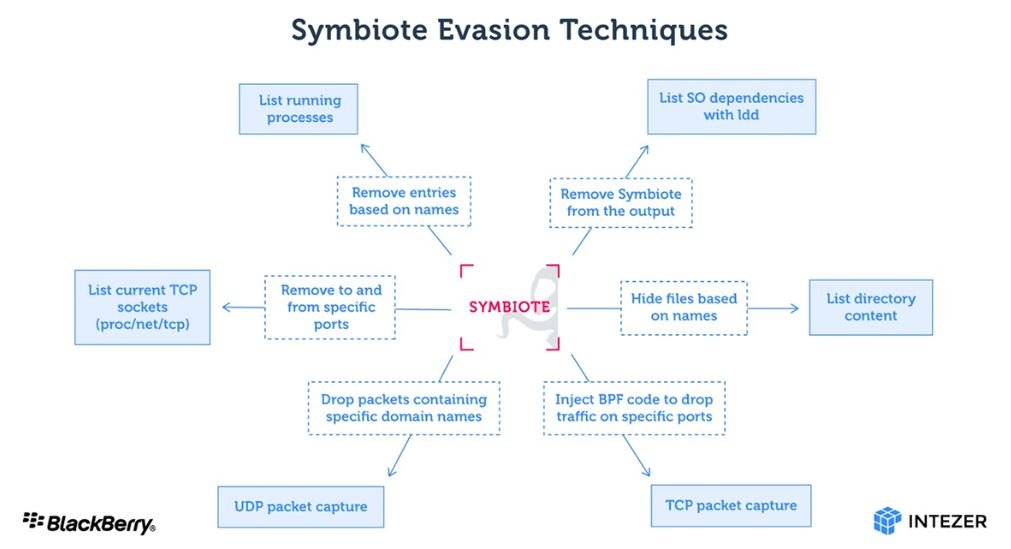
Because Symbiote works as a user-level rootkit, it can be difficult to detect an infection. Network telemetry can be used to detect anomalous DNS requests, and security tools such as antivirus must be statically linked to ensure that they are not “infected” by user rootkits. Infection vectors are still unknown, so Linux system administrators should remain vigilant for any hint of infection.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











